If you have problem spotting your own attacks, then spotting attacks from others will be harder...
Learning Activities
GoalsBackground
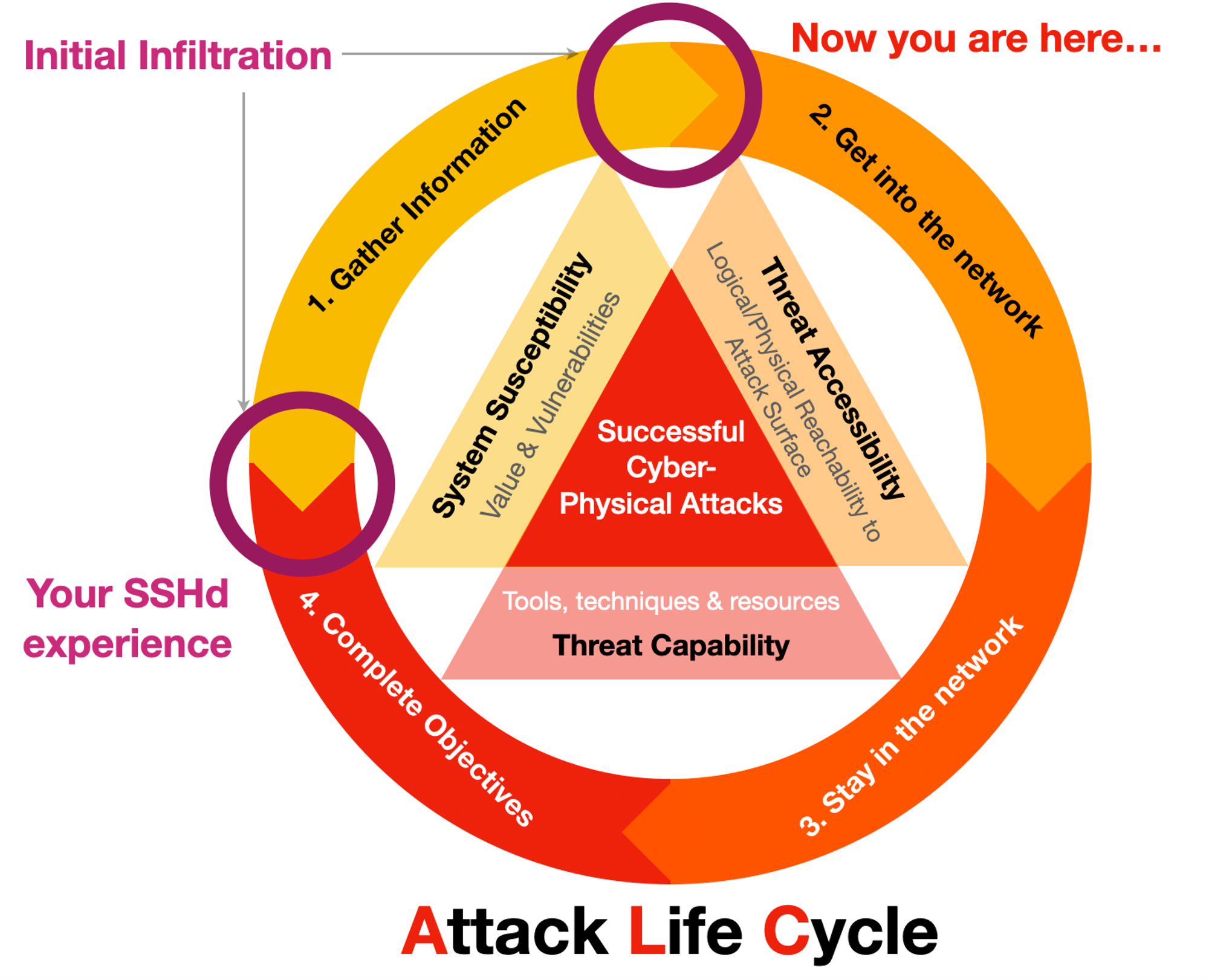
The first track (limiting SSH access) relates to Phase 1 directly to 4, if SSH brute-force succeeded. For server-side misconfiguration, APIs or exposed services vulnerabilities, attackers can quickly complete objectives without going through client-zones. This track lets you experience the longer path to completing offensive objectives.
Key Lessons
- A follow-up from Visual "Normal" Use-Case; help you better find "Wally"!
- If you do not know what normal looks like, it's harder to verify alerts.
