Flow of What I did
Open Skype.exe → Login → Download attachment (text document) → View attachment → Close attachment
Looking into Process Sequence in OrientDB Console:
Command to tail docker logs:
sudo docker logs -f orientdb --tail 20Looking at the logs in real time, there were two lines that were related to what I was doing:
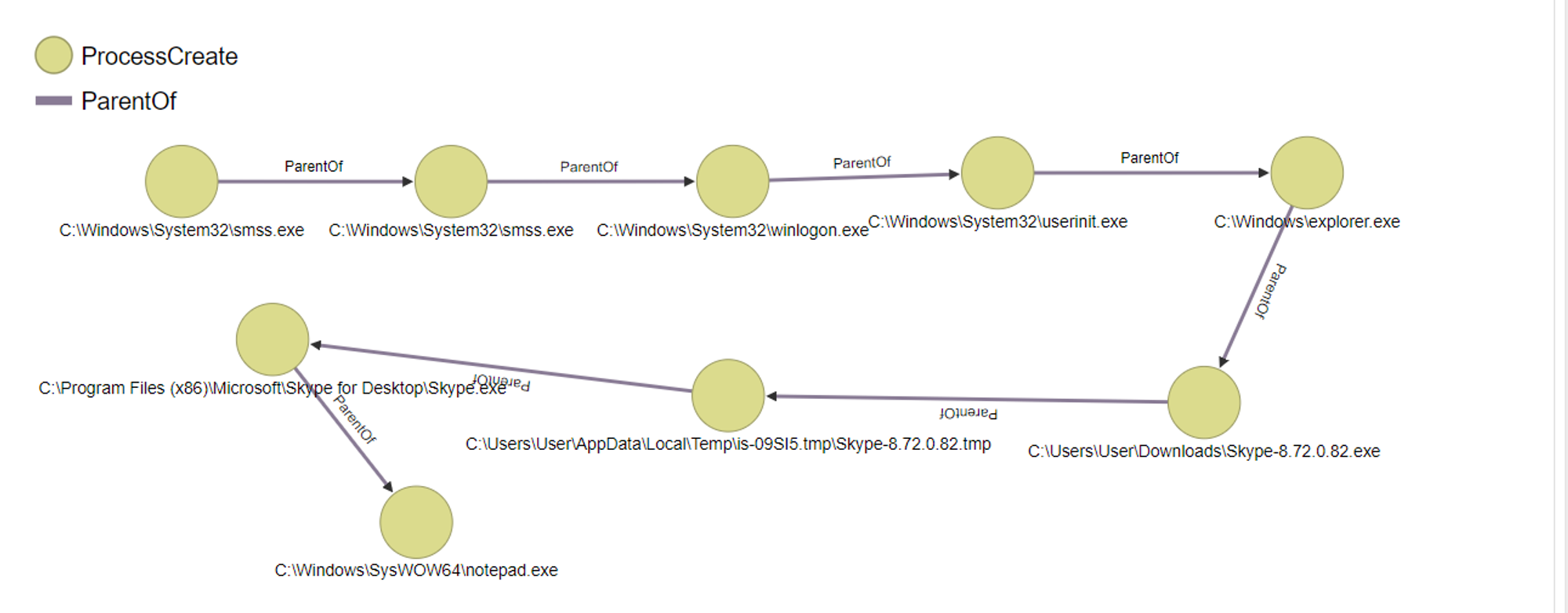
- System > smss.exe > smss.exe > winlogon.exe > userinit.exe > explorer.exe > Skype-8.72.0.82.exe > Skype-8.72.0.82.tmp > Skype.exe
- System > smss.exe > smss.exe > winlogon.exe > userinit.exe > explorer.exe > Skype-8.72.0.82.exe > Skype-8.72.0.82.tmp > Skype.exe > notepad.exe
The first bullet point is when I opened Skype while the second bullet point is when I opened the text document in Skype.
