Takeaways
- Think like attackers with RINSE Attack Life Cycle model.
- Defend Tactically with Tactics → Techniques → Procedures modeling.
- Disrupt one or more offensive tactics & make techniques related to those tactics irrelevant.
- Defending Tactically lowers your costs & increases effort for adversaries.
WHAT NOT TO DO is a valid strategy
Professor Michael Porter (Harvard Business School) once wrote in a classic 1996 Harvard Business Review article:
The essence of strategy is choosing what not to do. Without tradeoffs, there would be no need for choice & thus no need for strategy.
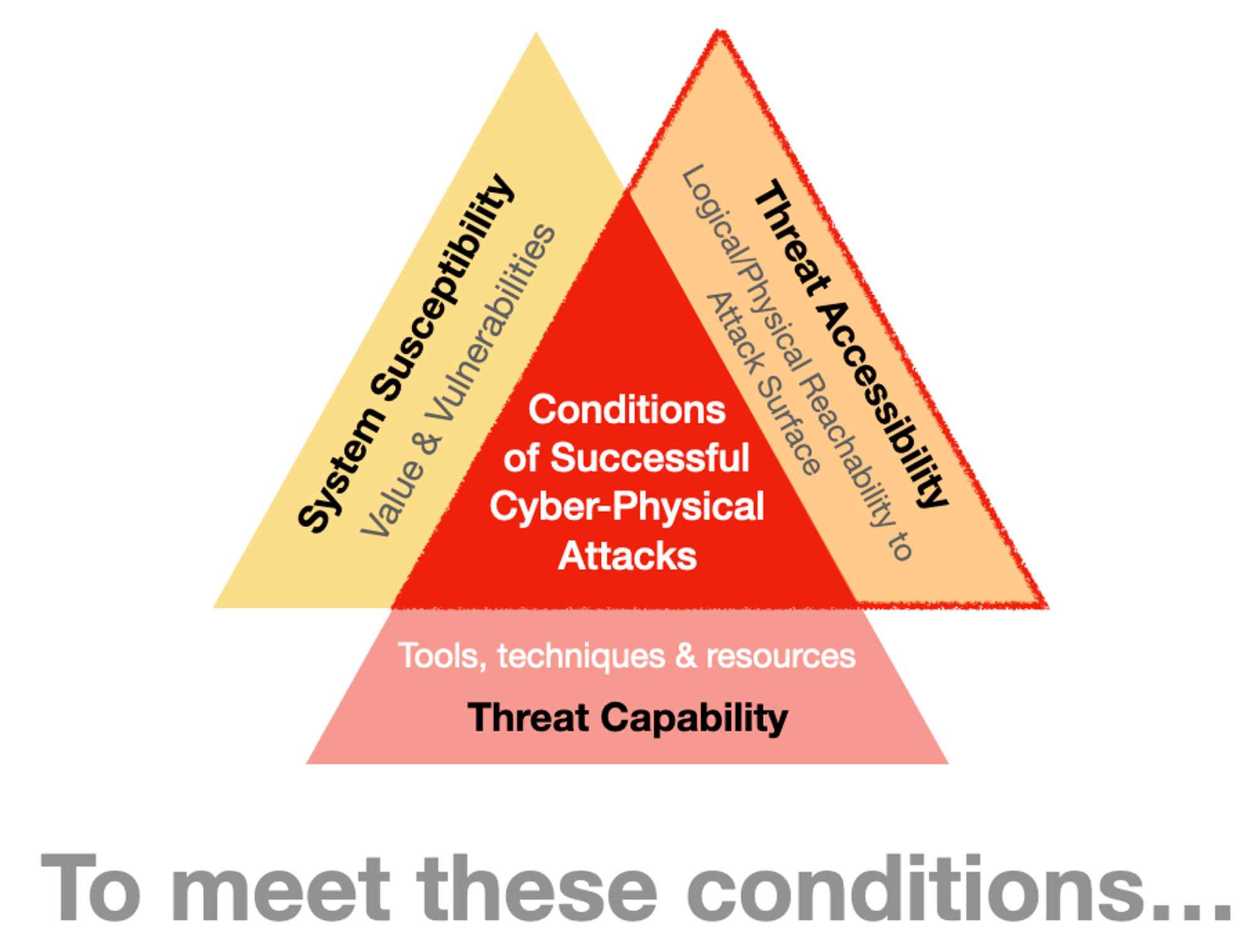
We may have done all the right things (e.g. investment in technical controls, training people to comply to policies & so on), but a single wrong move can nullify all efforts. It is only as strong as the weakest link. Let’s walk through the attack process to see what NOT to do with respect to Threat Accessibility, the “oxygen” of cyber attacks & what do we mean by defending “tactically”.
Think like Attackers
Once again, we revisit the necessary & sufficient conditions of attacks. A quick recap from the 1st part of this series, NUMBER ONE thing you want to do is cut off “oxygen” of cyber attacks; anything related to your systems that Threat Actors can access for their advantage!
