This entry is not meant to be a boring textbook rip-off, but rather provides quick understanding of what matters without feeling sleepy from text-walls.
What is Risk?
In the context of Cyber Security, our concern is the probability of a negative outcome.
Cyber vs Information Security
Cyber-Physical systems, often shortened to Cyber, refer to complex networks that include hardware, software, and potentially other types of systems. An example would be train systems, which control moving trains carrying passengers or goods and manage various station operations.
In the context of Information Systems, we are concerned with the loss of data in terms of Availability, which is affected by Denial-of-Service attacks, Integrity, which involves data being tampered with, and Confidentiality, which relates to data being stolen.

However, for Cyber-Physical systems, attacks can compromise safety and even result in fatalities! For instance, ransomware incidents affecting hospitals!
How Bad (Impact) vs How Likely (Probability)
Risk Assessment is to capture Risk Exposure into lists for follow-up actions.
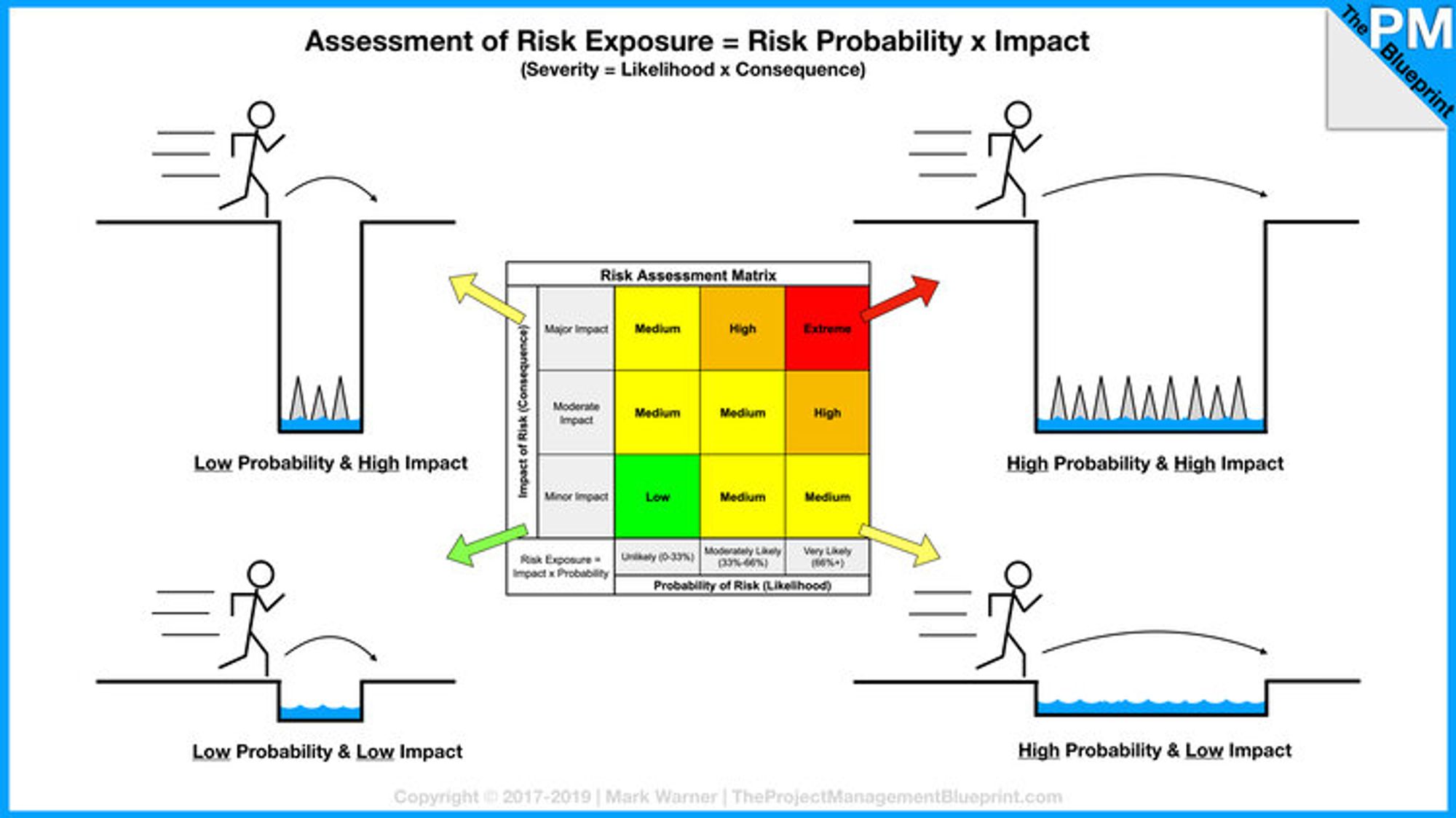
Image credit to https://www.theprojectmanagementblueprint.com/blog/risk-management/risk-exposure-equals-probability-times-impact
With limited resources, we need to prioritise the High Probability & High Impact scenarios.
Poor Security Posture → Easy Attacks
Unlike stick mans jumping over gaps, attacks happen often due to the lack of (or ineffective) Cyber Security controls (or measures).
After assessment, we need to follow-up with measures (aka controls) that make it harder for attackers.
A poor security posture refers to the lack of sufficient measures to mitigate risks, including users' risky behaviors.
It may not necessarily be that attackers are highly skilled, but rather that many networks are too vulnerable! This brings us to the next topic, the conditions of attacks, which explains Why are attacks prevalent?.
The probability of attacks is HIGH when all conditions are met!