Looking into Process Sequence in OrientDB Graph:
Process sequence lineage visualization in OrientDB:
Diving deeper into notepad.exe:
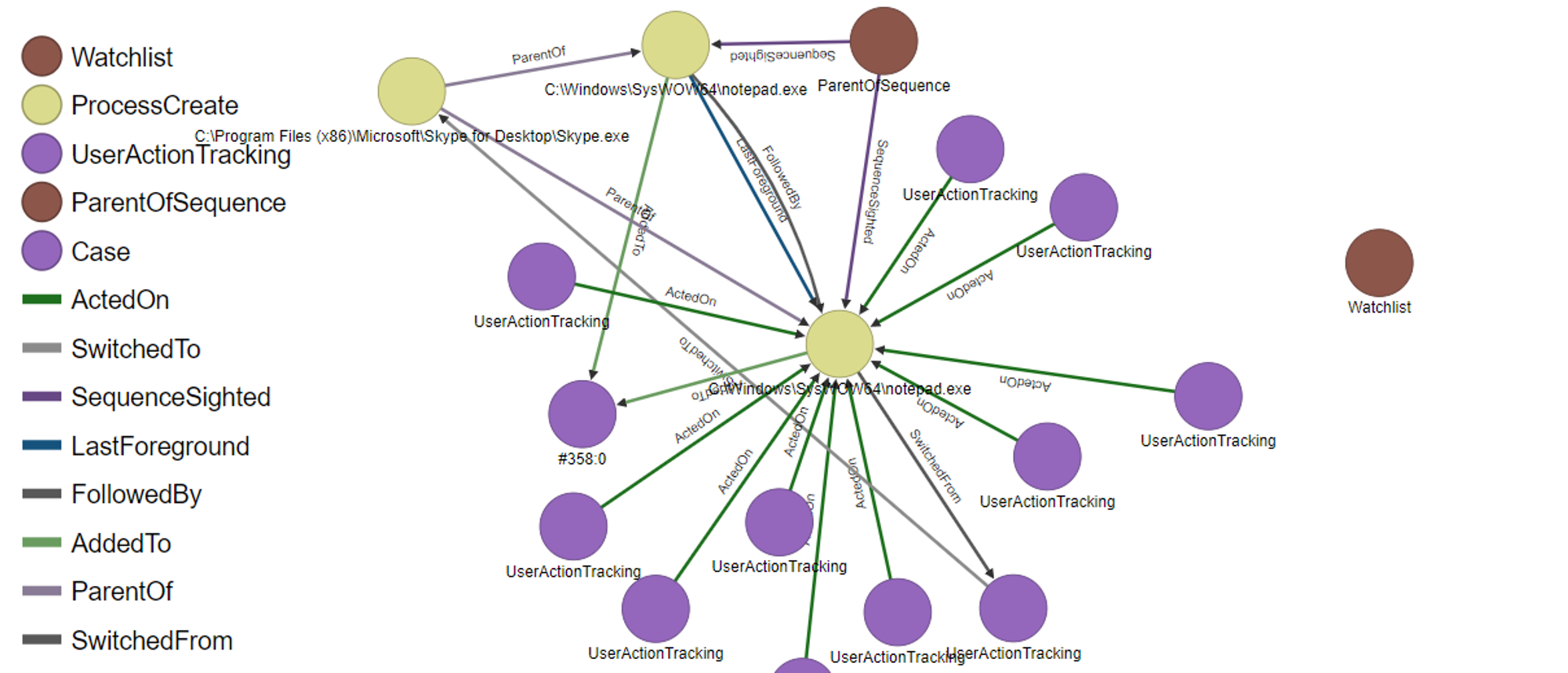
A lot of nodes/edges just from one notepad.exe. Let's look into what the nodes/edges means:
Watchlist: Placed in watchlist because of unusual process sequence (related to Wekan frontend, explanation in Wekan section below), needs to be investigated
ActedOn: Tracks the user action that was done on notepad.exe e.g. Left click to open notepad
SwitchedFrom/SwitchedTo: Foreground transition between notepad.exe and skype.exe (notepad.exe switched to skype.exe, because I closed the notepad)
SequenceSighted: Same process sequence found in ProcessCreation
LastForeground: Last foreground process in the sequence
FollowedBy: Timed-order presentation of the process
AddedTo: Process was added to a case, likely means needs to be investigated
ParentOf: A child process was created from a parent process i.e. Skype.exe is a ParentOf notepad.exe
Looking into Process Sequence in Wekan
Looking at Wekan front-end, I noticed that the process creation of notepad.exe was labelled with the tag "Unusual Process Sequence".
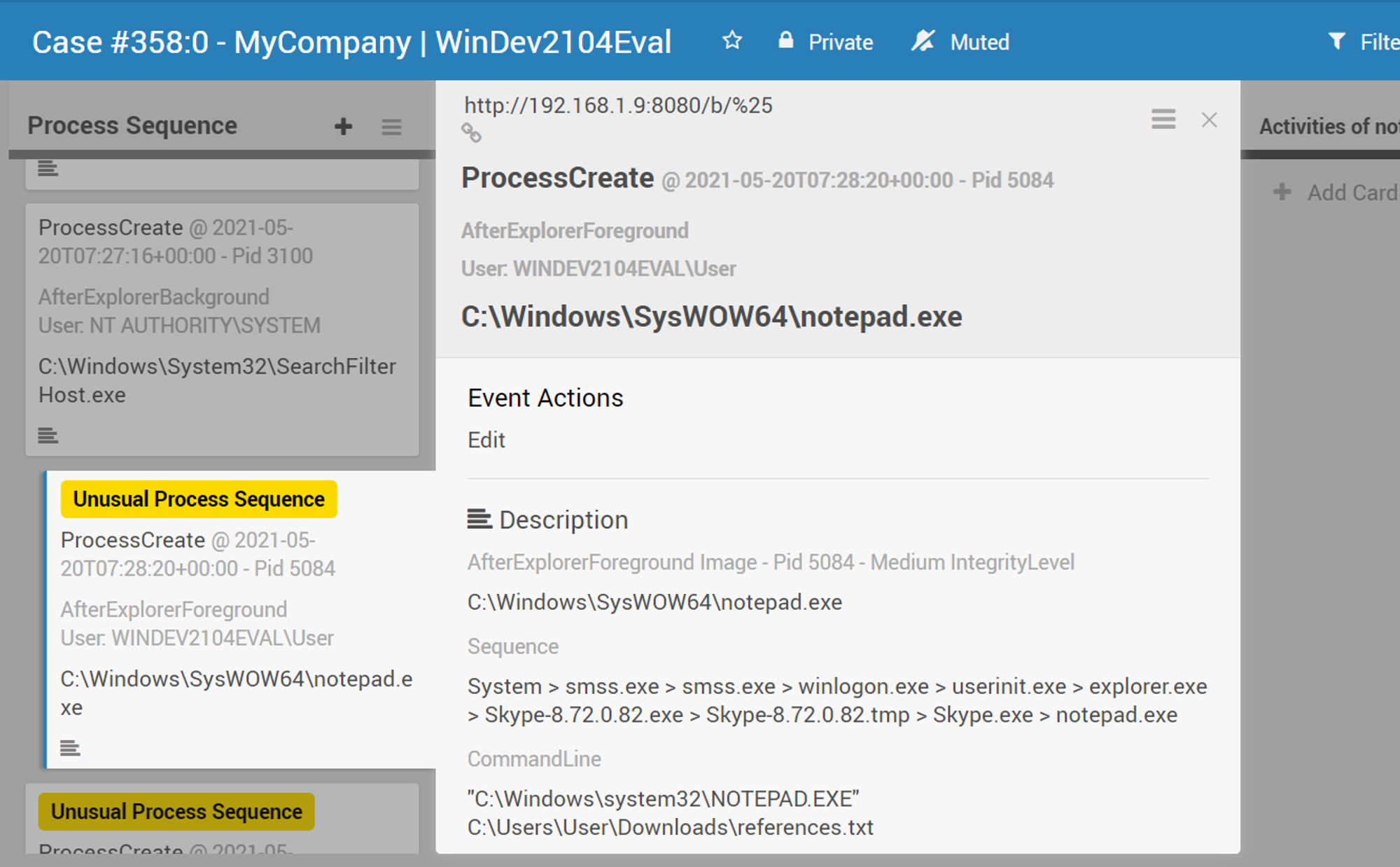