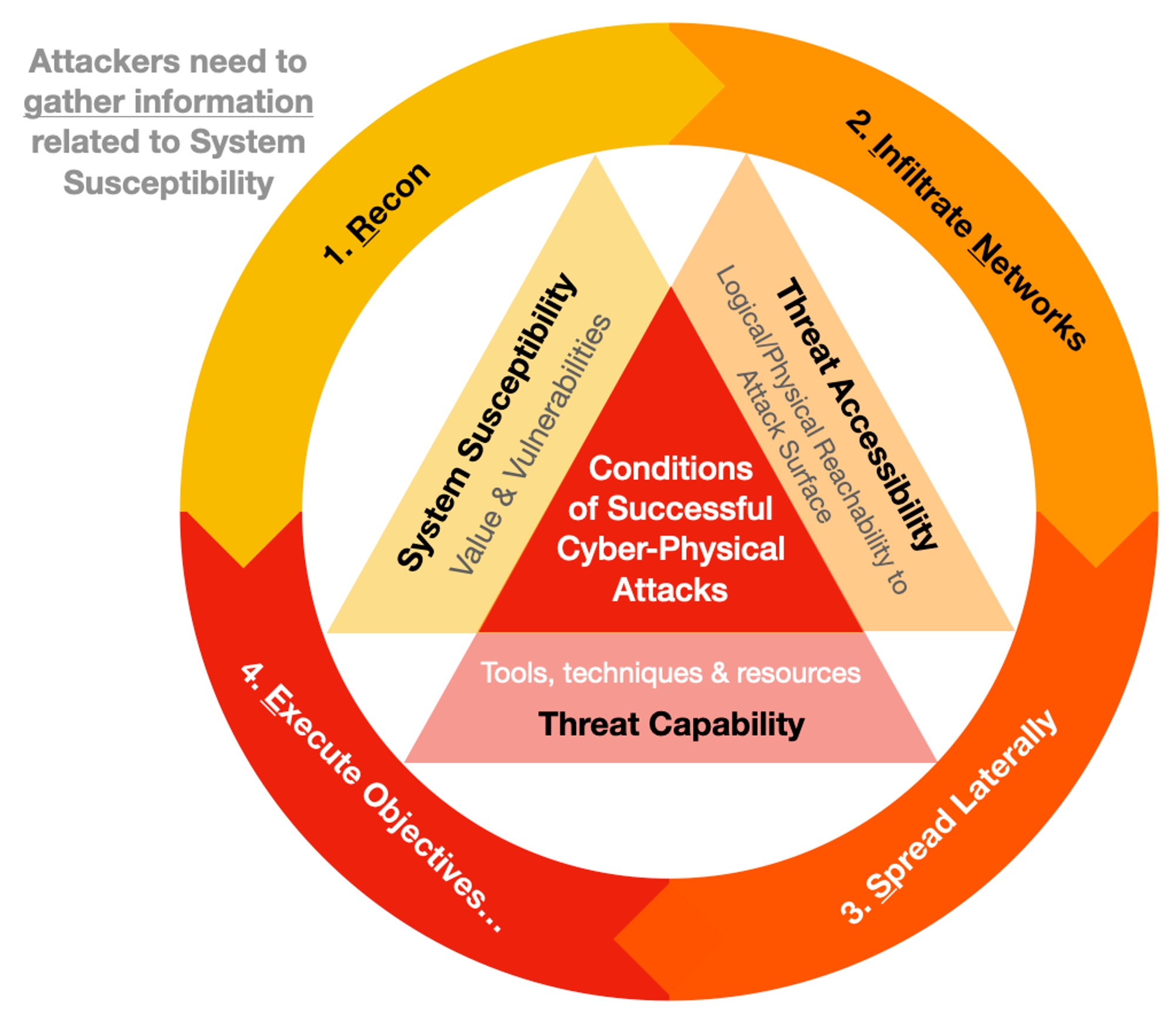
Attackers have to act & the 1st phase will be Reconnaissance, to gather information (establish Value & Vulnerabilities) related to your networks, services & even people.
Examples of low-hanging fruits (for attackers but what NOT to do for us):
- leave sensitive data-sets or secrets in public networks (e.g. cloud storage, code repositories & the likes)
- expose services (especially administrative interfaces) with default permissive settings & passwords
- ignore Information-Disclosure (inclusive of software versions info) findings from Vulnerability Assessment scans (if you are not scanning for your own weaknesses, your adversaries will)!
All the above is a subset of any basic Vulnerability Assessment. I sound like Captain Obvious but it still happens repeatedly.
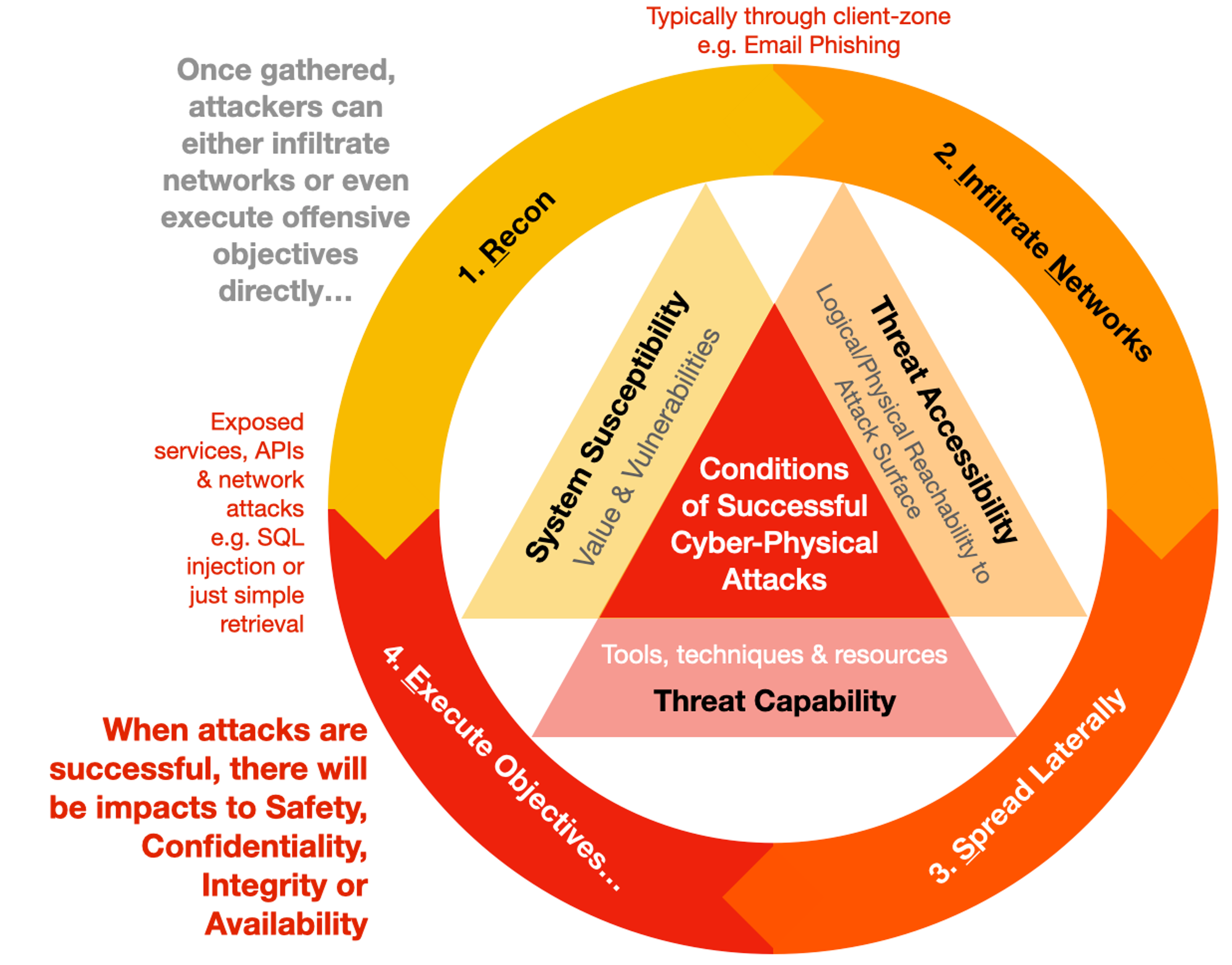
You may often come across the term VAPT or Vulnerability Assessment & Penetration Testing. VA is really more for dealing with Phase 1 to 4, to remove the “low-hanging fruits”. PT attempts to break in AFTER denying (or at least confirmed that a Risk Exposure item has indeed addressed) the easy (or high-probability) attacks, which is related Phase 1 to 2, to be elaborated later. Red Teaming is a more involved process that often simulate the whole attack life cycle.
