w.r.t this goal
- Good scenario because with increasing use of Instant Messaging platform as part of many enterprise collaborative tool-suite.
- This use-case is common since users can receive files & start working on it immediately.
- For that fact it can reach many users, it is a viable vector for spreading payloads beyond the usual email & browser approaches.
- One key area to improve is to show FileCreate or equivalent events
Learning Points for Students
Payload Delivery
- A TXT text file is uncommon for delivery exploits, which is alright since this is a benign use-case investigation. However, we do not preclude the possibility of users receiving "Active-Contents".
- We can argue that a more "centralised" way to mitigate Active Content delivery is through a web-proxy or some kind of network-layer Intrusion-Detection-System but more than often, such controls are easily bypass with trivial steps like embedding within an allowed format.
Profiling vs Detection Mode
Let's say you did NOT switch to Detection mode early, & you ran the same IM use-case flow, of which the sequences will be 'learnt'. If another user in the population were to do the same thing during Detection Mode, there will NOT be alerts. Which leads to the concern, what if during Profiling Mode, we learnt BAD things. For that, I wrote https://github.com/jymcheong/OpenEDR/wiki/2.-Profiling-&-Threat-Hunting
Also, at this juncture it is relevant to share a bit of the background of this OpenEDR, why I designed the way it is today. Our company is into defending Operational Technology & Gov-ICT networks. These networks are not foreign to Application-Control. The endpoints are unlike office-home ones, they don't run such a large set of programs. The kind of alerts that you have seen after quickly switching backend to Profiling Mode can be interpreted by more critical professionals as False Positive.
But people do not realise that for COTS EDR or even UEBA, the profiling processes (or whatever analytics ML, AI & various buzzwords) are largely black-boxes. The amount of computing resources & expertise to get it up are significant. Past few days, you have the luxury to use a type of tooling that I once evaluated with my team. But the difference is, you can have it in your possession & can continue even after this internship ends.
With guidance, you too can add enhancements to the Open-sourced backend, which unlike many COTS vendors, does the reverse, client-side Open-sourced (which to me is a bad idea) but their backend capturing YOUR data to THEIR cloud.
Utility of Fore/Background Attribute
- There are other interesting & possibly useful analytics to explore with this attribute. Eg. Explorer.exe (FG) > Wordpad.exe (FG) > Powershell.exe (BG) ..... eh why your RTF file so special leh?
Sequence vs Structural View of Events