- Infiltrations start from endpoints, could be client devices, exposed servers, IoTs & OT-stuff. (MiTMs are more of [3. Stay in the network] problem)
- When you can spot anomalous Code-Execution sequence, those extra sequences that rarely occur with common use-cases like viewing email attachment, then you have better Situation Awareness related to initial infiltration
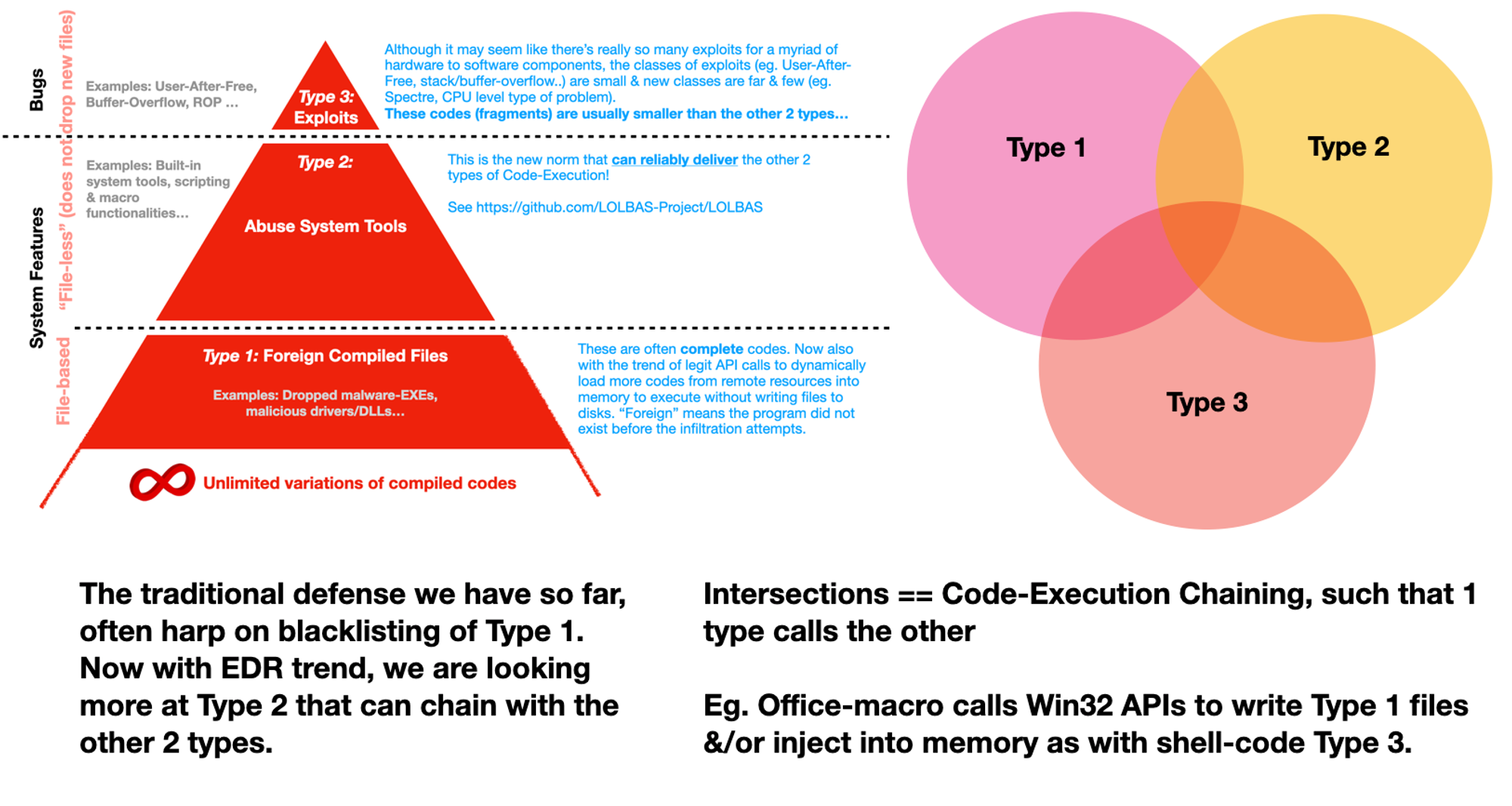
This track focuses on Type 2, what are the system tools, processes & so on within Windows (since we touched on Unix earlier). Concepts equally appl to Unix-variants. See https://lolbas-project.github.io
We focus on Type 2 because if you generate compiled binaries, C2 agents or whatever, you will realize such files will be 'dead-on-written' (instead of arrival). Why? Because DFPM.exe (one of the OpenEDR host agents) will deny read for such Type 1 payloads.