Why such a high-level view?
Before | After |
Business stakeholders find it hard to follow nitty gritty technical jargons. | Understand the problems & defensive efforts or investments quickly with a Big-Picture mental model. |
Severity “0” is highest... BUT WHY (da f...) use an arbitrary approach that has no basis (just because someone says so)? | Clear logical progression, each phase of attack corresponds to defenders’ severity level. |
Spending & implementing without understanding or ignoring controls due to lack of understanding. | Technical folks who configure networks & even develop software should get the main points quickly, without many pages/hours of “awareness” training. |
Mental bias lead & opinion-based decision making. | Counter mental bias with First-Principles mentality. It’s not always the most sophisticated offensive techniques first.
Occam's Razor & Least Effort Principle: when low hanging fruits are available, it’s just Recon (Phase 1) to Objectives met (Phase 4). |
Why bother to infiltrate when doors are not even lock? Let’s say there are no low hanging fruits, then what’s next for attackers?
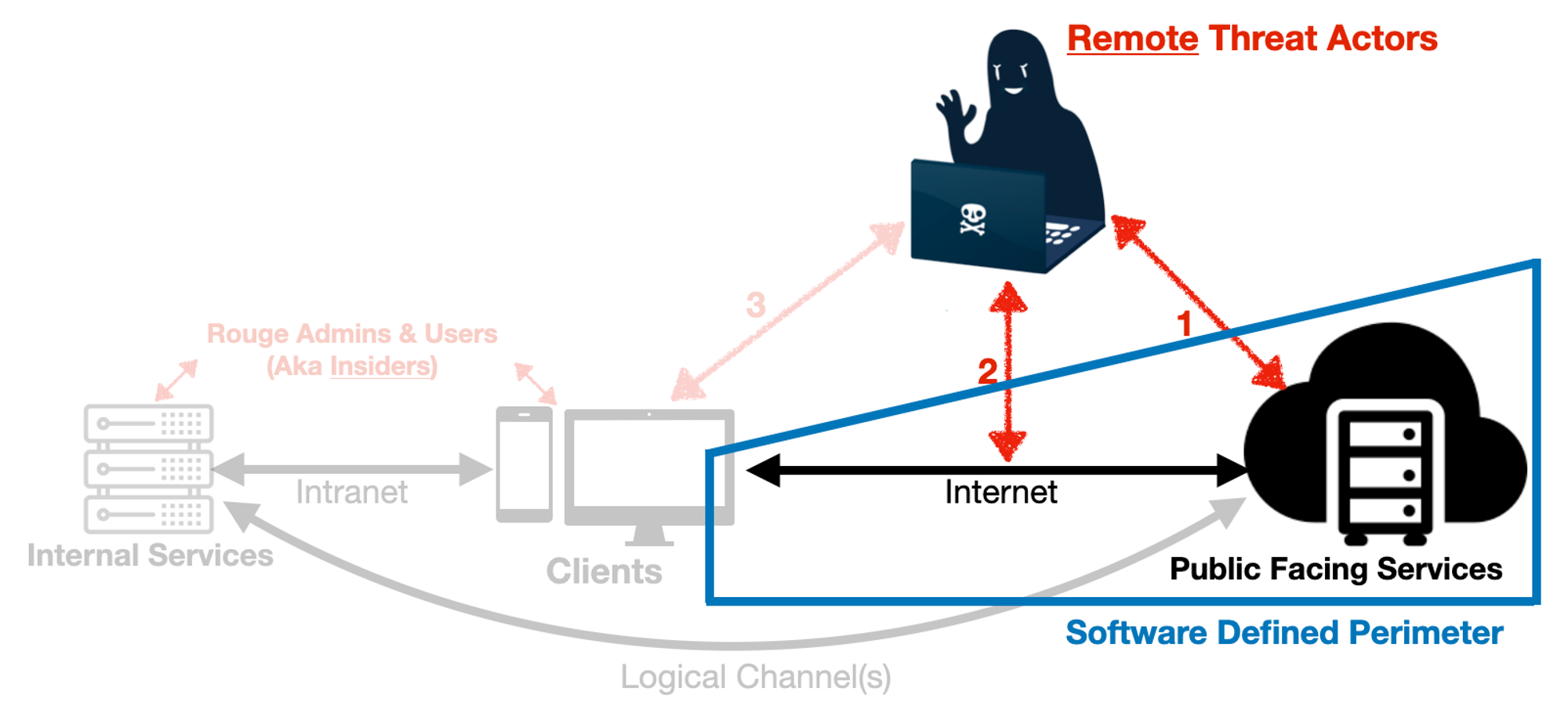
Visualize Threat Accessibility
Even if you don’t invest in Penetration Testing, Threat Actors are going to do it to your networks anyway!
