Attack Life Cycle
Attackers RINSE & repeat
For a successful attack, all three conditions depicted by the triangles must be met.️
- A target is worthwhile when it has Value & Vulnerabilities.
- Threat Actors need to reach the target's Attack Surface (the sum of all means) to exploit those vulnerabilities.
- Attackers need tools, techniques & resources to mount an attack.
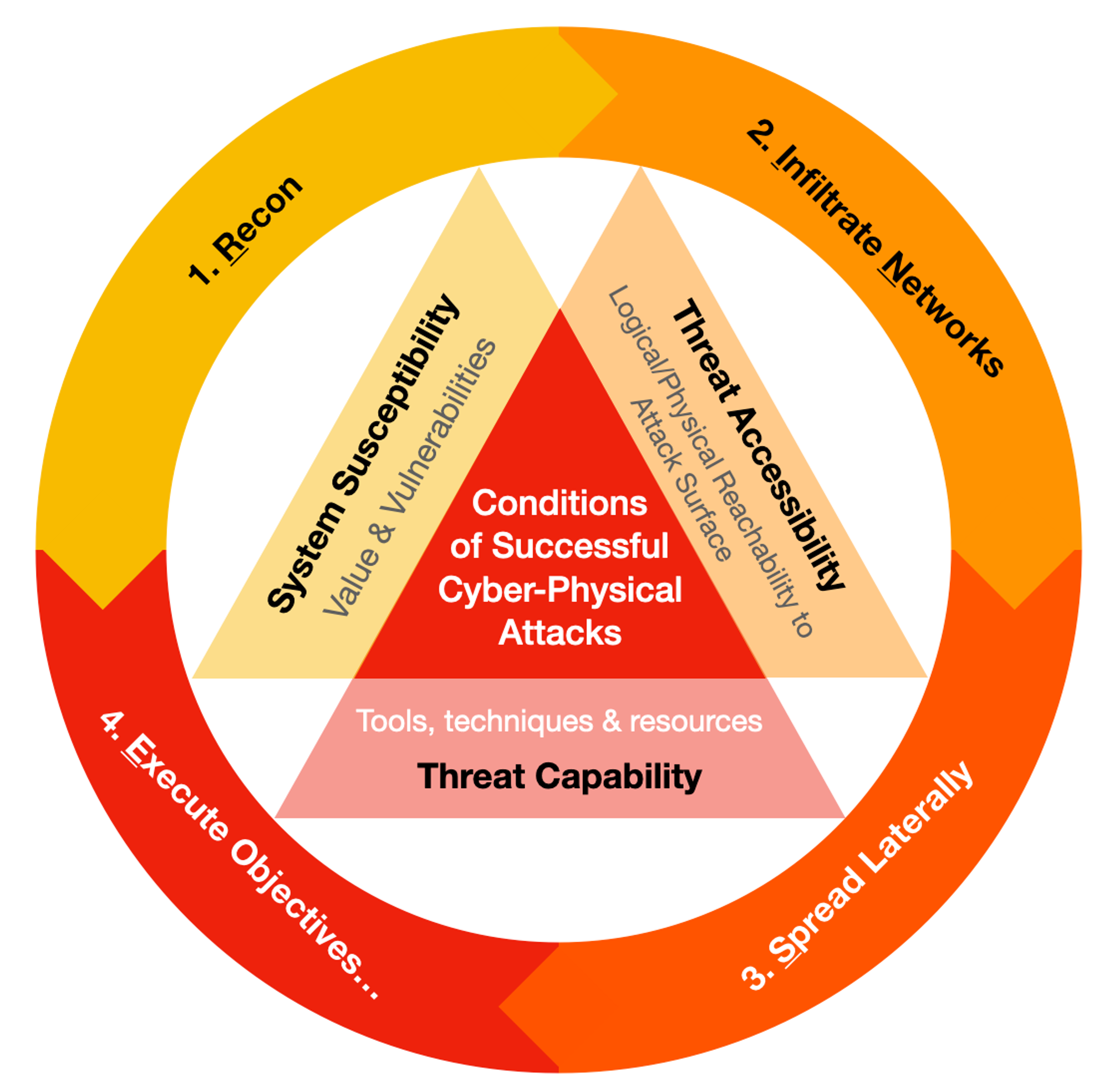
To meet these conditions, attackers need to perform:
- Reconnaissance - Gather information to assess
Value & Vulnerabilitiesthat compound toSystem Susceptibility - Infiltrate Networks -
Threat Accessibilityrefers to the reachable means (Attack Surface) to get into target networks - Spread Laterally - Stay within target networks undetected depends on
Threat Capabilitywhich requires tools, techniques & resources - Execute Objectives - to steal information which impacts Confidentiality, tamper with system & data Integrity & deny Availability of data & networks. For critical Cyber Physical systems, it can threaten Safety & lives.