As you progress into various offensive techniques, I will discuss further the detection techniques within OpenEDR.
Why harp on Code-Execution...
When there are so many other offensive tactics & techniques? Apart from eavesdropping (eg. MiTM to steal credentials, tokens, cookies & what not), almost all host offensive tactics require Code-Execution!
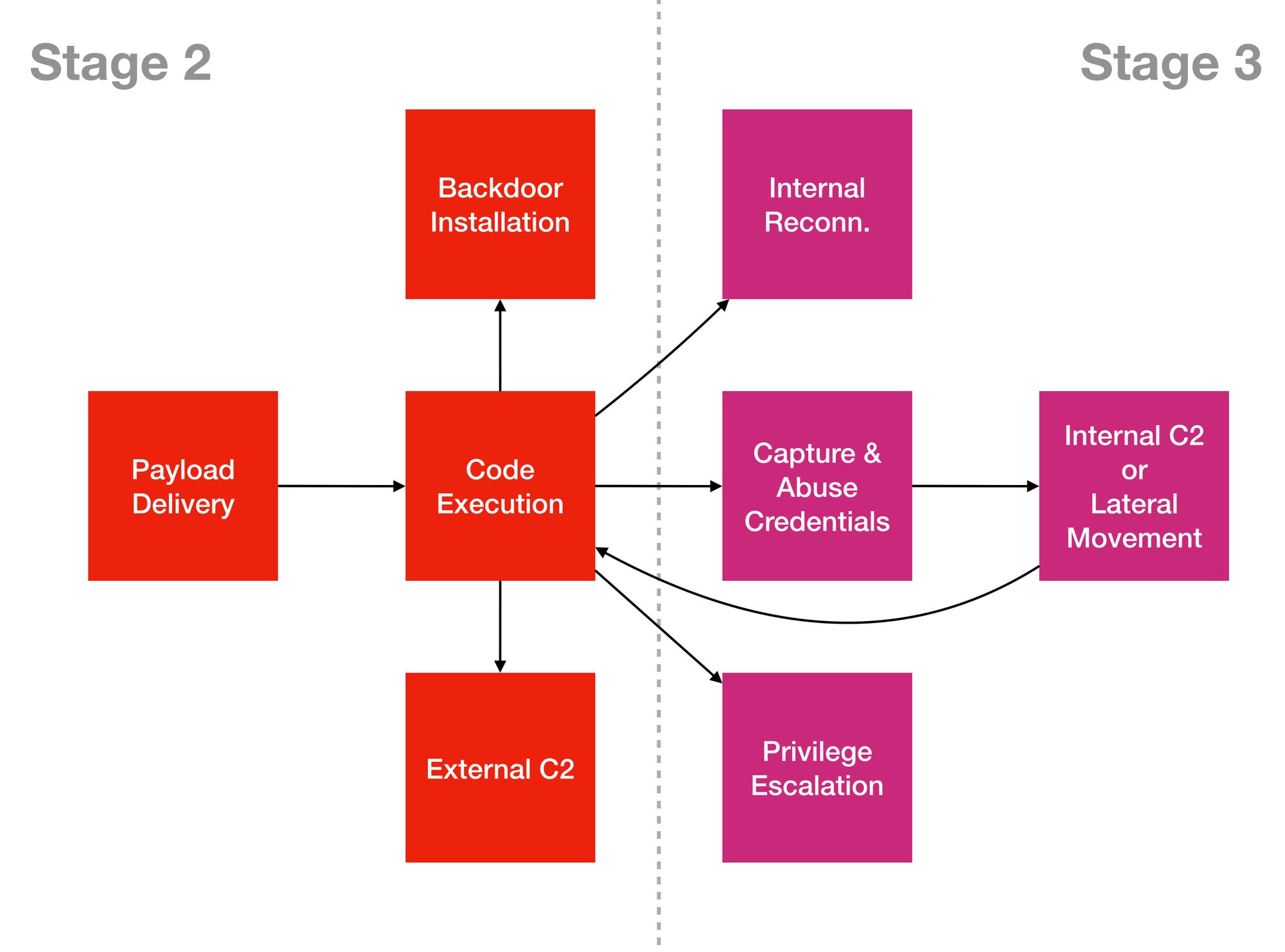
There are many techniques for each tactical area. Students should attempt at least 1 technique per tactical area highlighted above. It has some similarity with MITRE ATT&CK but I developed my mental-models independently. It happens to be similar. We reference it but won't use it with our internal training as there are concerns with copyright issues, e.g. you need to use the full phrase MITRE ATT&CK & not just ATT&CK, plus other meaningless legalities to remember.