Most networks are essentially connected graphs with 3 main components: logical paths (i.e. network channels & protocols), endpoints & exposed-services (typically via network ports) on hosts (e.g. servers, regardless self-host or cloud-based running some kind of software).
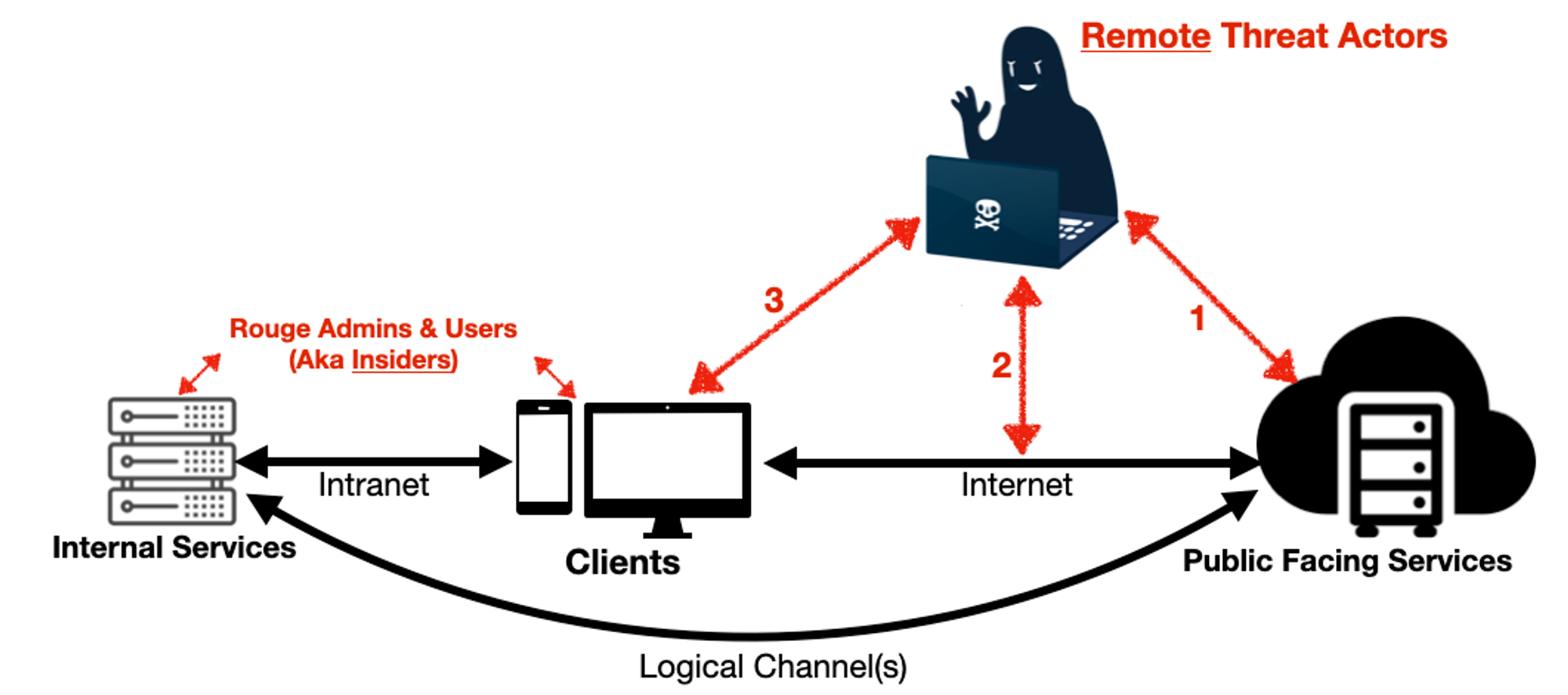
Remote attackers can:
- attack Public Facing Services directly (e.g. scan for vulnerabilities before delivering attacks, it can be cloud SaaS, self-hosted or whatever),
- get in-between users & PFS (e.g. fake login pages to capture credentials) or
- get into client (or any other non-server e.g. IIoT) zones (e.g. send malicious “payloads” via emails, browsers...).
Insiders (including contractors) already have access to various internal networks & services.
Passwords are Liabilities
Password deserves a special mention because it is more a liability than a control to “protect” your systems. It is one of those WHAT NOT to depend on (& often hard to get rid of)...
- Remote Threat Actors (option 1 of previous diagram) can brute-force your services with repeated password attempts (even with Multi-Factor push authentication; see MFA fatigue article), just like my interns’ 1st lesson on Attack Surface Management.
- Intercept data with fake Wi-Fi (think public free hotspots) by getting in between the users & internet services.
- Deliver deceptive messages leading users to fake login interfaces to capture user-IDs + passwords (= credentials), & including One-Time-Passwords (e.g. the Singapore OCBC hack).
Free offensive tools & tutorials are plentiful:
- Evilginx2 - Standalone man-in-the-middle attack framework used for phishing login credentials along with session cookies, allowing for the bypass of 2-factor authentication
- Browser-in-the-Browser Attack: https://mrd0x.com/browser-in-the-browser-phishing-attack/
Cost is an important consideration because it makes little sense for defenders to spend so much time & effort but attackers can pull it off cheaply or even for free.
So let’s assume for now, we removed all “low-hanging fruits” (i.e. no more Phase 1 straight to 4) & added strong authentication to “corner” attackers to Infiltrate (your) Networks...