To effectively counteract potential attacks, identifying and disrupting the appropriate conditions is crucial. However, determining which conditions to prioritise can be a complex decision.
Big Picture
This model provides relationships between defensive concepts & considerations with offensive phases:
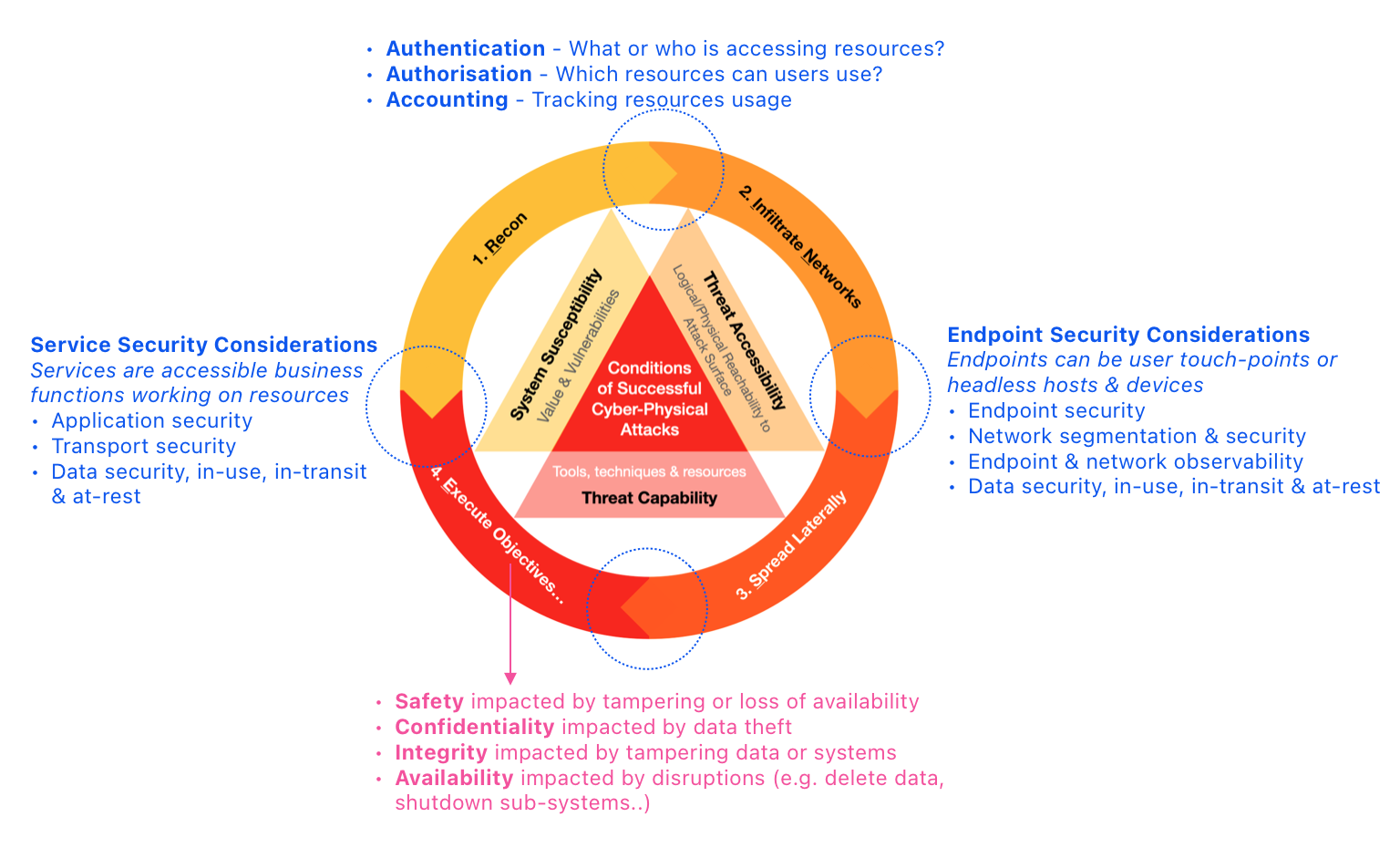
First, we examine the process from the standpoint of an adversary.️
Direct vs Indirect Access
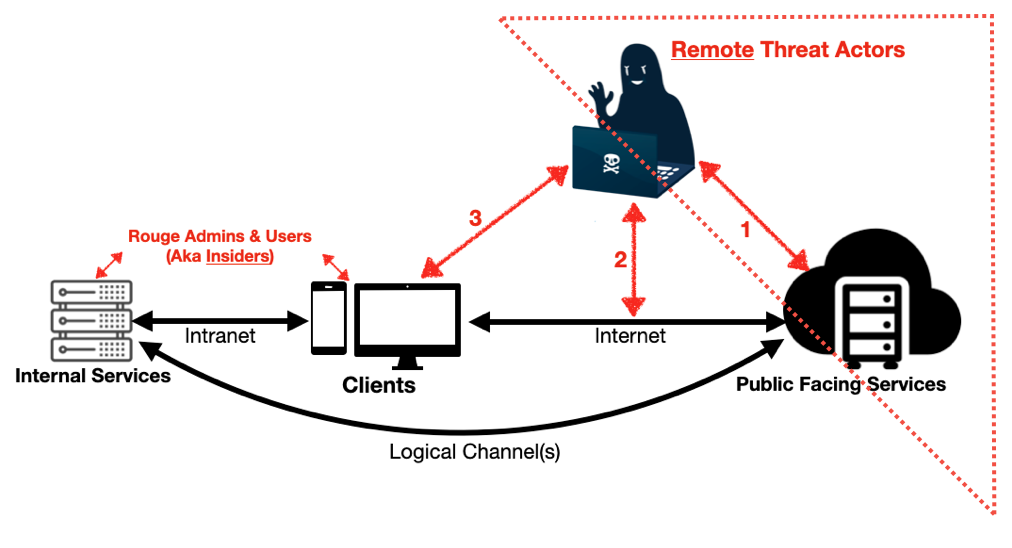 Examples of direct access from
Examples of direct access from 1.Recon to 4.Execute Objectives: Poor web-server configuration leads to exposure of unprotected sensitive files that can be