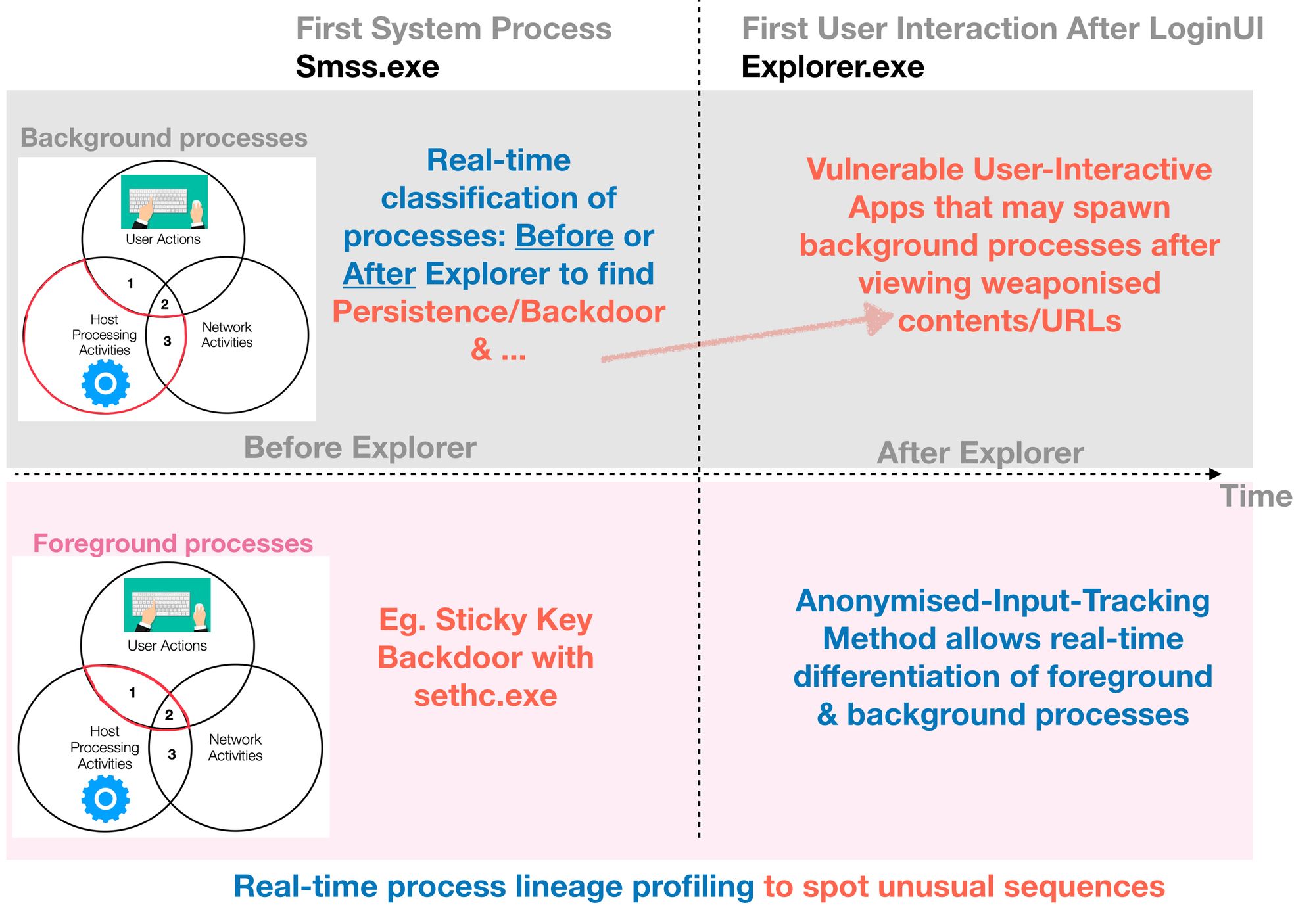
Why Foreground vs Background Process matters?