RINSE (& Repeated) Tactics
During Stage 1, attackers can gather what they can either find online (e.g. run port scans on Internet &/or find out who are your system-admins?) or offline (e.g. Mr Robot style...) then attempts Phase 2:
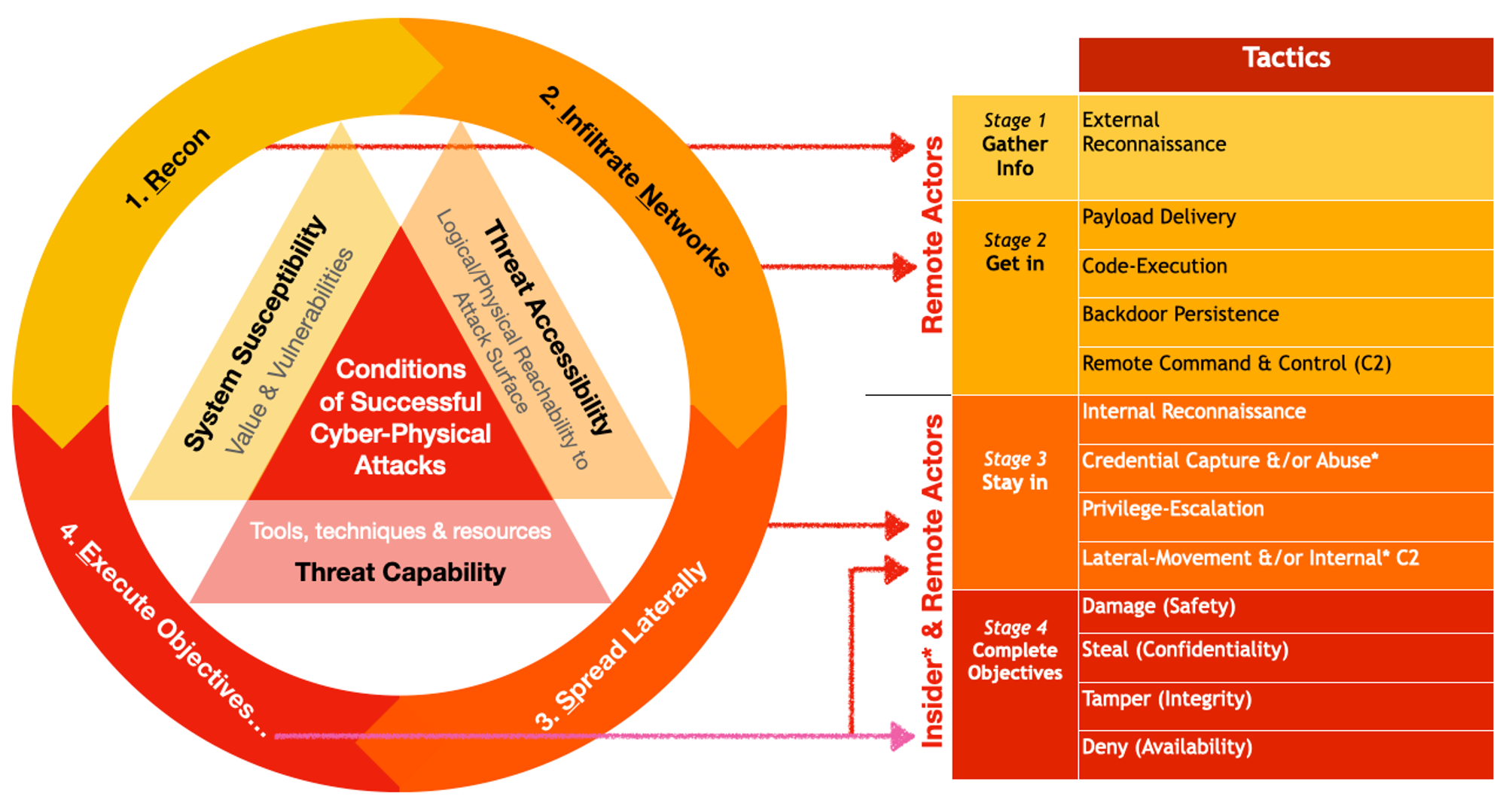
I will explain why each associated tactic is “necessary” in the sense that disrupting any one tactic will impede the progress of that phase. There are other offensive tactics not listed here, but we are concerned with the “common denominators”.
Tactics | What is it? | Why is it necessary? |
Payload Delivery | In military speak, a payload refers to the bomb load (e.g. a missile warhead) of a weapon system.
For logical systems, apart from Something-in-the-Middle that intercepts at the network layer & not within devices, everything else on computers need codes to run. | When the target systems cannot receive any malicious codes, nothing “bad” runs.
|
Code-Execution | Tactics are just sub-objectives needed to reach main objectives. Code-Execution deserves a mental model on its own & I will discuss it in the final part 3 of this series. | ALL other tactics (sub-objectives) require this on any computer-based systems. |
Backdoor for Persistence | Backdoors added ahead of attacks or added after infiltration. It provides remote attackers ways to get deeper into targeted networks. | Let’s say attackers gained Command & Control (or C2) remotely but did not add a backdoor, what happens to the remote control when the system reboots? C2 lost!
Which is why for attackers’ sessions to resume, the remote-control(s) must be persistent to survive system restarts, sometimes > 1 for redundancy. |
Remote Command & Control (C2) | A means to issue commands from a remote entity to the target device. Think TV remote control. 3 components: the remote, near-infrared as communication channel & TV as the target. | Without remote C2, a Threat Actor who is not physically present (as oppose to an Insider who has Internal C2) within the network, cannot control targets. |
Internal Reconnaissance | Gathering information from within yields what you won’t usually find from public networks. | The first target may not be the actual target, but a stepping stone or pivot. Even when an attacker were to have a network map (e.g. from collusion), gathering information from within is still essential to figure out the territory (”the map is not the territory” & adversarial OODA loop). |
Credentials Capture or Abuse | Remote Threat Actors have to capture but Insiders can abuse access that is already given. | It becomes hard to tell when Threat Actors are adept at blending in with captured credentials & using sanctioned system tools. Which is why a dedicated section on Passwords are Liabilities.
Passwords are weak secrets that are cheap to capture. |
Privilege Escalation | To gain elevated access to resources that are normally protected from an application or user. | Offensive Objectives require it. For instance, super user rights give attackers access to data or functions that are not accessible to standard user (i.e. attackers’ initial access rights).