downloaded by anyone, or network routers with default passwords & ports exposed to the Internet. Low hanging fruits for adversaries!*
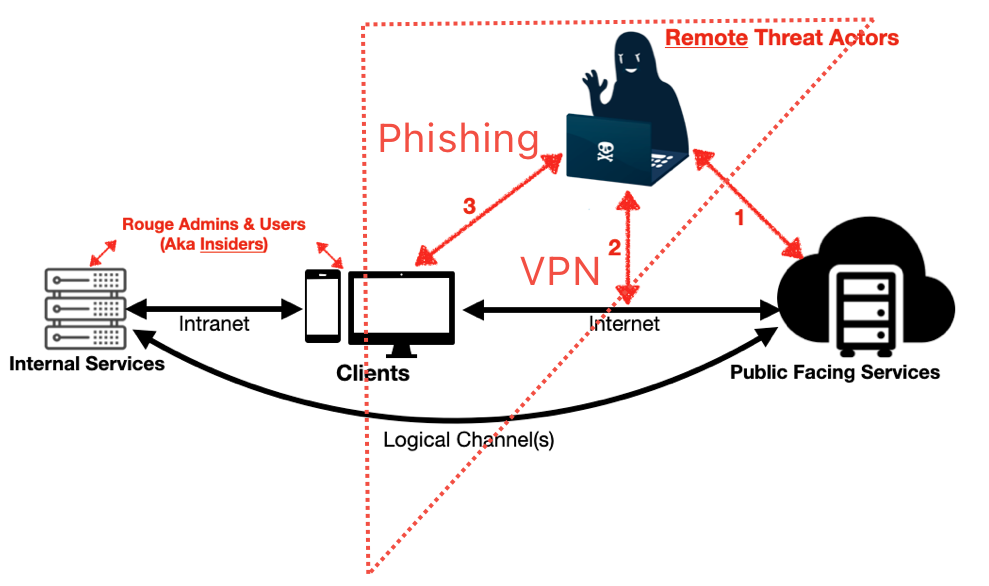 From
From 1.Recon to 2.Infiltrate Networks: Attackers use LinkedIn to figure out who are the HR executives (Information Gathering), send deceptive emails to lure them (Phishing) to click on malicious links or execute malware.
Just need one employee to give attackers that chance to gain control over a HR asset when the malware infects like a Patient Zero & persists within that endpoint. Why go through all that trouble when attackers can buy access into corporate Virtual Private Network?