For many environments, users interact with their OS via some form of Graphical User Interface.
There are also cases of admin scripting & so on, but such scripts execution are typically consistent. Threat Actors can abuse system tools (Type 2 Code-Execution). E.g. Whoami.exe ran by an admin vs a background C2 session driven Whoami command.
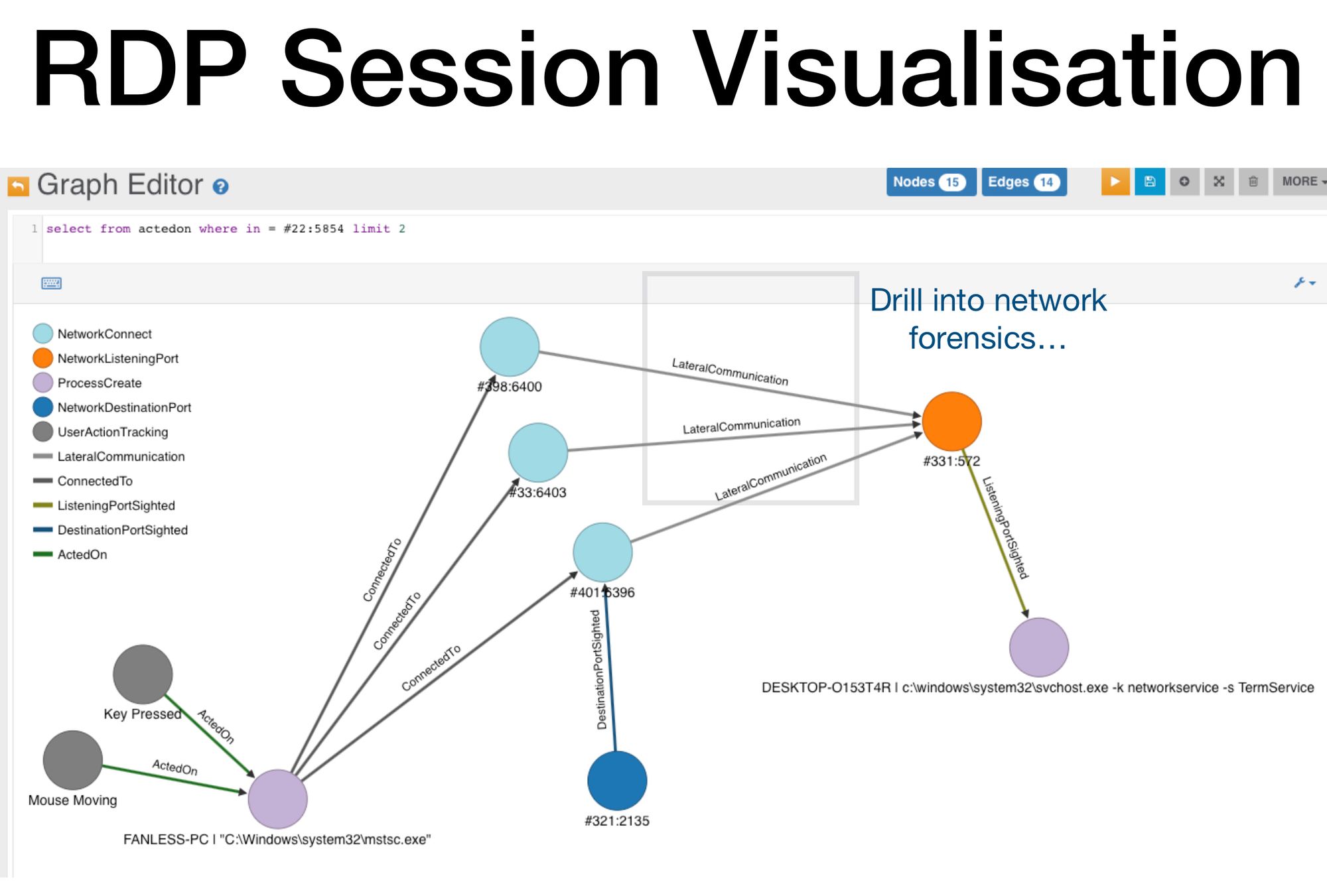
We have an interactive RDP session with anonymized user-actions linked to the left most purple-colored process; a RDP client. But what if a background process is relaying RDP sessions to a remote attacker? What would be the edge-types for that process?