Threat Actors with escalated rights can wipe digital evidence & even plant false-flags. It leads to the last necessary tactic... |
Lateral Movement or Internal Command & Control | Remote Threat Actors have to spread laterally (after Internal Recon), traverse connected networks to reach intended targets. Insiders already have internal C2 over the targets.
An example of “spreading” laterally would be along pivoting the first compromised host or device that is remotely controlled to deliver payloads to the next target, thus RINSE & repeat...
Another form of Internal C2 is when a compromised host or foreign implant acts as a pivot point (or proxy) for a target that has no means to communicate to Internet. | First compromised device may not be the actual or final target.
Methods to differentiate Threat Actors early is not a nice-to-have but necessity. |
Tactics → Techniques → Procedures
When we visualise tactics like a dependency graph, it looks like this:
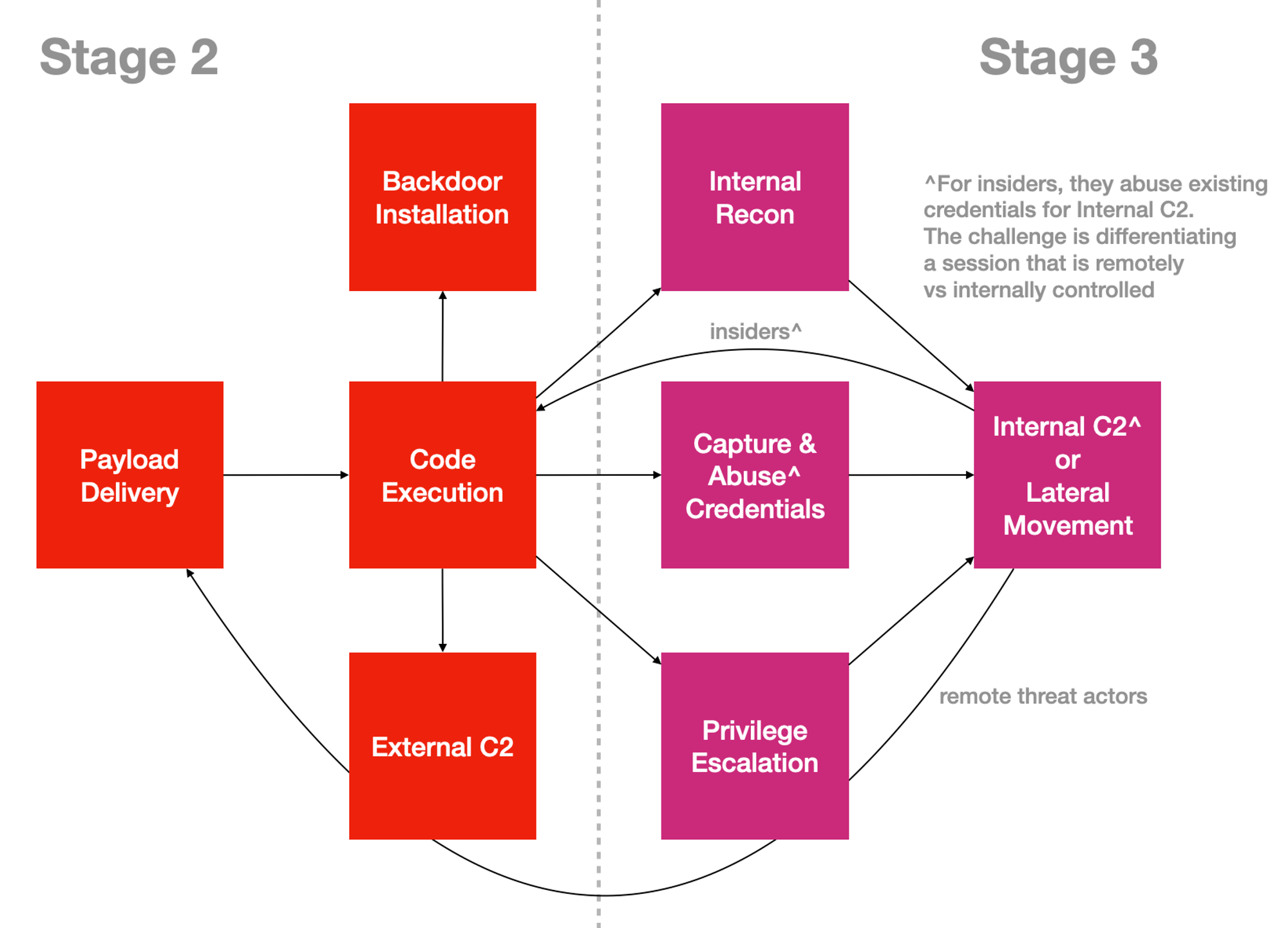
To meet a sub-objective (tactic → what), attackers need methods (techniques → how to... that are specific to technologies & systems) executed in certain sequences (procedures → when to do what, like a flow-chart) to achieve intended outcomes.
Code-Execution is critical since all other tactics need (or depends on) it. The final part of this Mental Model series will drill into my Code-Execution mental model that I used to design & implement Free Endpoint Defense & Response.
TTP modeling is necessary for better defense. There are other models like MITRE ATT&CK®, Lockheed Martin’s Cyber Kill-Chain®, Mandiant Attack Life Cycle & so on. RINSE Attack Life Cycle model is just one of them, which I am explaining why it is the way it is.
Defending Tactically?
From the diagram below, you can see that there are lots of grounds to cover even with a minimal set of tactics. Defending tactically deals with problems early with fewer resources!