The graph views are good for structural representation. But at some point, you will be thinking or grumbling, need to click so much & arrange them nicely... tedious right? Having evaluated quite a number of EDRs & what not, it seems as if some engineers quit from one company, then run to another one. Or they engaged the same UX consultancy & ended up having similar presentation layers.
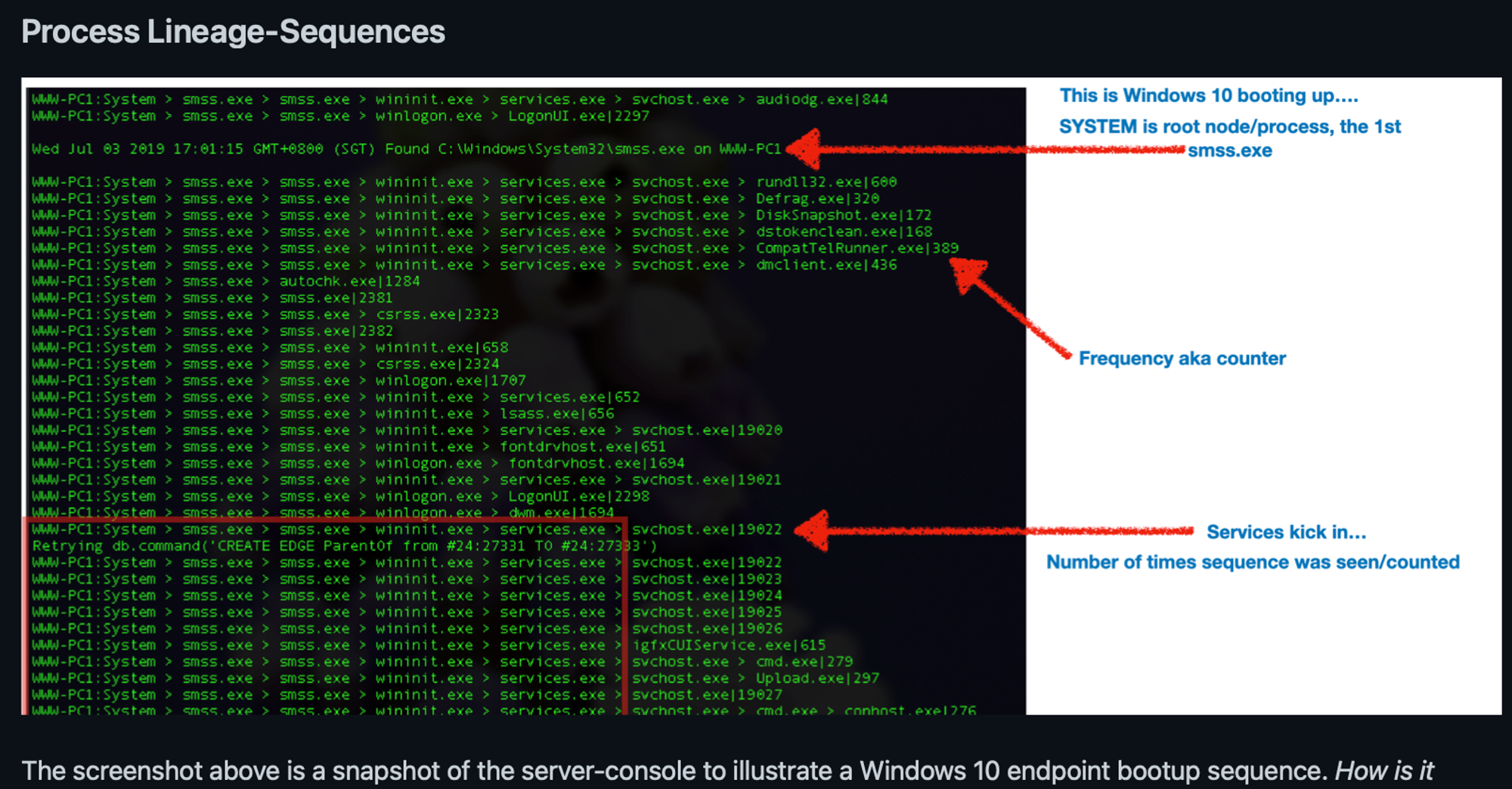
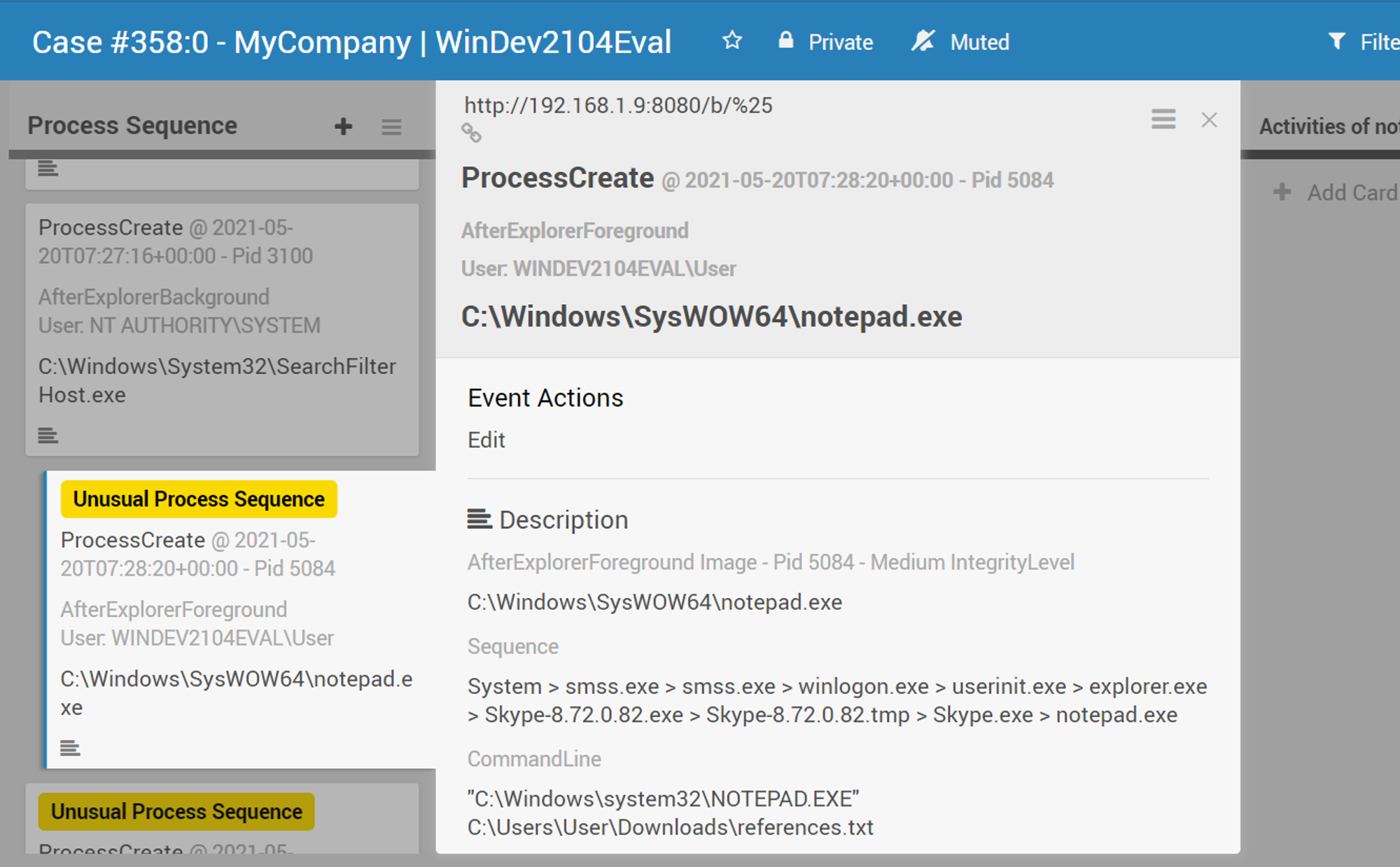
- From left to right, that's Process Lineage.
- From top to down, that's Process Sequence or temporal (time) order.
Obviously we don't want the analysts to stare at this for the whole day considering this example is only 1 host; WWW-PC1, what if there are hundreds of hosts???!
What if something spoofs a EXE name & tries to evade this sequence detection method?
Good question! But you will learn later that such a spoof will need a written EXE file owned by the current user, even if it is a local admin account like what you are about to do. The file won't even have a chance to be launched because it will be denied read via ACL modification upon written.
Not enough Cyber Security staffing..... or are things just too darn complex?
Such that it perpetuates the problem of lack of skilled people?! So back to the earlier UX joke-comment, why on earth do we want to subject a user to click & click just to understand something, on a daily basis !?