Why bother to label a process with Before/After-Explorer?
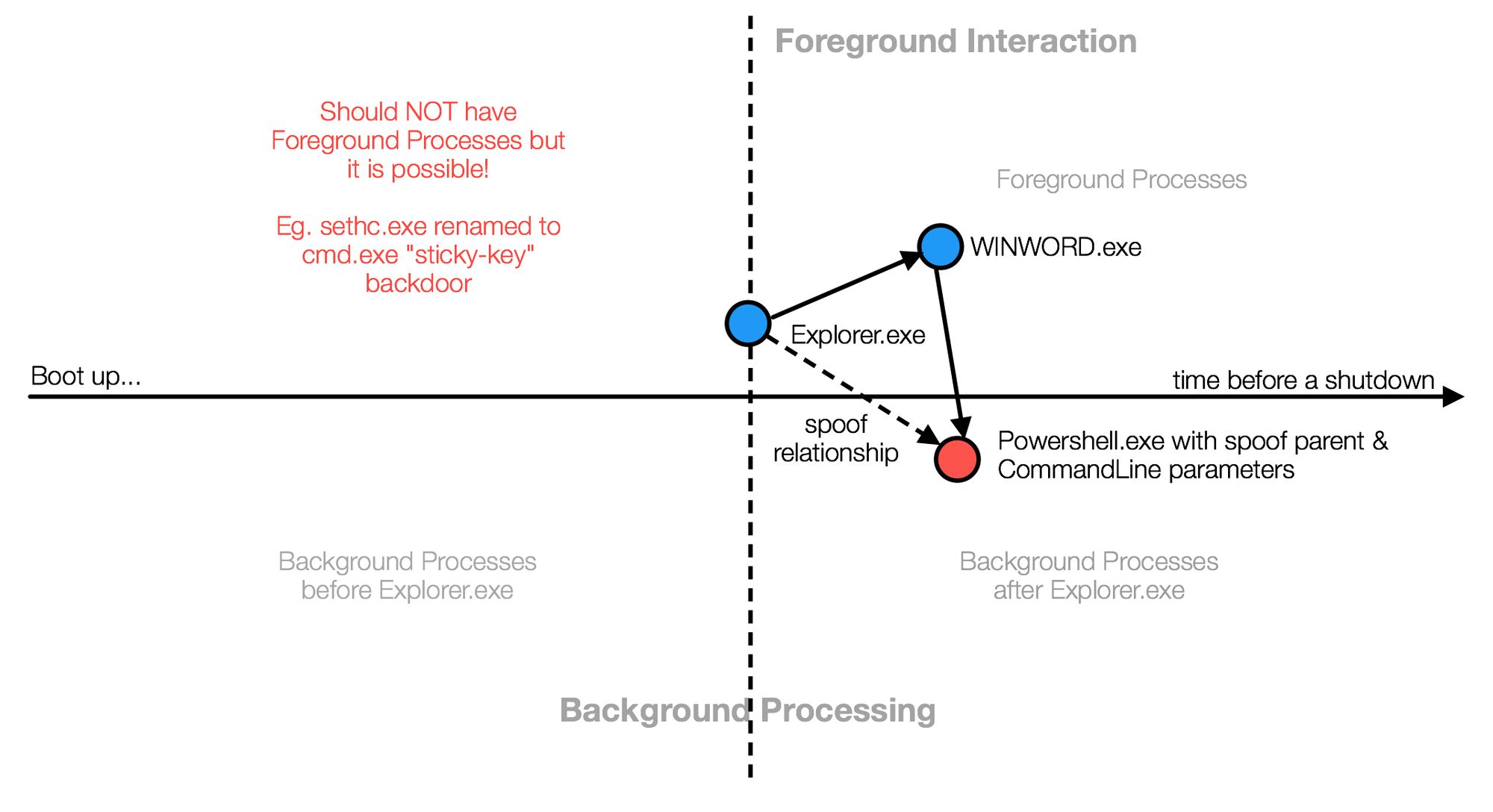
Whenever there is an alert for new sequence &/or commandline anomaly with the BeforeExplorer attribute, we are quite clear that such anomaly could be a case of Persistence or Installed-Backdoor, especially so when the events include network communication with external destinations. However, when it has AfterExplorer, we may want to investigate & trace back as what you did with Visualize Normal...
For instance, YJ did a process-spoofing with office-macro. Most office-documents will not cause such background sequences...
