Flow of What I Did
Open Microsoft Edge → Go to gmail.com → Login into gmail → Download attachment (Microsoft Word) → Open attachment
Looking into Process Sequence
Command to tail docker logs:
sudo docker logs -f orientdb --tail 20Looking at the logs in real time, there were two lines that were related to what I was doing:
- System > smss.exe > smss.exe > winlogon.exe > userinit.exe > explorer.exe > msedge.exe > msedge.exe
- System > smss.exe > smss.exe > winlogon.exe > userinit.exe > explorer.exe > msedge.exe > wordpad.exe
Through the logs, it tells us the process sequence that led to the creation of msedge.exe and wordpad.exe.
Information about the processes:
smss.exe: Manages the startup of all user sessions in Windows. The operating system's main thread activates the file. "smss.exe" launches processes such as Win32 and WinLogon.
winlogon.exe: Component of Microsoft Windows operating systems that is responsible for handling the secure attention sequence & loading the user profile on logon.
userinit.exe: Responsible for executing logon scripts, reestablishing network connections and then starting Explorer.exe.
explorer.exe: Manages the Graphical Shell component of the Windows operating system including the Taskbar, Start menu, Desktop and File Manager.
msedge.exe: To start Microsoft Edge web browser
wordpad.exe: To start WordPad
Except for msedge.exe & wordpad.exe, the other processes are all files of Microsoft Windows. Hence, this process sequence chain can be considered as normal.
Process Visualisation
We can also use OrientDB to better visualize the logs and to gather more information:
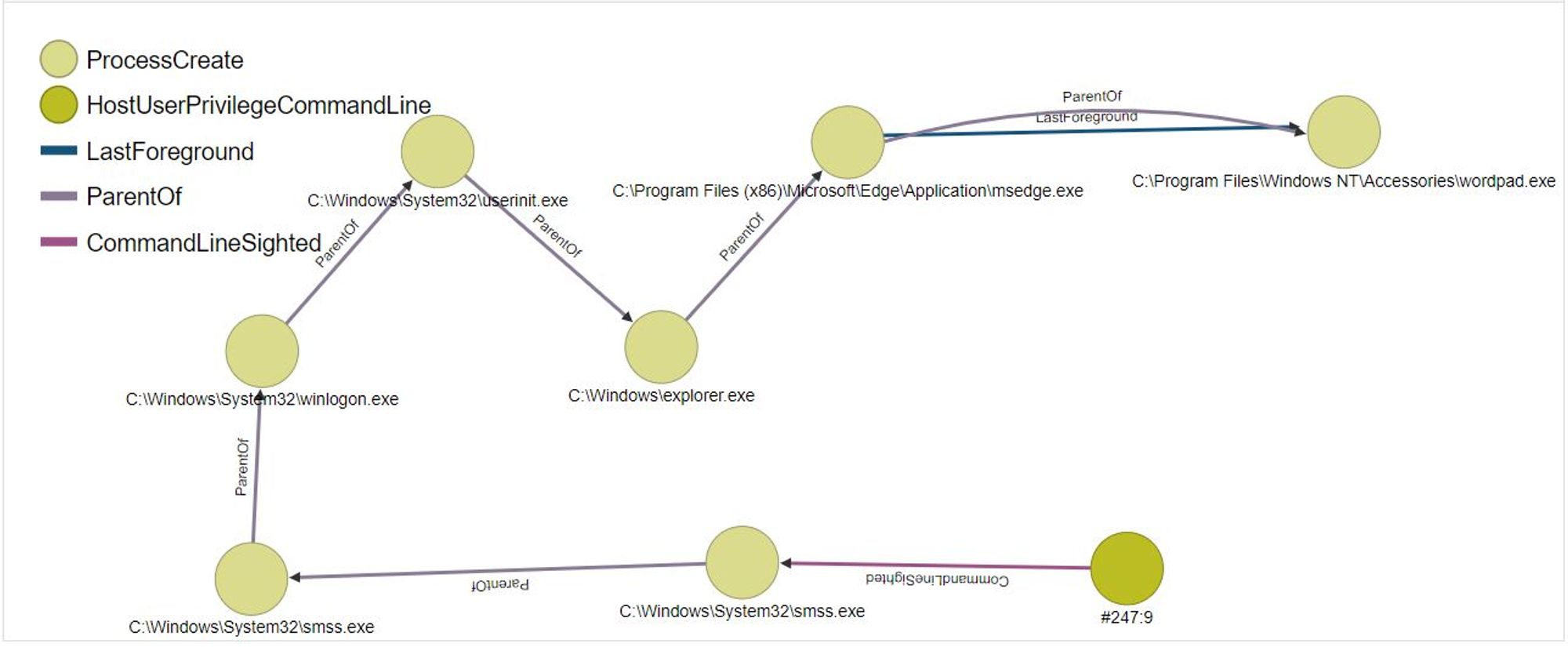
Extensive information e.g. Image, ParentImage, CommandLine, ParentCommandLine etc for each process can be found by selecting the node. For example, in the case of wordpad.exe, the CommandLine used was:
"C:\Program Files\Windows NT\Accessories\WORDPAD.EXE" "C:\Users\User\Downloads\email (1).docx"
This tells us that the docx file was opened using wordpad.exe.
Now that we know the normal process sequence of when a user opens a docx attachment using email, deviations from this normal process could indicate a red flag e.g. if WordPad.exe created a child process when we did not do anything in WordPad.