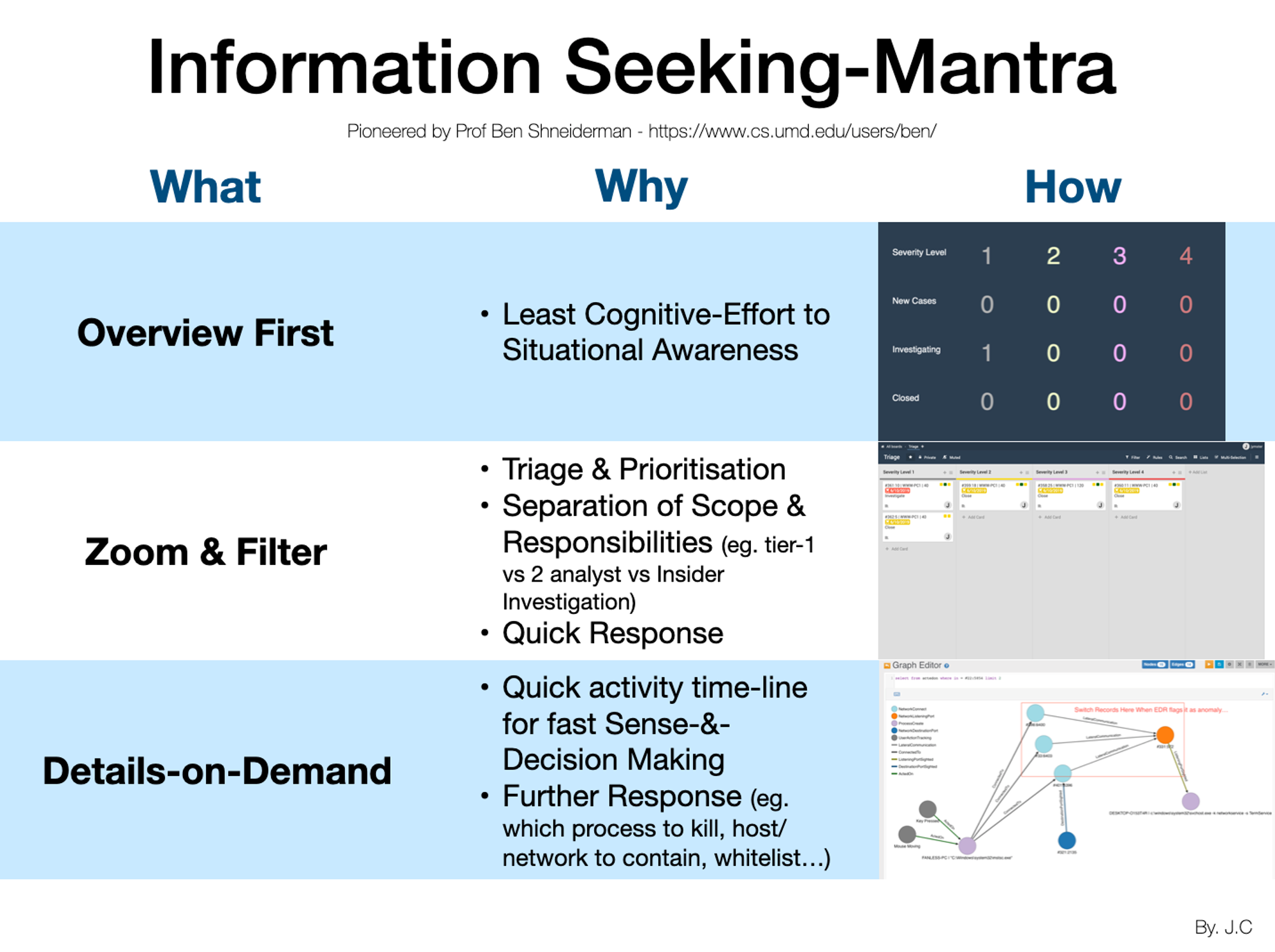
I read the works of Prof Shneiderman & decided, since I am not talented with UI/UX nor do I have the luxury of programmers, I will just reuse Wekan Kanban system & hack it to present alerts!
What you have done is starting from Triage, to Investigation board & all the way into SQL. The last portion is more for senior analysts but now even a 1st year student can do it!