This is because of the uncommon sequence that lead to the creation of notepad.exe. The usual/normal process sequence would likely be System > smss.exe > ... > explorer.exe > notepad.exe. However, because I downloaded and opened the file from Skype, it resulted in this unusual/out of the ordinary process sequence (explorer.exe > Skype.exe > Skype.tmp > Skype.exe > notepad.exe). Hence, notepad.exe got flagged out by OpenEDR. For such cases, we would need to further investigate to determine if the process is benign or malicious. If no network communication was made i.e. External & Internal Network Activities list are empty and no activities was done by the process i.e. Activities of .exe list is empty, then it likely means that it is a benign process.
FileCreate
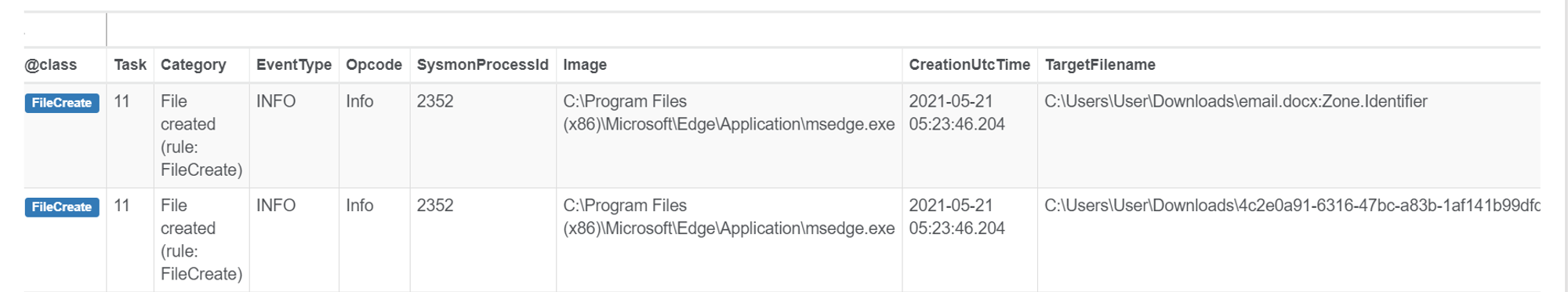
After I logged into gmail and downloaded the docx file, I queried in OrientDB Select From FileCreate where Image like "%msedge.exe%". The two entries that returned shows that the docx file was created from a download in msedge.exe as seen from the parameters Image name and TargetFilename.
Looking at the first entry, I noticed that the TargetFilename contained a ":Zone.Identifier" extension. The text after the colon is an identifier for an "Alternate Data Stream". ADS is used to store meta-information about the file. In this case, the zone identifier stores whether the file was downloaded from the Internet. Zone.Identifier files are generated automatically when a file is downloaded from the Internet.
References:
