Comparison of ODB console + ProcessCreate attributes:
Both execution resulted in the same process lineage sequence. However, I noticed that there is a spoof found when I ran wordpad.exe as administrator:
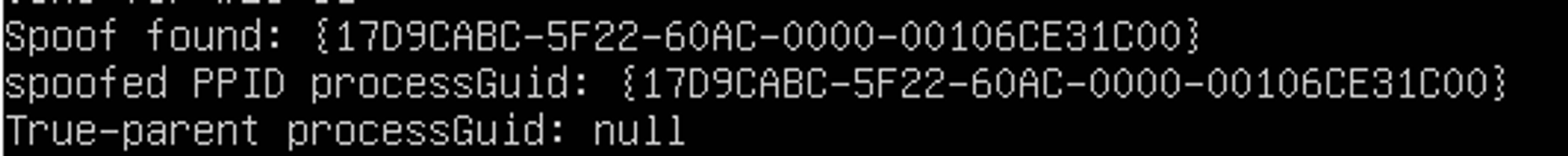
I tried running powershell.exe as administrator and spoofing occurred once again:
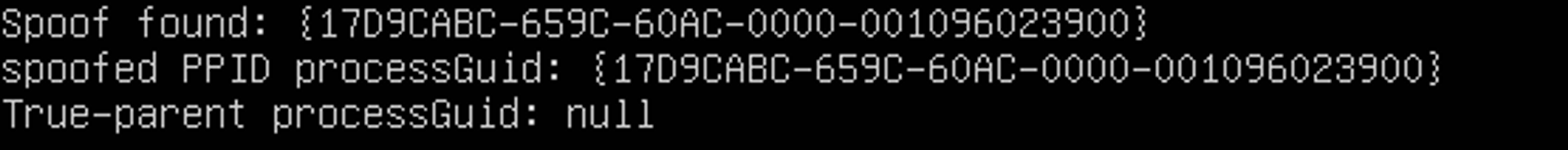
It seems that spoofing occurs whenever we run a process with higher privileges i.e. run as admin.
Debugging
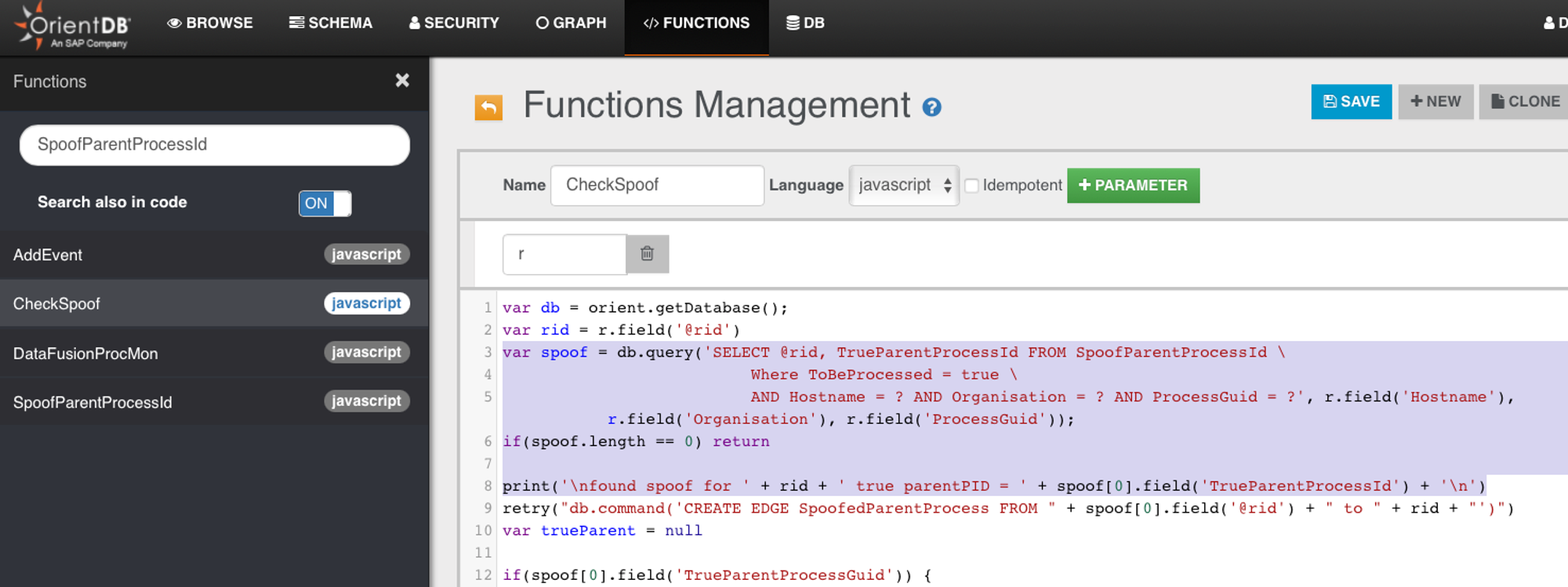
Investigating why there is no TrueParentOf edgesAll ProcessCreate attributes were the same except for the following:
Difference in ProcessCreate attributes
Attribute
Normal
Privileged
Explanation
Medium
High
Each process has an integrity level: Low, Medium, High or System. A process with a lower integrity level cannot write to an object with a higher integrity level. This stops attacks such as dll injection without privilege escalation. By default, non-elevated processes run with medium integrity level, hence why normal execution of wordpad.exe resulted in medium integrity level. On the other hand, privileged execution will result in high integrity level because we ran as administrator.
0x31ca908
0x31ca8e9
This is a unique field for each logon session. Running as normal user and as a adminstrator will result in 2 different LogonId. I attempted opening wordpad.exe again as a normal user and got the same LogonId i.e. 0x31ca908.
{17d9cabc-5749-60ab-0000-002008a91c03}
{17d9cabc-5749-60ab-0000-0020e9a81c03}
Same explanation as LogonId
{17D9CABC-7664-60AB-0000-0010F81BFE03}
{17D9CABC-7611-60AB-0000-001004C9FC03}
Unique for each process
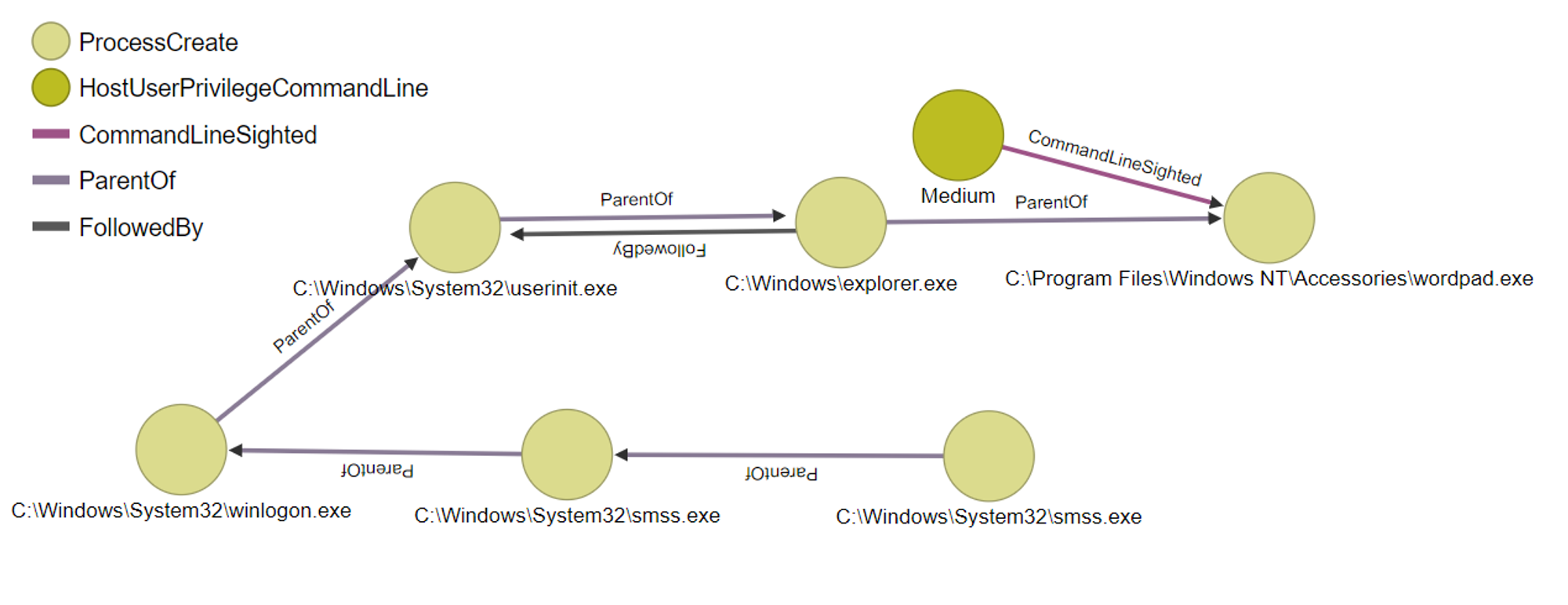
Comparison of OrientDB graph:
Normal execution of wordpad.exe:
Privileged execution of wordpad.exe:
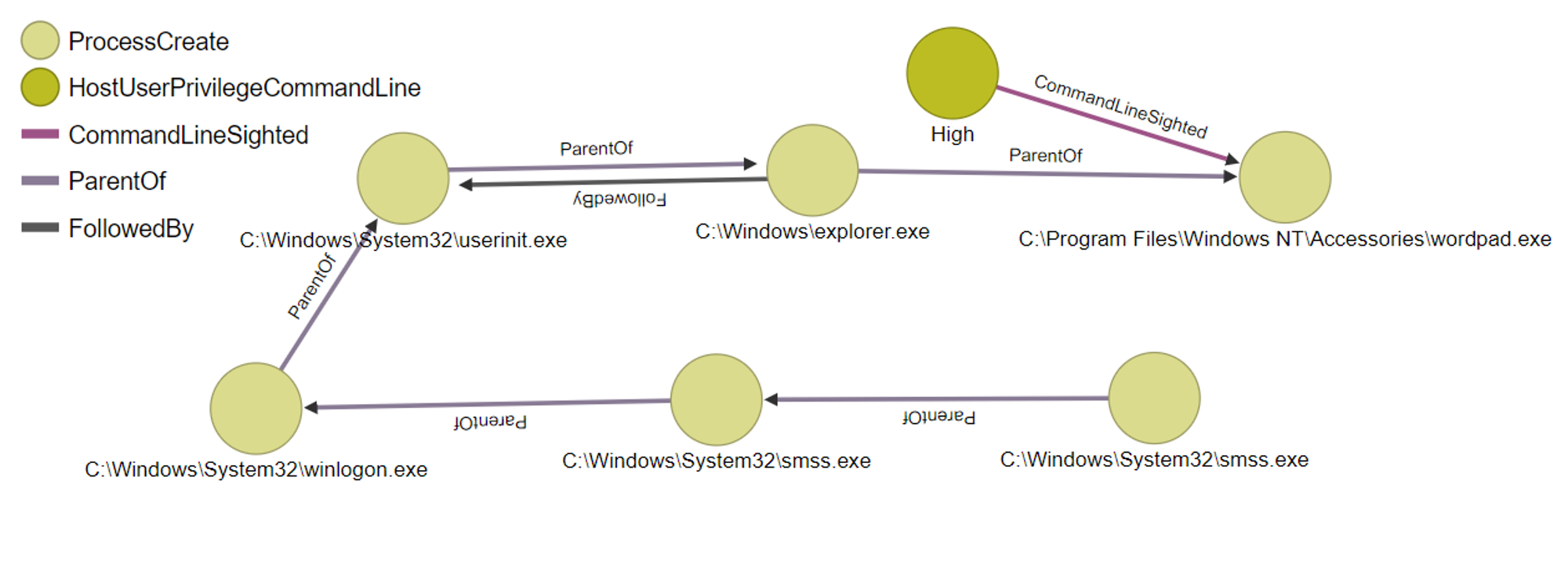
When comparing the graphs, the main difference is the HostUserPrivilegeCommandLine. As mentioned earlier, normal execution has a medium integrity level while privileged execution has a high integrity level.
Jym's Comments
You can select edge-class like so, where CommandLineSighted is an Edge class:
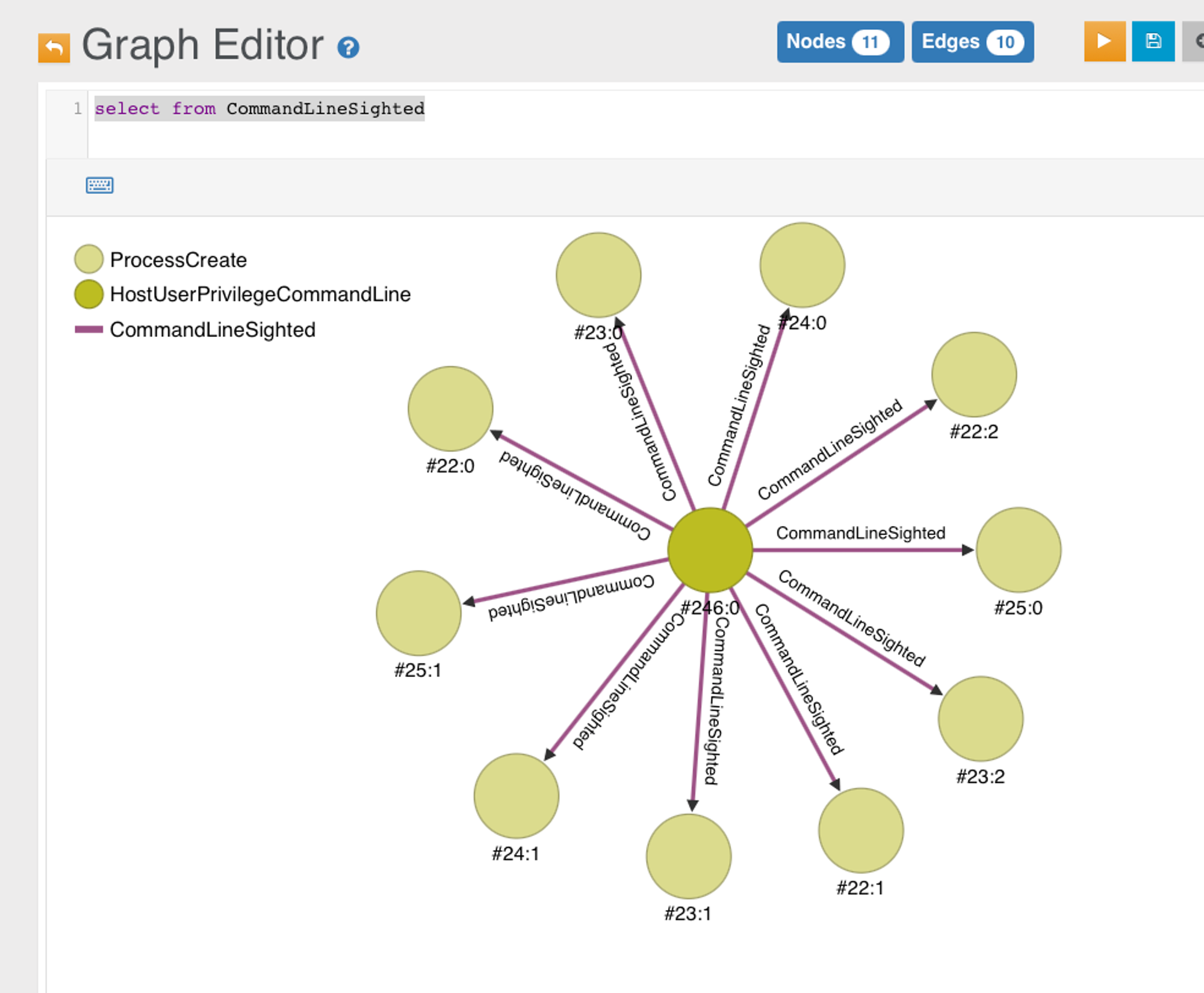
Facts established so far...
May 26, 2021
- Took my kids' laptop which was already installed with OpenEDR (no ProcessTampering Sysmon) & uploaded events to my development backend (those server functions related to this issue were untouched for quite a while)
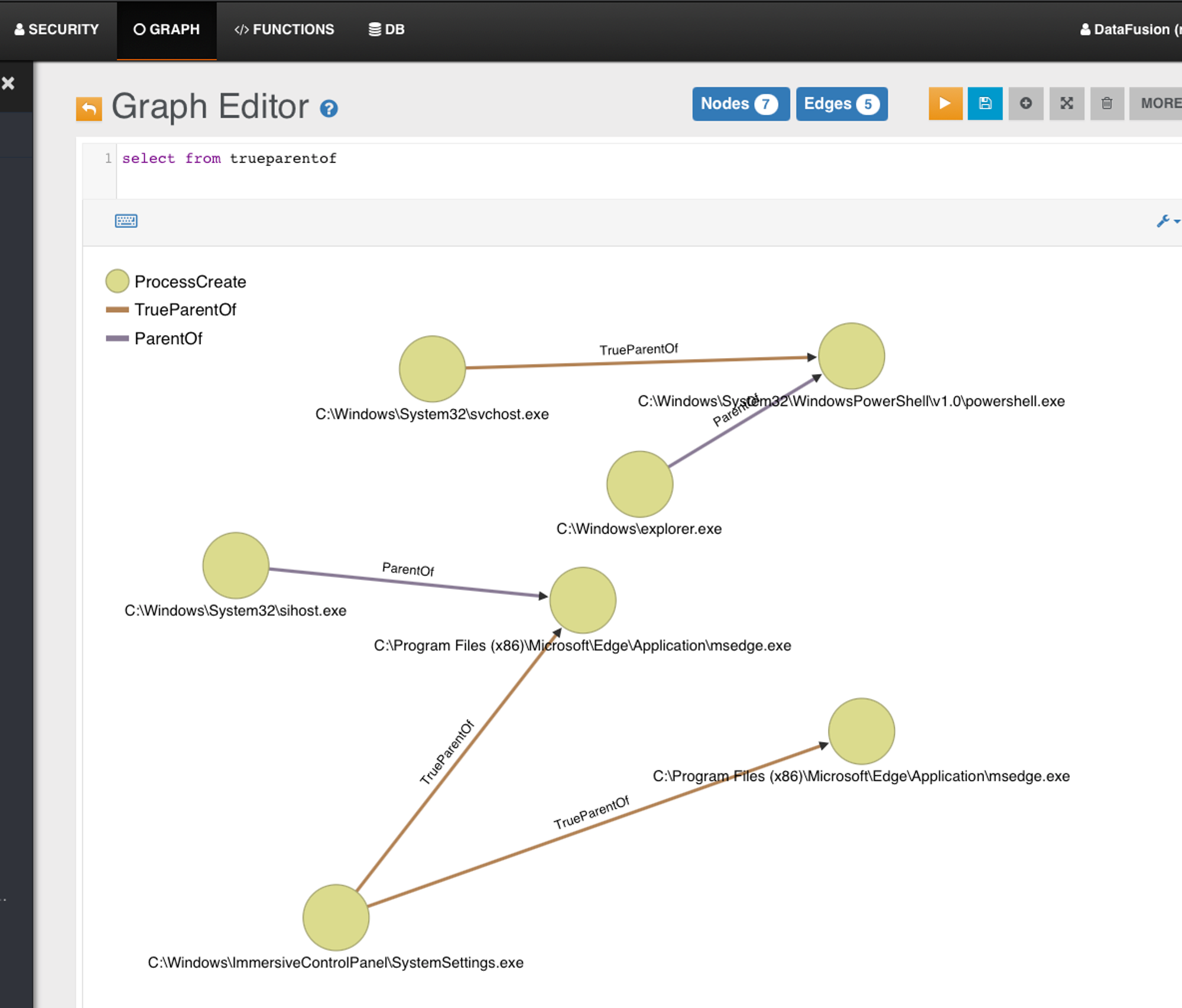
Powershell run-as admin, the ProcessCreate didn't reach backend immediately. I had to type few commands... before events get rotated out...
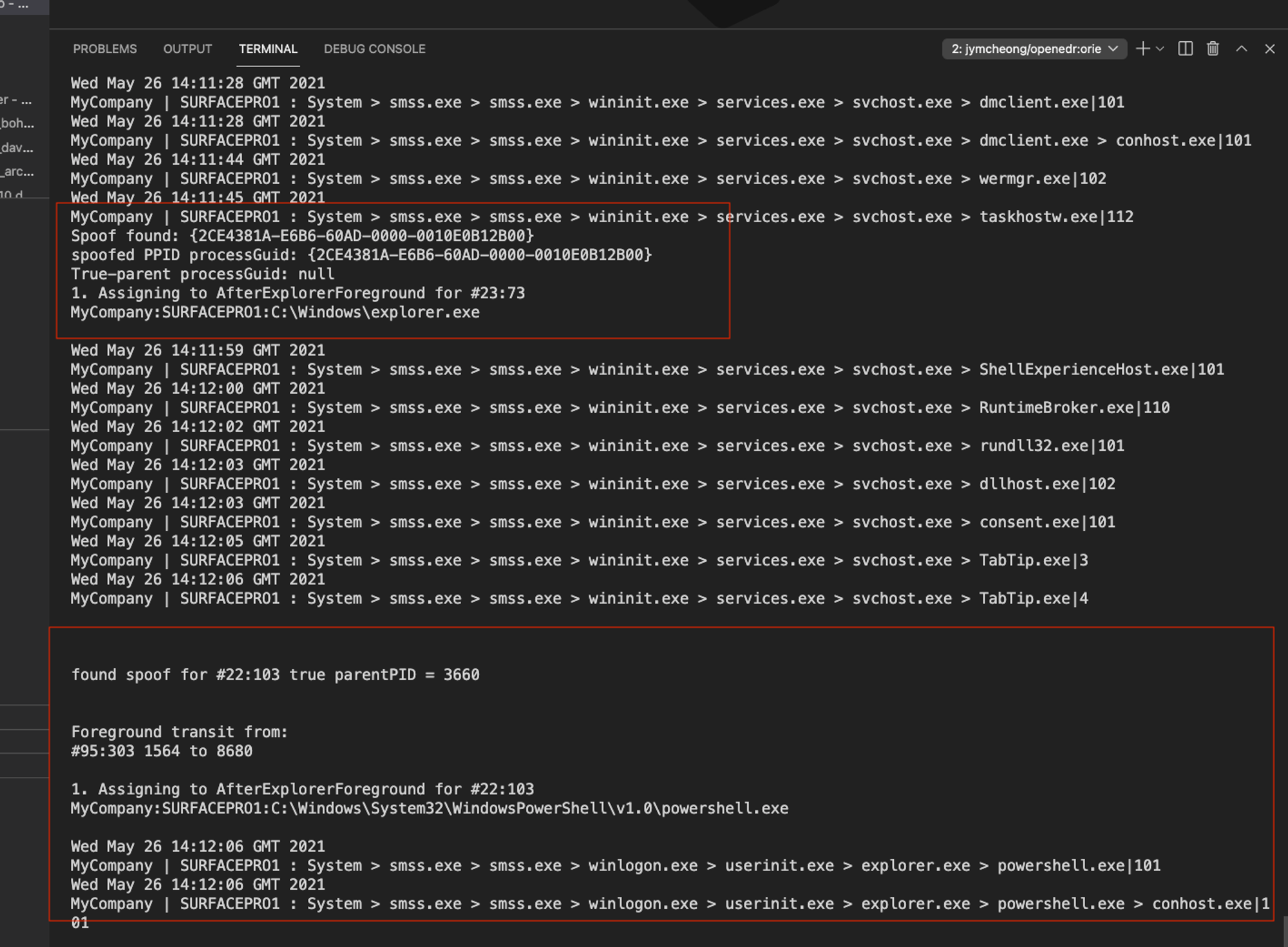
- This is interesting because there could be some edge case(s) in your environment that I may have not considered or encountered before...
May 25, 2021
- SpoofParentProcessId vertex-class-records exist but ALL vertices have no edges out to any ProcessCreate
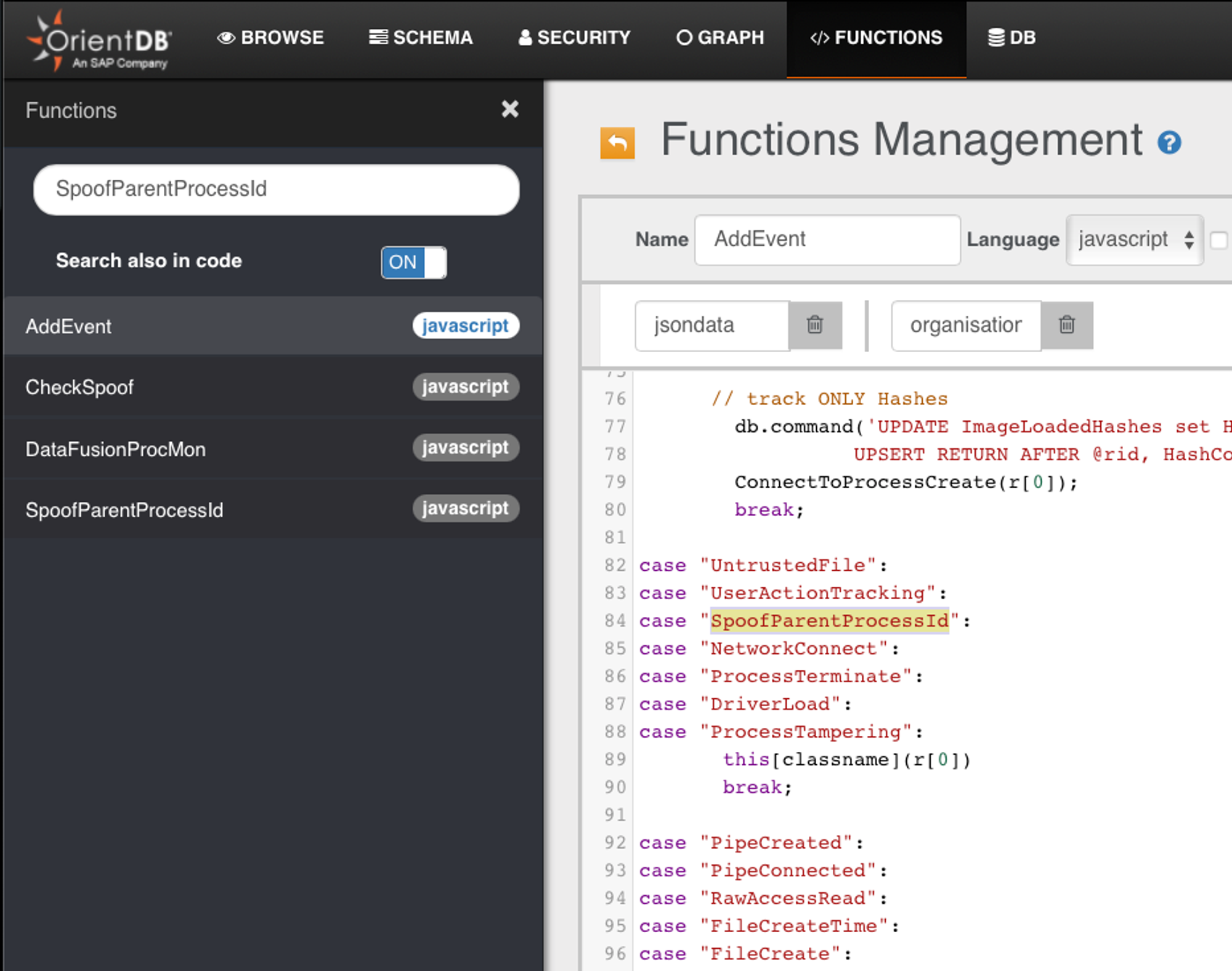
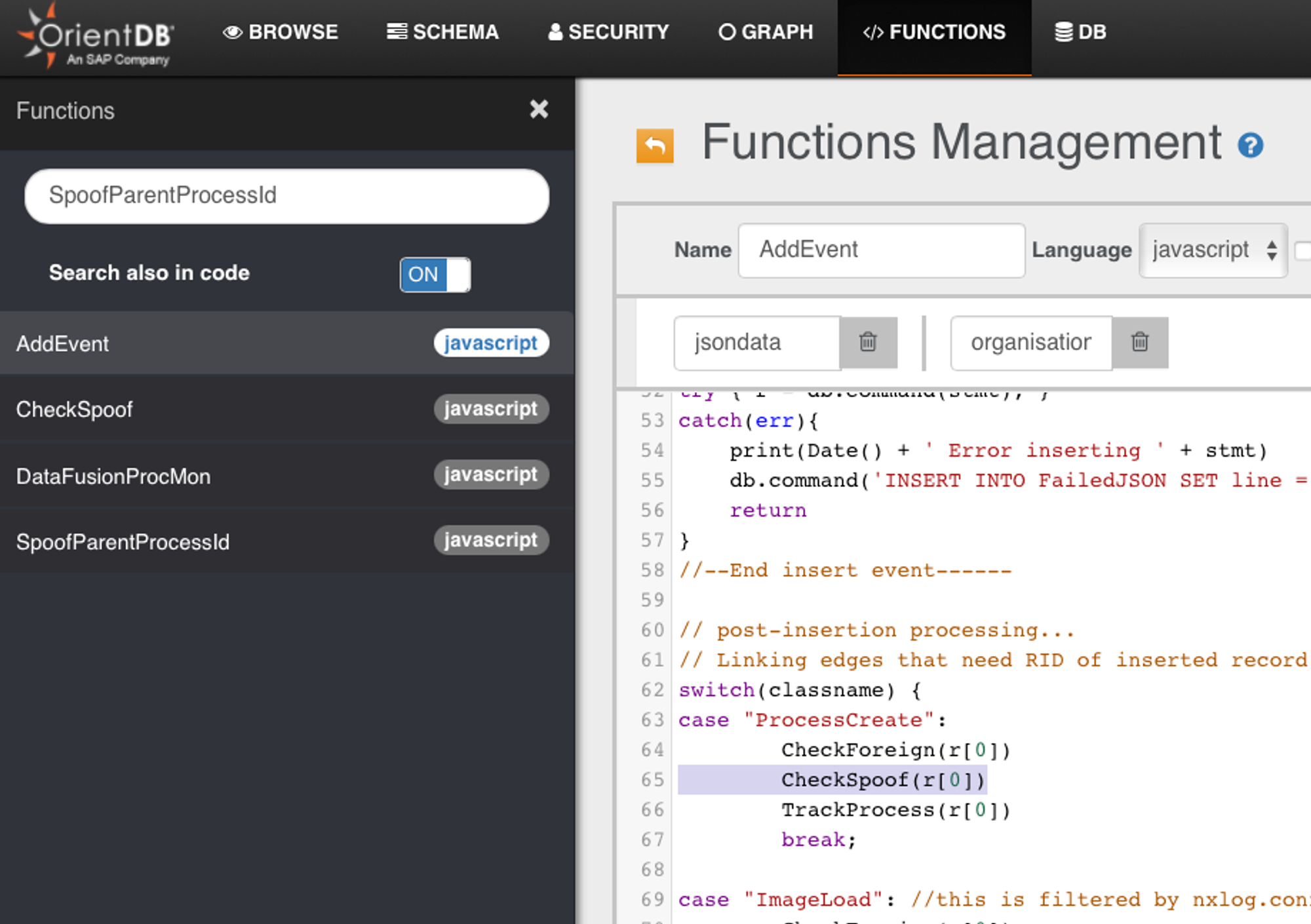
- Using string search, we can see 4 ODB functions are relevant to this vertex class SpoofParentProcessId
- As shared in our IM private discussion, there are 2 scenarios of data flow & it is not deterministic
- SpoofParentProcessId vertex reaches ODB first, then ProcessCreate later
- ProcessCreate first, then SpoofParentProcessId
- On some machines, it is scenario 1, others 2, thus I say non-deterministic
- it YJ's case, both SpoofParentProcessId & CheckSpoof function are somehow linking edges to ProcessCreate
- From your ODB console listing, it seems more like a scenario 1 with the additional fact that TrueParentProcessGuid field is null, which is possible since some early processes that started earlier DFPM.exe, then we can't cache for subsequent look up of ProcessGuid value of a process given its ProcessId
- And if ODB console output does not show a 'found spoof...' when triggering a UAC test case on the target VM, it begs the question what happened to that spoof = db.query... highlighted below, listing of CheckSpoof function:
- CheckSpoof is called by AddEvent; this handles the scenario where SpoofParentProcessId record gets into the database ahead of ProcessCreate
- You also queried & found SpoofParentProcessId vertices, means DFPM.exe is working & Upload.exe transported the event into ODB
- You also took the TrueParentProcessId (that 1180) to query & found a corresponding ProcessCreate, it means the true parent event was ingested
- We are only 9 working-days into your internship (Hari Raya excluded)
- You are year-1, not final year, & you are wearing a user or "analyst" hat to look at things so far.
- It is unreasonable to suddenly get you to switch to developer hat for a system that you haven't dig into.
- This lesson will help out with the OpenEDR enhancement track.
YJ, pls spend some time to investigate since for the offensive track, we will use UACme to study both the structure AND sequence. Thanks!