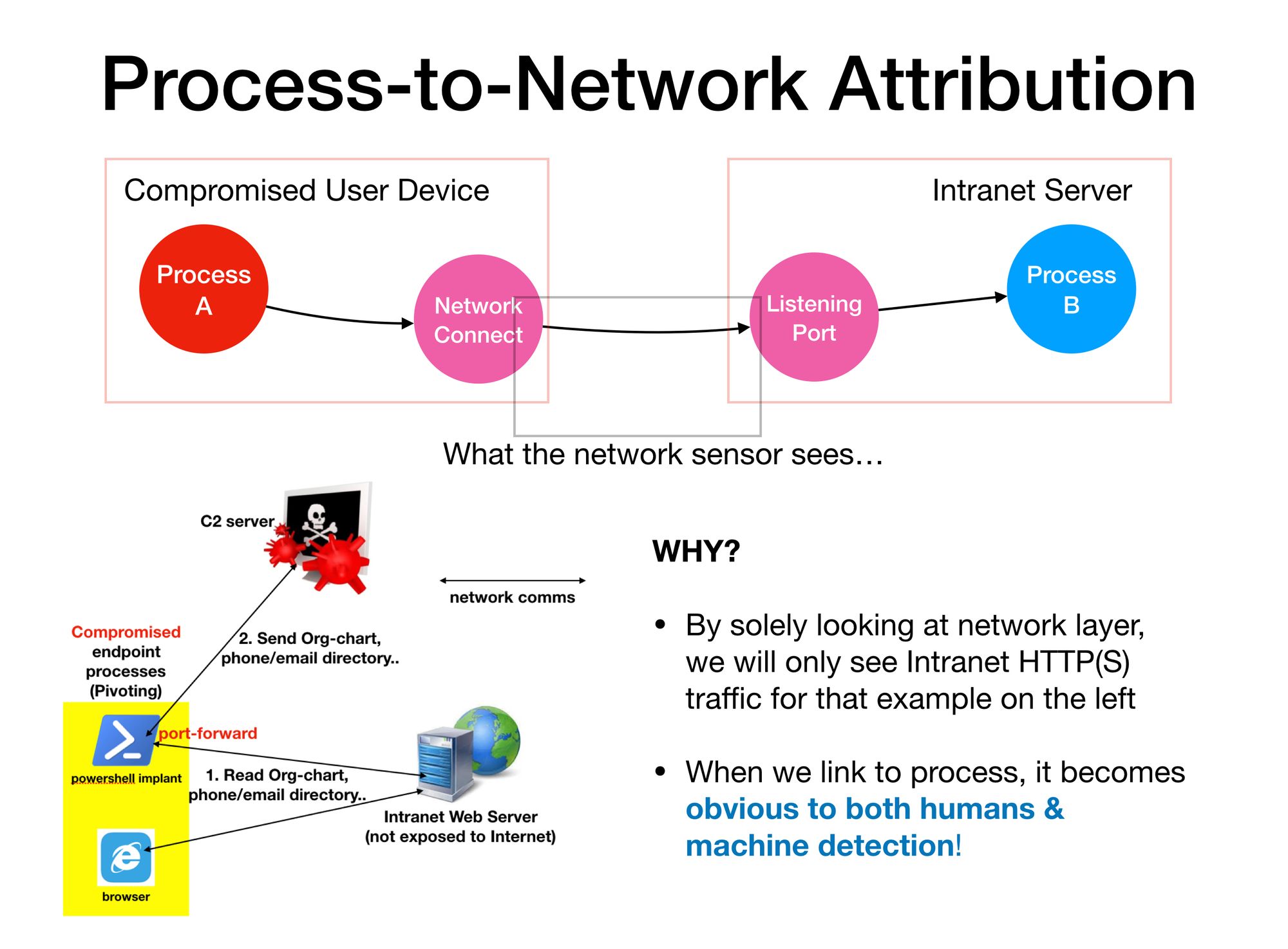
The Problem with "Silo Analytics"
We attribute network activities (link) to processes because we can't really tell solely by looking at network data. Consider the example below. As far as the network sensor is concern, it cannot tell whether it is the Powershell or browser process that is communicating with the intranet server. When we link the network event with process, it becomes clear!
Subsequent tracks of sizing & enhancement of OpenEDR become meaningful to students who experienced 'Normal' vs 'Attacks'. Students are free to install the tools & practice further at his or her own pace & gear.