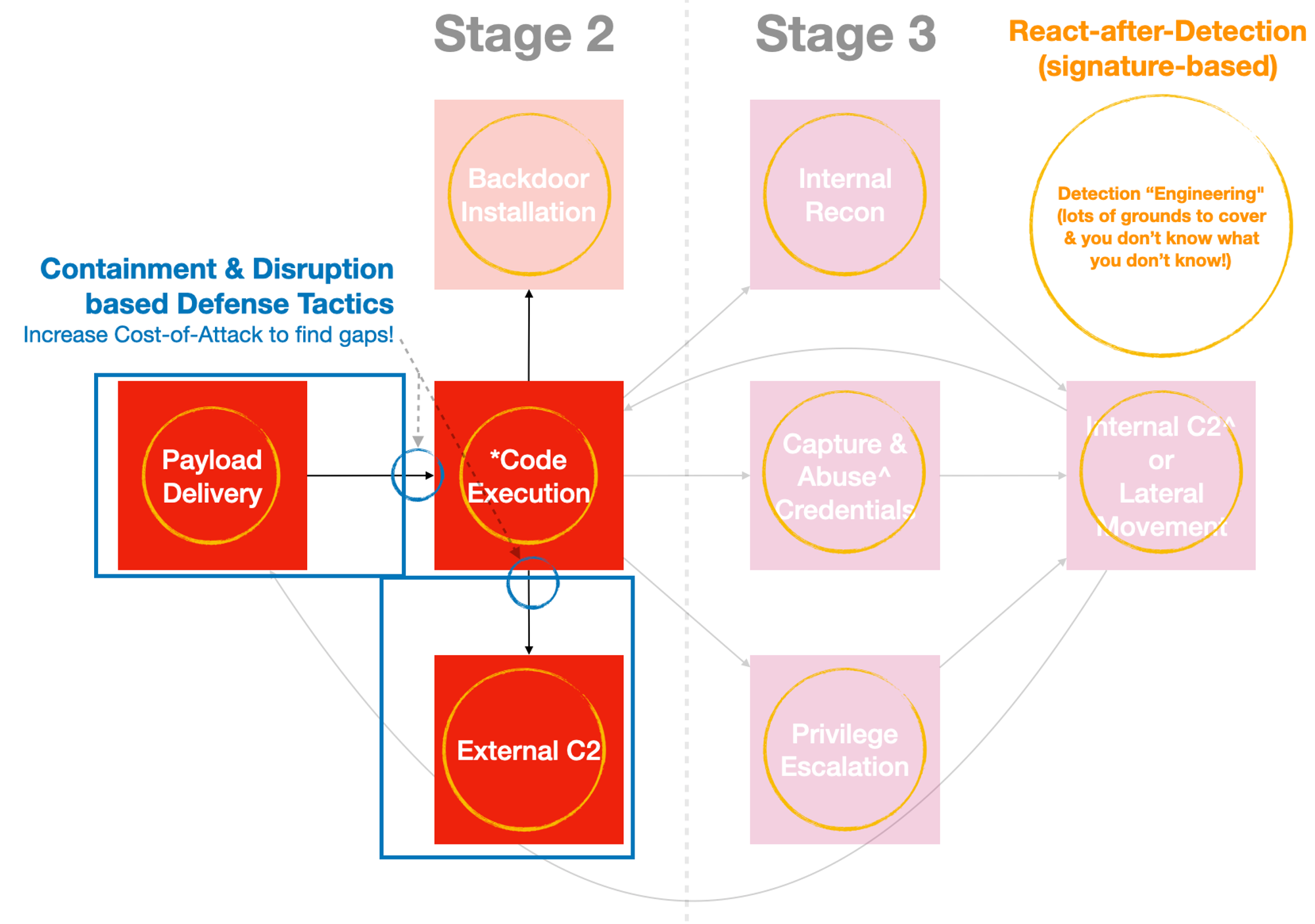
Defending tactically reduces the problem-scope & increases cost-factor for attackers because they have to spend more time (& money) to figure new ways (instead of easy rinse-&-repeat → profit) to get in (e.g. come up with new tactics & techniques, as oppose to reusing free public offensive tools).
A React-after-Detection posture attempts to figure out what are in the boxes (techniques for that tactic), but defending tactically disrupts the paths between tactics. You discover new techniques when they are disrupted!
I will just illustrate disruption to two important tactics related to network layers in view of not overwhelming the reader. Let’s use the RINSE model starting from the low hanging fruits...
Phase 1 to 4 - Low Hanging Fruits

Earlier in part 1, I shared the 1st lesson on Attack Surface Management that my interns took. They saw relentless brute-force attempts immediately after bringing SSH service (on someone else’s computer) live on the Internet. After re-configuration to receive connections only within a VPN network, no more brute-force events. That’s a basic example of denying Threat Accessibility, the “oxygen” of attacks. For such a scenario, what’s next for the attackers?
In Q1 2021, there was a 1,916% increase in attacks against Fortinet’s SSL-VPN and a 1,527% increase in Pulse Connect Secure VPN. No surprise since work-forces all over the world are working remotely thanks to COVID.
VPN servers like any other online services, need to expose ports to receive connection requests. The most glaring problem of traditional VPN is having access to the whole Internal networks once attacks targeting services’ vulnerabilities are successful. Flawed VPN clients become a means to escalate privilege on victims’ terminals.
Threat Accessibility basically shifted away from exposed app-services &/or infra-layers, to specific network or app services (VPN in this case). Software Defined Perimeter addresses short-comings of traditional VPNs. You can find out more about SDP with this link, but I will only highlight one key feature, that is to cloak (aka “black”) networks. Another mature protocol has been around since 2015; Host Identity Protocol achieves the equivalent.
Tactics | Conventional Controls | Defending Tactically |
External Recon | For self-hosted services (regardless cloud or on-premise), you could remove software or service version disclosures, but you may not have control over certain cloud services for this area. | Software Defined Perimeter has no listening ports. Sending attack payloads directly to network service is much harder (to shoot what you can’t see).
Attackers’ next move? Figure out who can access the “black” networks. |
Phase 1 to 2 - Getting in...
Let’s say attackers figured who to deliver payloads to (e.g. with emails)...
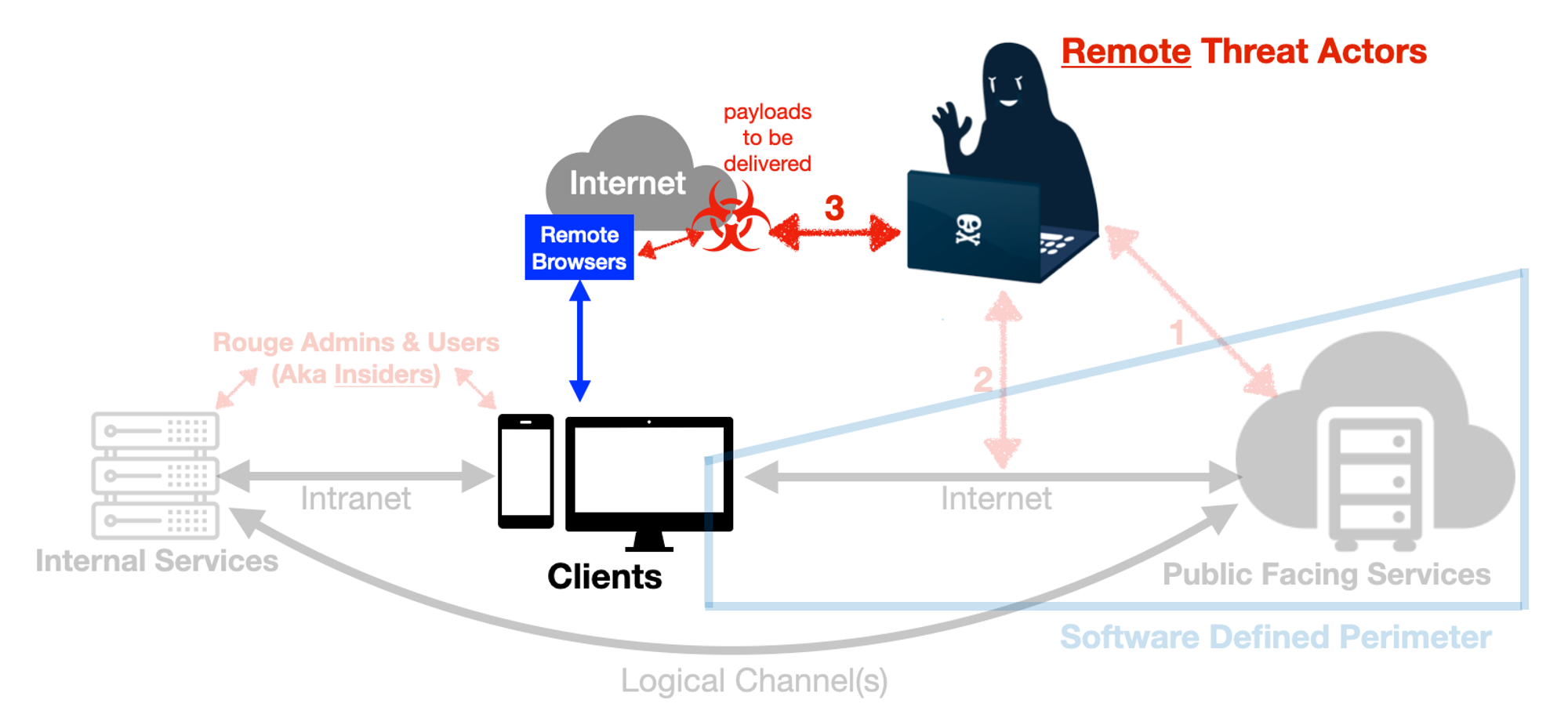
Tactics | Conventional Controls | Defending Tactically |
Deliver Payloads | Web-App-Firewalls, Firewalls, email scanning... just to name a few but with deceptive email messages & encrypted files, payloads usually get through.
Hope to achieve 100% “Don’t fall for it” phishing exercises... good luck!
Not sure if it is fair to always blame users as the weakest link when the networks, software & tools are flawed to begin with. | Let’s say the deceptive email gets to the target audience, target clicks... The payloads however, will just end up within the Remote Browsers that are running within transient container sessions, disposed after each use.
Some Remote Browsers service also warn phishing attempts upfront & stops users from typing in credentials.
I am not selling Remote Browsers here, just illustrating the point that a broad array of techniques related to email & browser offensive methods become irrelevant. You now spend budget on specific intelligence related to containment escapes & any C2 methods over Remote Browsers. |
Code-Execution | Anti-Virus, Endpoint Detection & Response...
Tools to generate payloads that bypass these controls are essentially free on the Internet.
“Threat Researchers” are also kind enough to share detailed tutorials & know how, but who acts on such info faster is a better question? | For the final part of these series, I will explain how Code-Execution can be disrupted tactically. But for the sake of discussion, let’s say employees pick up some free USB storage, got curious with certain files within, malware/trojan-horse RUNs & attempts to call home to remote C2 server! |
Remote C2 | Web-proxies, Firewalls, signature, heuristic, AI/ML or whatever “i-am-going-to-figure-out-bad” based network sensors...
Cheap to bypass with network layer with encryption (e.g. Let’s Encrypt free certs). | Suppose network configuration is restrictive, such that the client zone can only reach out to Remote Browser service at specific network ports. Attackers’ preferred C2 channel (e.g. over Internet TLS/SSL) to call home to remote C2 servers is disrupted.
I’m not saying it's perfect or problem-free. For instance, a loop hole could be DNS resolutions on the client devices were not restricted such that attackers can tunnel out of the network.
This is what I meant by “problem scope reduced”, as oppose to worrying about C2 command-verbs/behaviors, spend money to decrypt-to-detect then re-encrypt & all that fragile & expensive controls. |
React-after-Detection vs Defending Tactically
Networks that have huge attack surface will always be undefendable. Managing attack surface tactically is the way to go.
React-after-Detection | Defending Tactically |
Low-hanging fruits that let attackers start from Phase 1 to 4, like a walk in the park. | Can’t reach vulnerabilities directly, even if credentials were to be captured. |
Expensive to keep up with known & unknown techniques, either you never figure out or figured out attacks much later. | Attacks denied early. |
Cheap (almost free) to attack conventional controls. | Adversaries forced to spend more time & money to mount attacks. It will still be a cat-&-mouse game, just that the longer but sustainable cycle will be in your favor. |
What’s Next
For the last part of this series, I will explain how my Code-Execution model helped me designed a Free Endpoint Defense & Response solution to disrupt this important tactic that leads to all other tactics.
Want to learn more? Check out https://www.jym.sg/cyber-security-in-7-weeks