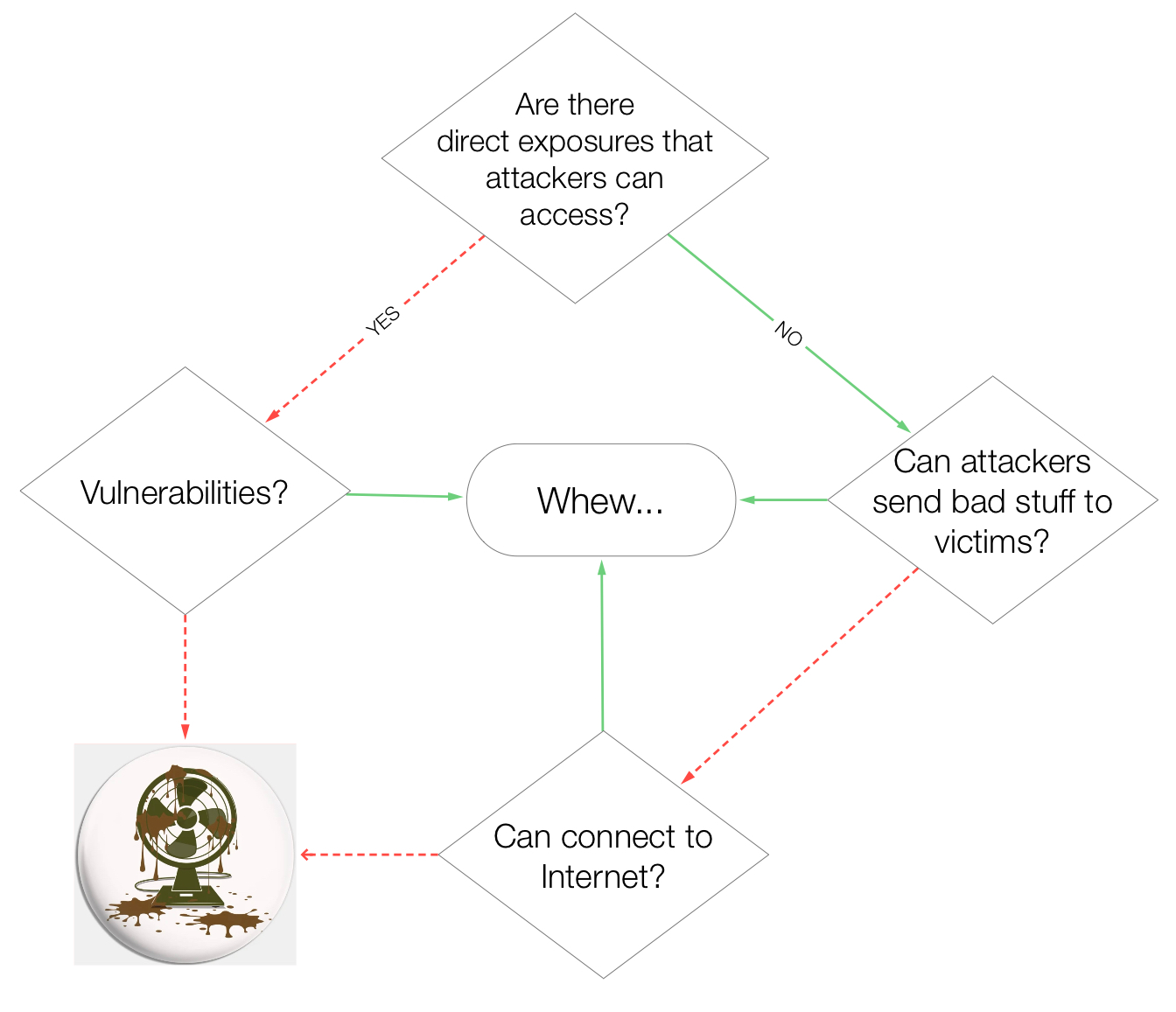
The flow chart covers both direct & indirect access. The attackers have the skills to carry out intrusions from either way. Internet gives them the access to reach vulnerable assets & victims, otherwise attackers need to be physically present or near targets.
Attacks are effective only when all conditions are fulfilled, yet it will fail if any single condition is disrupted. For instance, when employees are vigilant, they report the phishing emails. With Multi-Factor VPN authentication, 1st factor of ID & password sold on dark web is less threatening.
Disrupt Attacks by Design
Instead of reacting to yet another vulnerability announcement, another patching exercise (e.g. Microsoft Patch Tuesday) or worst, automatic updates that disrupted millions of Windows hosts.
The majority are either oblivious or disbelieving of the fact that they can be under attack, or aware but stuck in a Chase-After-Bad posture, which is unending & costly.

My interns (unaware but curious) learnt about Threat Accessibility & managing privileged administrator access through this lesson plan:
- Sign up a free cloud Linux server.
- Start the virtual Linux server & use a strong password.
- Configure audit log to review authentication attempts.
- Start monitoring audit events.
- They will notice that within a short while, many failed secure shell or SSH attempts will start appearing in that console session earlier.
Weak passwords used for remote root access in Linux systems increase the risk of successful brute-force login attacks.️
- I directed them to some free Virtual Private Networks like ZeroTier & Twingate.
- The students reconfigured their servers to only accept connections from the same private network.
- NO MORE brute-force attempts. Even if the passwords were weak, attackers cannot reach those servers to test it.
Designing with Threat Accessibility in mind enables us to disrupt attacks effectively while maintaining both usability and security.️
What about the other two attack conditions; System Susceptibility & Threat Capabilities ?
They are part of the unending Chase-After-Bad posture!
Getting rid of vulnerabilities by patching is an impossible task.
- Vulnerabilities is not limited to software bugs, but include poorly designed features that can be abused.
- Even if hypothetically Windows were free of bugs, there are numerous system tools & mechanisms susceptible to misuse by attackers.
- All complex operating systems, including Linux, MacOS & mobile ones have such vulnerabilities.️
- I'm not suggesting "don't need to patch", but we have to exercise caution and careful consideration before implementing any changes to production systems.️
Threat actors are extremely motivated, creative & resourceful. They often use free or cheap tools to evade costly controls & monitoring operations at a fraction of the cost!

Avoid Single-Factor Authentication
Single-factor authentication refers to the process of verifying identity through the use of one identifier, such as an email address or username, coupled with a password.️
Upon obtaining these credentials, there is a significant risk that password reuse will grant Threat Actors access to other services for affected users.️
We can disrupt such unauthorised access with either Multi-Factor authentication or replacing passwords with passkeys.
Negligence like default passwords (e.g. exposed database) or worse, total lack of access control becomes low hanging fruits for attacks to reach objectives directly from Phase 1 to 4.
Avoid Admin Ports Exposure
Admin access through ports like SSH, RDP, VNC should never be exposed over the Internet. Even web admin pages should be limited to a small set of fixed Internet Protocol addresses whenever possible.
There are many freemium software private networks like ZeroTier, Twingate, Tailscale & the likes to limit access. Instead of using public Internet address, simply configure such remote admin services to use private network address accessible to a few admin endpoints, just like what my interns did.
Reduce the need for Signature-based Controls
The Crowdstrike Channel File incident is a prime example of Signature-based control. Updates are needed to counter whatever new offensive techniques.
Due to the ever-evolving nature of offensive tactics & techniques, continuous updating of signatures became the unfortunate norm to keep pace with new threats.️ But malware & offensive techniques are part of an infinite set, such reactive or Tit-for-Tat controls controls will never keep up.
More examples of Signature-based Tit-for-Tat Controls (non-exhaustive) :
- Anti-virus
- Web App Firewall
- Network Intrusion Detection
Encryption facilitates evasion for malware. Malicious network traffic can be obscured through encryption, with a significant proportion of Internet communications encrypted.️
Apply Design Thinking & ALC
Now that you have some idea of the pitfalls to avoid, we are ready to use this scenario of a tech refresh for a hypothetical law firm, to come up with a more usable & secure network, by applying Design Thinking & Attack Life Cycle mental model.
Recap
- Attackers will RINSE & repeat within this Attack Life Cycle.
- They can attack directly at services or indirectly, by getting into target networks & work their way within to meet their offensive objectives (steal, tamper & deny access to data or systems).
- Although cyber attacks seem like a very complex topic, there are only three conditions necessary for any successful attacks.
- It is sufficient to disrupt attack by dealing with any one of the conditions, but keeping up with system vulnerabilities by patching, paying for more controls to address ever changing offensive techniques is unsustainable.
- We can disrupt attacks by design to make systems usable & accessible to legitimate users but much harder & costly for attackers, instead of just reacting to system vulnerabilities & threat techniques.
- A concrete scenario was used to illustrate how it can be done.
Once you have a high-level view of attack as a life cycle & the necessary conditions, it's time to dive deeper into Tactics Techniques & Procedures.